About Reports
The PCE includes the ability to generate, download, and manage two types of recurring reports: Executive Summary reports and App Group Summary reports.
Reporting in the PCE
The PCE web console menu includes a “Reports” option. When you choose the Reports option, the Reports page appears. This page includes two tabs: Downloads and Recurrence. Generated reports appear on the “Downloads” tab. By default, the list is sorted in descending order by the “Generated At” time.
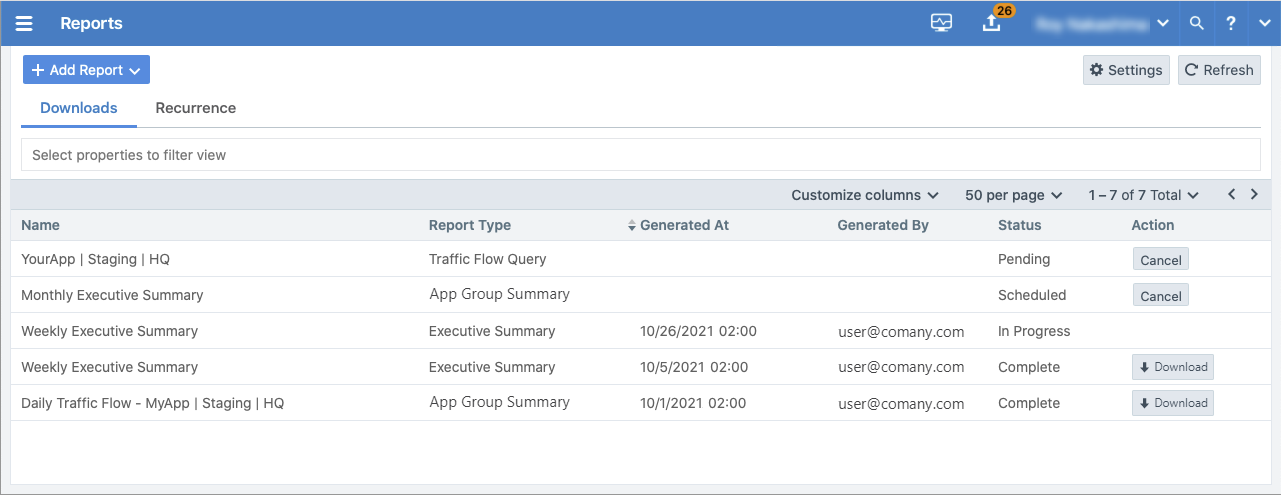
Because Illumio provides the reports as downloadable PDF files, you can share them with people in your organization who don’t have access to the PCE web console or PCE REST API.
The data in the reports is not customizable. However, you can configure the time range of the data that the reports are generated from and the frequency at which they are run. Both types of reports include when a specific report was generated, which Illumio user generated it, and the PCE version from which the data was obtained.
Recurring reports are run on the following schedule:
Daily: Midnight each day
Weekly: At midnight on the first Saturday after the report was added, then weekly at Saturday midnight
Monthly: Midnight on the last day of month after the report was added, then monthly on the last day at midnight
The PCE does not cap the number of reports you can create, only the only the length of time you can retain them. Generated reports include data for provisioned security policy, managed and unmanaged workloads, and provisioned policy objects. They do not include changes you have made to your environment but haven't provisioned.
Executive Summary Reports
Executive Summary reports are high-level by design. They provide information to decision makers, such as an organization’s CIO or VP if IT, about the overall deployment of Illumio within the organization’s computing environment. These reports are intended to provide more business-oriented information than tactical data.
Executive Summary reports give the decision makers a snapshot into how Illumio policy enforcement is progressing and can display the return on investment (ROI) for purchasing and deploying Illumio software.
Executive Summary reports answer the following questions for decision makers:
How are we progressing in deploying security policy into our environment?
How many of our workloads are being managed by Illumio (VENs are installed on the hosts but they aren’t in enforcement mode)?
How quickly is enforcement progressing over time (the number of workloads that have moved into the enforcement mode over the report’s specified time range)?
What potentially dangerous traffic is Illumio blocking that wouldn’t have been blocked without Illumio Core, resulting in a security risk.
What sort of vulnerabilities do our workloads have? Vulnerability information is provided as a V-E score that is the sum of all app groups.
Important
To include app group and workload vulnerability data in the Executive Summary report, you must have purchased a license for the Vulnerability Map feature. The Vulnerability Map is a separately licensed feature of Illumio Core. The licensing is based on the number of workloads. The license is required to import Qualys report data into the Illumio PCE. For information about obtaining the Illumio Core Vulnerability Map license, contact Illumio Customer Support.
