FQDN-Based Rules
Applications across datacenters and cloud environments are responsible for a vast amount of east-west traffic. This traffic is the result of communication between workloads, including bare-metal, virtual machines, and containers. However, many applications might need to communicate with services, such as SaaS, PaaS or external registries. These services are coupled with an IP address but that address might be unknown or the services might only be reachable by a URL because their IP addresses are frequently changing. This situation introduces a challenge to security teams because security policies are based on IP addresses or subnets. Administrators can allow outbound communication to any workload or to a broad range of IP addresses to overcome this challenge; however, this approach opens a security gap. To resolve this challenge, Illumio has added FQDN-based visibility and enforcement to its Illumio Core.
Create Policy Objects for FQDNs
IP List
By default, you can leverage IP lists to describe IP ranges, groups, and subnets. From the 19.1.0 release on, you can use IP lists to describe FQDNs.
You can use the previous example (us-west-1.ec2.archive.ubuntu.com) to create an IP list for FQDNs:
From the PCE web console menu, choose Policy Objects > IP Lists.
Click Add.
Enter a name (can be a custom name).
In the IP Addresses and FQDNs field, enter one or multiple FQDNs (wildcards are supported).
Click Save.
Provision the changes.
Based on the example above, these methods of describing the specific FQDN are supported or unsupported.
Supported
us-west-1.ec2.archive.ubuntu.com
us-west-1.ec2.*.ubuntu.com
*.ec2.*.ubuntu.com
us-*.ec2.archive.ubuntu.com
The syntax below is supported; however, it does not describe the FQDN in the example.
ubuntu.com
*.ubuntu.com
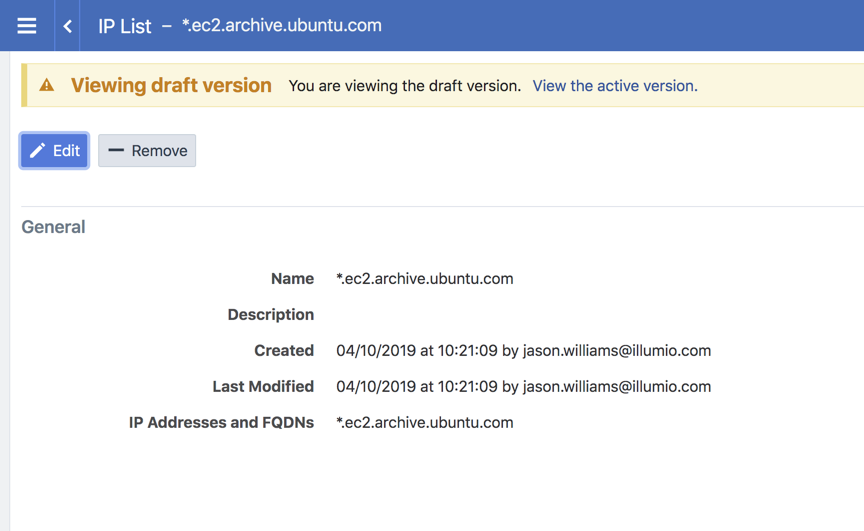
You can use a wildcard in the IP list, such as *.ec2.archive.ubuntu.com as shown below.
