Firewall Coexistence on Pods
The Illumio C-VEN configures iptables on each host and each Pod (in a managed namespace). By default, Illumio Core coexistence mode is set to Exclusive meaning the C-VEN will take full control of iptables and flush any rules or chains that are not created by Illumio Core. In containerized environments, this may affect communications to/from container components (Docker, Kubernetes, Illumio Kubelink). Therefore, Illumio Core must allow firewall coexistence in order to achieve non-disruptive installation and deployment.
Note
For Workloads part of a Container cluster (Kubernetes or OpenShift nodes), firewall coexistence is enabled by default if Kubelink was deployed and is "In Sync" with the PCE (prior to the C-VEN installation).
In some cases, there may be some Pods that implement iptables rules inside the Pod namespace for the containerized application to work (VPN, NAT, and others). In order to support such requirements from containerized applications, you should enable firewall coexistence for these Pods.
In order to allow firewall coexistence, you must set a scope of Illumio labels in the firewall coexistence configuration. Once you provision a firewall coexistence scope, the PCE will enable firewall coexistence configuration on all the Pods whose labels fall within the scope.
Note
Labels assigned to Kubernetes cluster nodes must fall within the firewall coexistence scope. This is not a requirement for the labels assigned to container workloads.
To configure firewall coexistence:
In the PCE UI, navigate to Settings > Security.
On the Security page, select the Manage Firewall Coexistence tab.
Click Edit.
In the edit wizard, click Add. The Add Firewall Coexistence Labels and Policy State wizard will pop-up.
Select a scope of Illumio labels. The scope must include the labels you intend to use for your Kubernetes cluster nodes.
Select All for Policy State.
Illumio Core is Primary Firewall - Select your preference.
Yes = (Recommended) Illumio iptable chains will be at the top of iptables at all times. Non-Illumio iptable chains can coexist, but will follow after Illumio chains.
No = (Not Recommended) Non-Illumio iptable chains may coexist and can be placed before Illumio chains.
Note
For deployments using Calico, Illumio recommends setting the Calico ChainInsertMode to Append and set Illumio Core as Primary Firewall value to Yes. If the Kubernetes cluster requires Calico Insert mode, then set Illumio Core as Primary Firewall value to No.
Click OK.
Click Save.
Provision the changes.
Be sure to provision the saved changes or else firewall coexistence will not take effect.
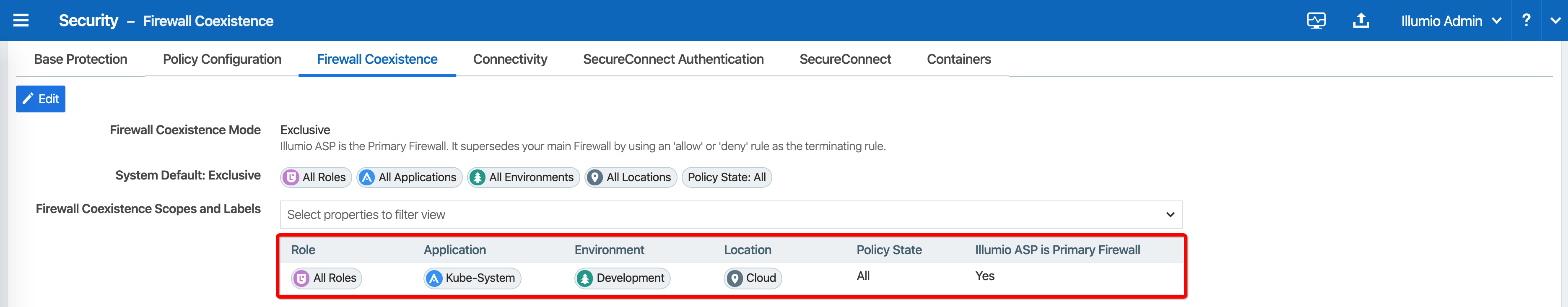
The following example is of a firewall coexistence scope for a Kubernetes or OpenShift cluster which has the following labels:
Role: All
Application: Kube-System
Environment: Development
Location: Cloud
The firewall coexistence scope in the example uses the 'All Roles' objects to cover future Pods spun up in the kube-system namespace that may require additional iptables rules to forward packets.