For more information about Vulnerability Maps, see Vulnerability Map.
Tips for Reading Executive Summary Reports
Executive Summary reports provide high-level information for decision makers. They are meant to show trends and patterns in your roll out of Illumio Core into your data center environment.
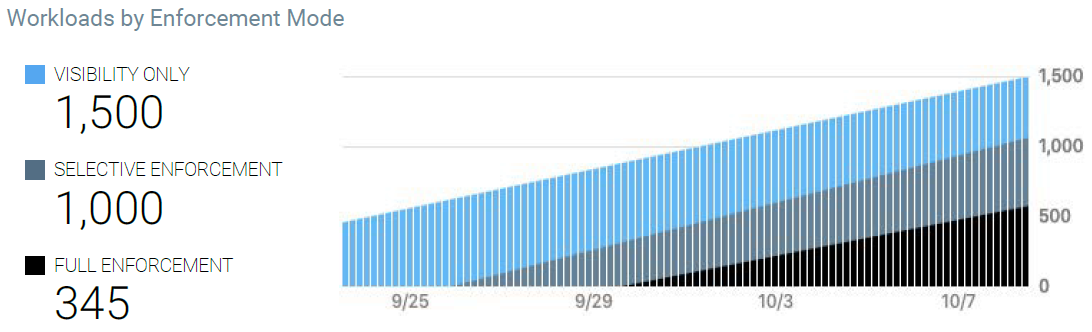
For example, an executive who has approved deploying Illumio Core might want to know how many of their workloads are being managed (enforced) by Illumio policy. The Workloads by Enforcement Mode graph shows the trend for how quickly is enforcement progressing over time and percentage of workloads in deployment versus enforcement.
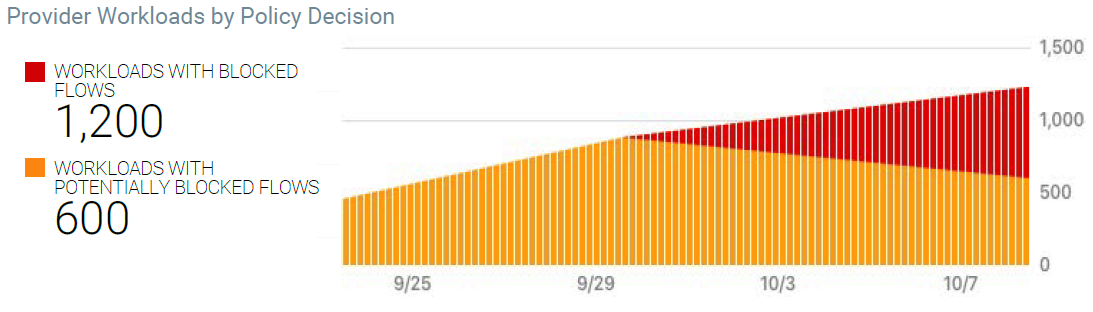
The Provider Workloads by Policy Decision graph show can help confirm when the rules you have created for your data center look viable and you can start enforcing policy on your workloads. This example graph shows a tend you want to see; and visually represents how you initially had workloads deployed but not in enforcement.
App Group Summary Report
Illumio Core contains many features designed for application owners; such as the App Group Map and role-based access (RBAC) for applications owners. See “App Group Map” in the Visualization Guide and “Role-based Access for Application Owners” in the PCE Administration Guide, respectively, for information.
App Group Summary reports are designed for application owners (for example, members of your business applications group like your Oracle or ServiceNow app admins) or other people in your organization who need to understand the security of you applications, such as IT security auditors (for example, auditors of PCI or HIPA systems).
You create App Group Summary reports by application; meaning, each report provides data for only one application defined by a set of labels. Whether you choose 2 labels (application and environment) or 3 labels (application, environment, and location) for a report depends on how you have configured the PCE to define app groups. See Configure App Groups for information.
Using the App Group Summary report, application owners or IT security auditors can accomplish the following goals:
Examine which inbound and outbound services interact with a specific application. Having a clear picture of all traffic into and out of an application is important for accessing the security posture of the application.
Understand whether connections are normal for an application and monitor the application’s health and status over time. For example, you can create a weekly report to monitor the state of an application over time and detect any changes in inbound or outbound network services.
Fulfill compliance auditing requirements. For example, you can run a report every 30 days and review the report to ensure the application connection status matches with the application’s baseline.
Establish a connection baseline for an application and use that baseline to create security policy (rules or selective enforcement rules) for the application. See “Rules” and “Rule Writing” in the Security Policy Guide for information.
After creating security policy (rules) for an application in the PCE, see the impact of the Illumio security policy on the application.