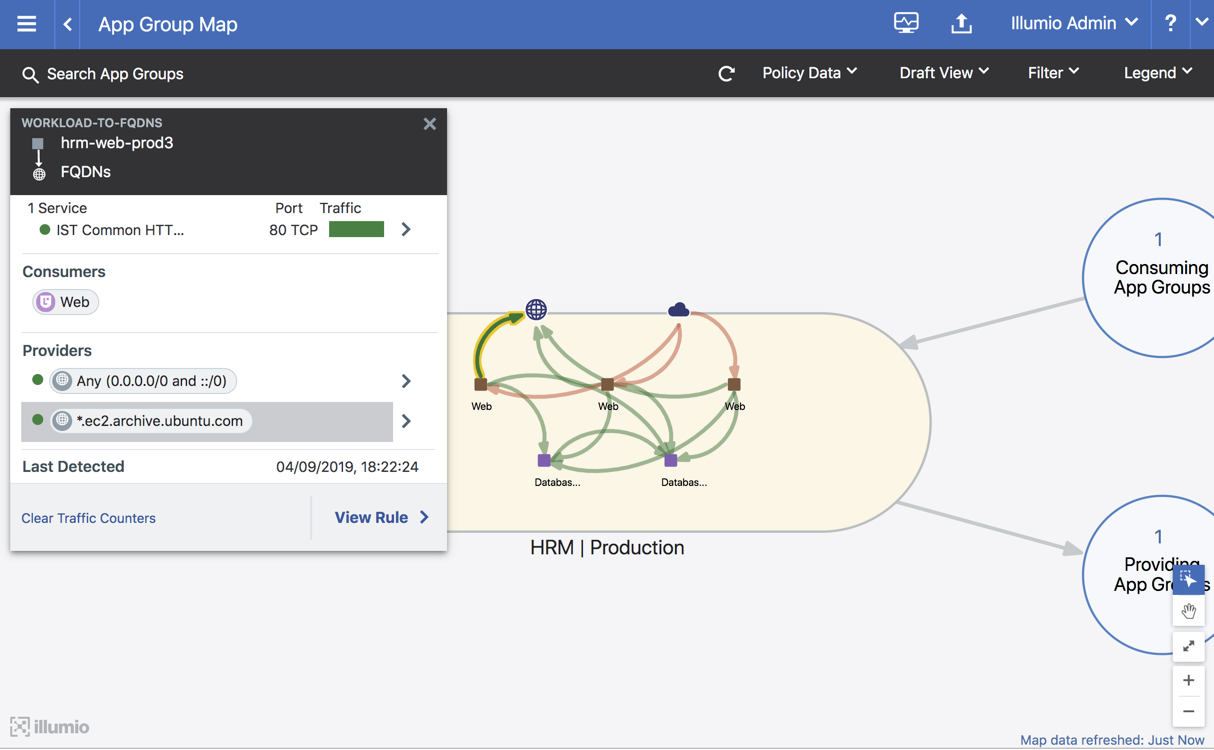
Example of the traffic in Illumination:
Virtual Service
When you have created an IP list to describe the FQDN, you do not need to create a virtual service to describe the same FQDN.
You should only create a virtual service for an FQDN when you do not want to create an IP list:
From the PCE web console menu, choose Policy Objects > Virtual Services.
Click Add.
Enter a name.
Enter a service or port.
