Start Up and Shutdown Events
The PCE leverages the operating system's syslog function to log audit events. As syslog is part of the operational environment, there is no mechanism to enable and disable the audit feature. The PCE starts sending audit events when it is started. The PCE stops sending audit events when it is stopped. The corresponding events are pce.application_started and pce.application_stopped. These events are registered internally in the log file illumio-pce.log. They are also registered as audit events that are sent to the audit server.
Audit Server and Active Sessions
This section explains how to determine the remote audit server status and discusses the types of active sessions for logged in PCE users.
Determining Remote Audit Server Status
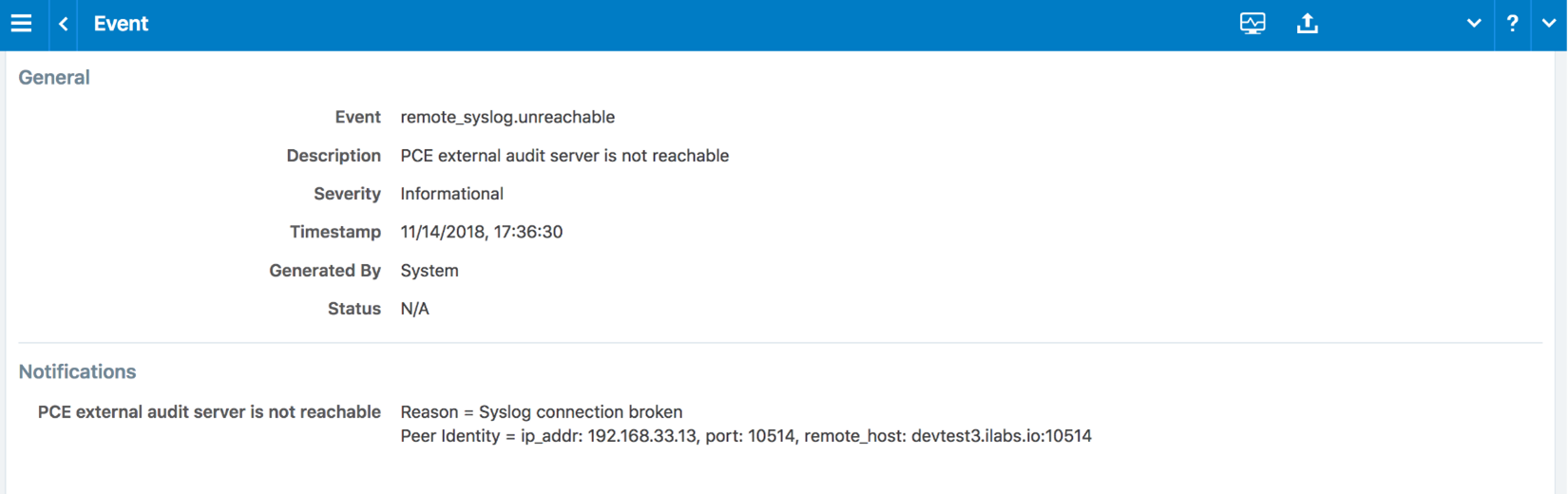
From the “Events Configuration” screen of the PCe web console, one can check the configuration of each audit server. The current reachability status of the syslog server can be found by searching for “remote_syslog_reachable” or “remote_syslog_unreachable” events via the Events Viewer.