Enter your R-A-E-L labels for the FQDN.
Click Add FQDN and enter an FQDN.
Click Save.
Provision the changes.
Based on the example above, these methods of describing the specific FQDN are supported or unsupported.
Supported
us-west-1.ec2.archive.ubuntu.com
us-west-1.ec2.*.ubuntu.com
*.ec2.*.ubuntu.com
us-*.ec2.archive.ubuntu.com
The syntax below is supported; however, it does not describe the FQDN in the example.
ubuntu.com
*.ubuntu.com
This example of a virtual service represents *.ec2.archive.ubuntu.com.
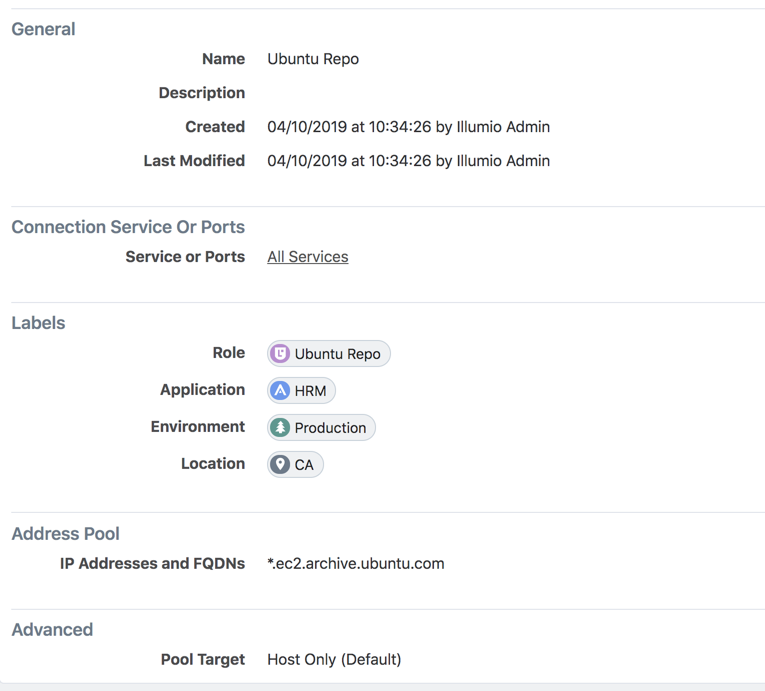
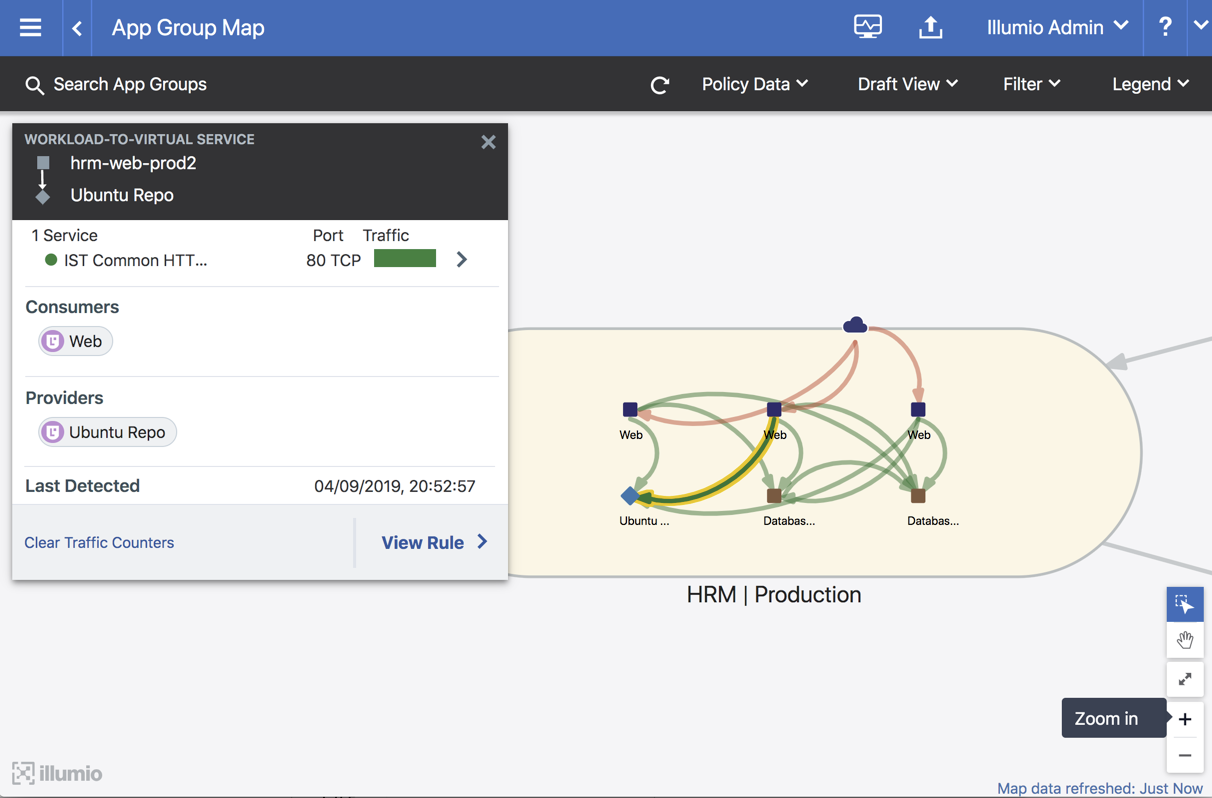
Example of traffic to the virtual service in Illumination:
Write Policies to Allowlist FQDNs
IP List
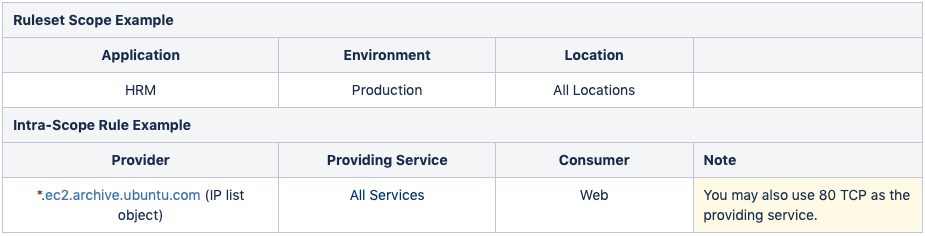
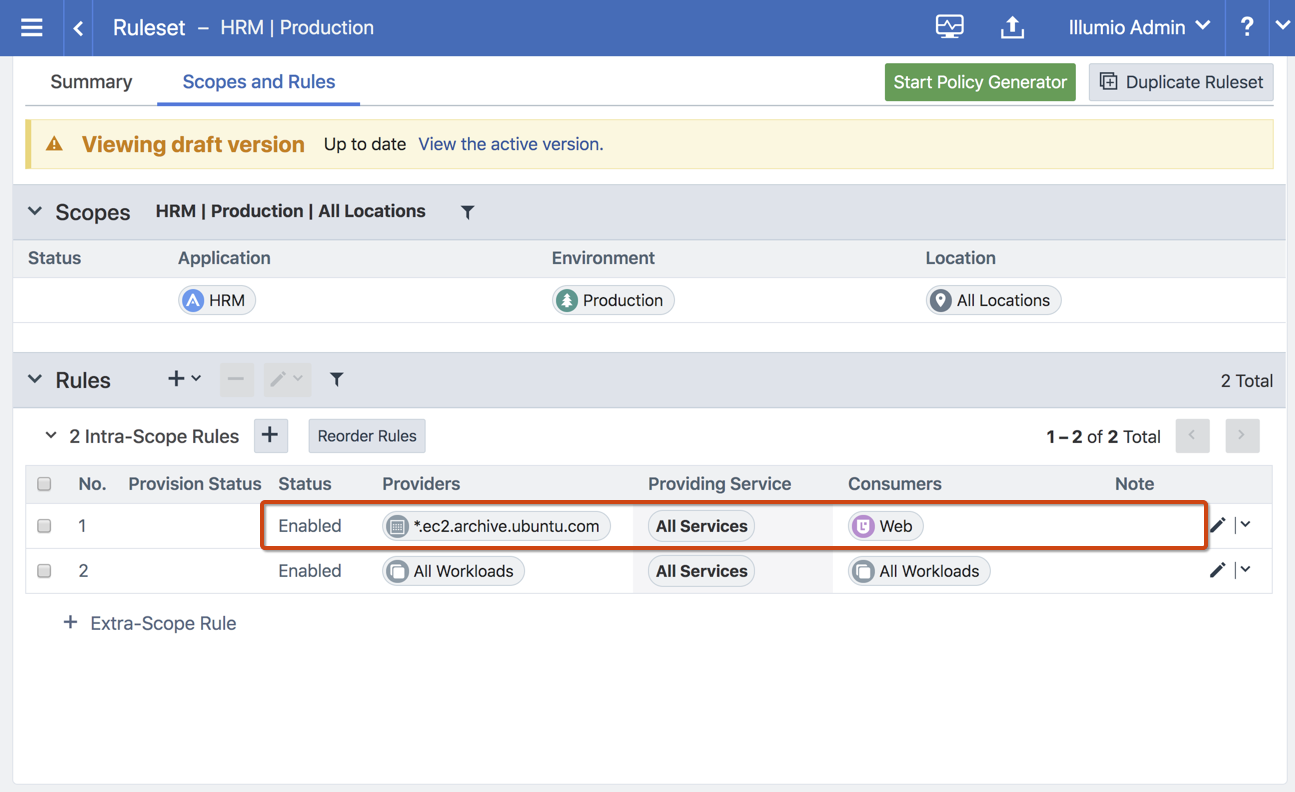
The syntax and ruleset structure for IP list policies does not change for FQDNs.
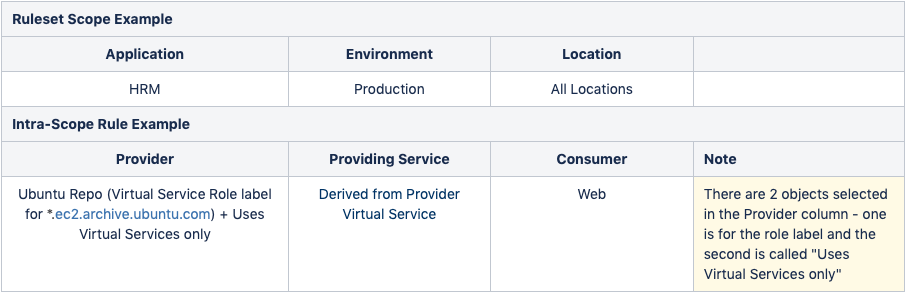
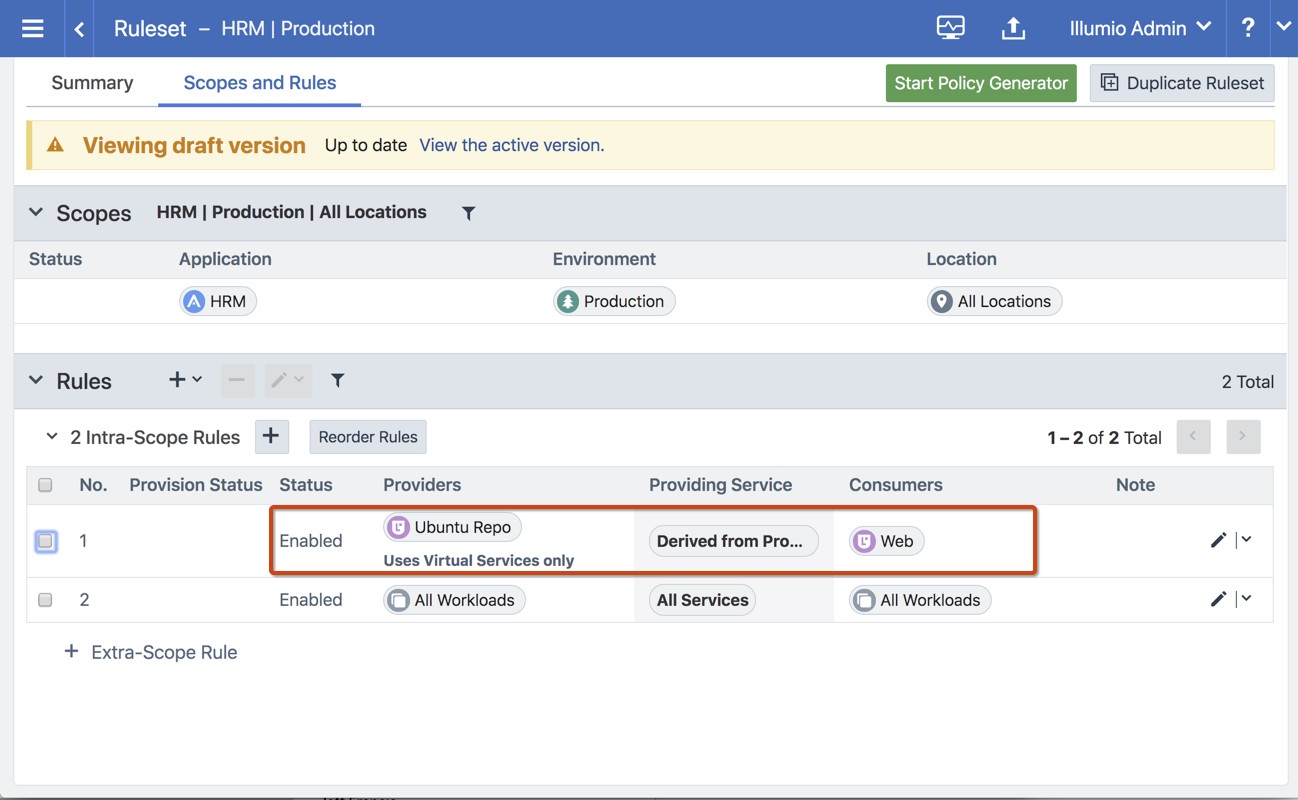
See the following example:
Virtual Service
Writing a policy against a virtual service for an FQDN is the same as writing a policy for an IP-based virtual service.
See the following example that uses the Ubuntu Repo (*.ec2.archive.ubuntu.com):