Figure 17: Remote Audit Server Reachable
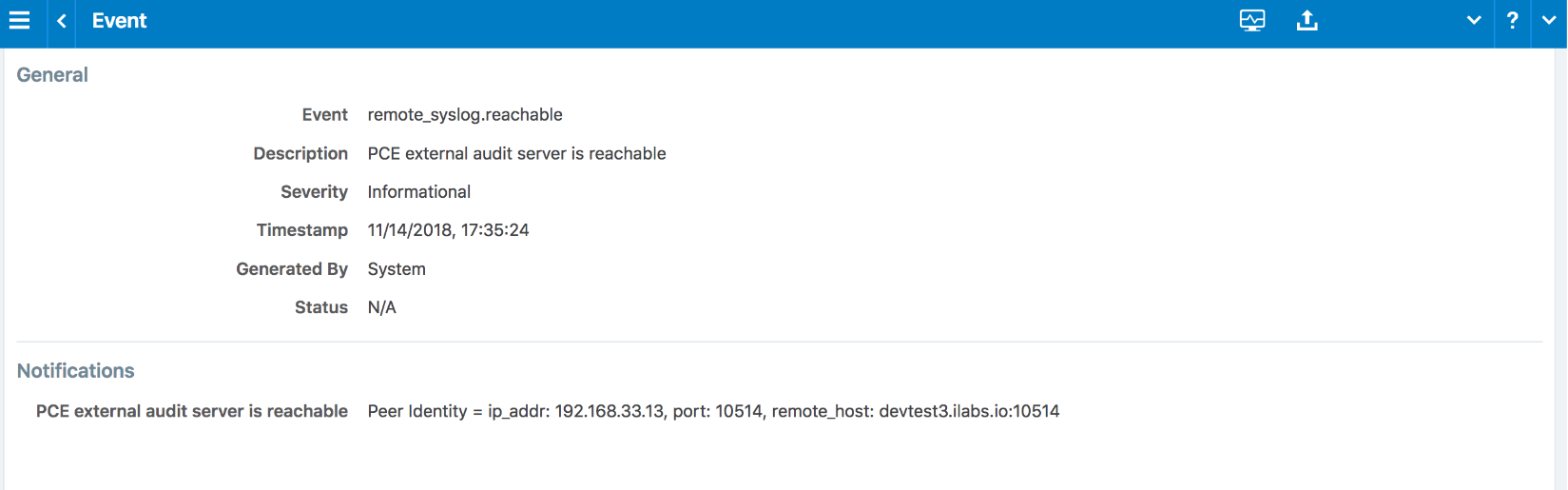
Figure 18: Remote Audit Server Unreachable
Understanding Login Sessions and Agent Manager Sessions
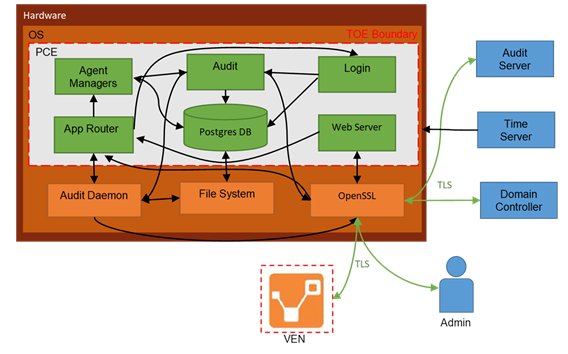
A logged in PCE user has two active sessions – one active session is with the Login service and another active session is with the Agent Manager service:
Login service: Manages sessions related to users and user authentications. The Login service maintains user login sessions.
Agent Manager service: Manages PCE sessions related to policy objects, labels, managed workloads, unmanaged workloads and related PCE services.
Given the two user sessions noted above, the following scenarios are useful in understanding expected audit event messages related to user sessions:
Scenario 1: Both Agent Manager and Login Sessions Expired
When a user takes an action (e.g. first time logging in, refreshes a page) and the session is expired in the Agent Manager, the authentication failure is logged as an event and the user's browser is redirected to the login service for authentication. If the session on the login service has expired too, the user will be prompted to log in and a successful login will result in two session created events corresponding to the two active sessions.
Scenario 2: Agent Manager Expired and Login Session Still Active
When a user takes an action and the session is expired in the Agent Manager, the authentication failure is logged as an event and the user's browser is redirected to the login service for authentication. If the user's session on the login service is still current, the user's browser is redirected back to the Agent Manager (with no interaction from the user) and a new session is created for him, resulting in a single session created event for the Agent Manager session.
Figure 19: Login Service and Agent Manager Service
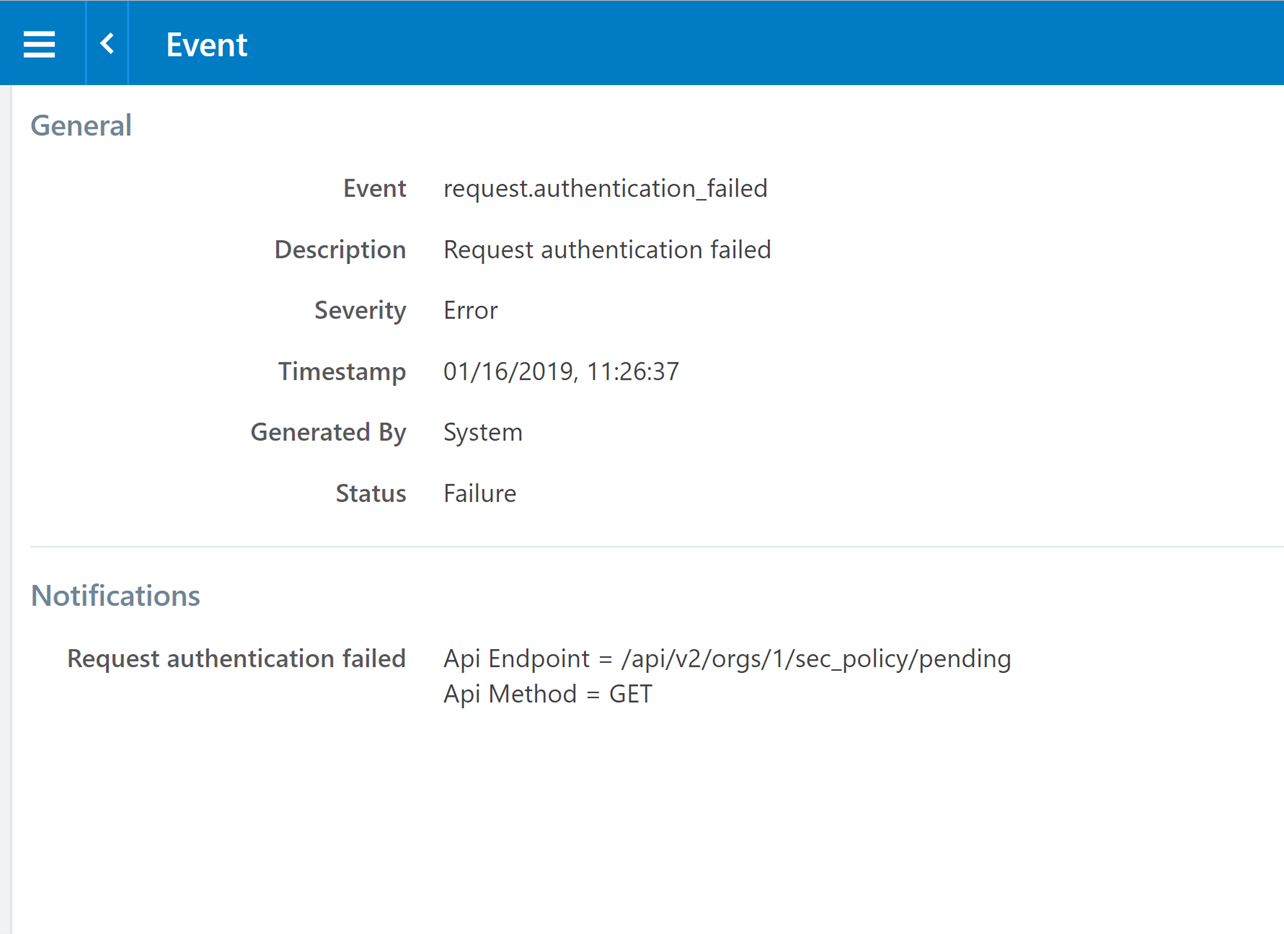
The Agent Manager session can generate events by either a user performing an action or the system performing a task. An example of a “system generated” event is a user authenticated failure event in which a user types in an incorrect password. This results in a “request.authentication_failed” event being generated by the system. (See example below)
Figure 20: User Authentication Failure Event
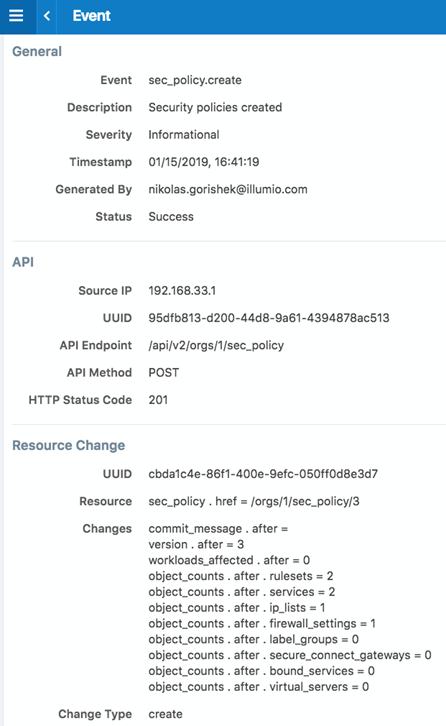
An example of a “user generated” event is when a user creates a new security policy. The resulting event captures the information related to the newly created security policy including a unique identifier listed in the “Resource” field for the event. See example audit message below with unique identifier “version .after=3”:
Figure 21: Event Message Unique ID