Core Services Detector
Core services (such as DNS, Domain Controller, NTP, and LDAP) are essential to your computing environment and run on one or multiple workloads. The Core Service Detector feature helps you identify these core services and suggests an appropriate label for them. The Illumio PCE can detect 51 core services. Identifying and labeling these workloads is important because they are centrally connected, and other applications depend on them.
Application owners sometimes don’t know enough about the core services or how to identify them. In addition, different teams could be managing core services, and application owners must coordinate with these teams to secure their applications. When you use the Core Services Detector to label and write policies for core services, you can save time on application policies and progress to policy enforcement faster.
Note
In a Supercluster, the Core Services Detector is available only on the leader PCE.
For information about using the REST API to manage core services, see the REST API for managing Core Services in REST API Developer Guide.
Enabling Core Services Detection
The Core Services Detector is not enabled by default because it is an optional feature. Organizations that have already done extensive work with labeling their core services might not be interested in this feature.
Important
To enable Core Services detection, you must be an Illumio Org Administrator.
To enabled this feature, follow these steps:
To obtain access to the Core Services feature in the PCE, update the value for the following parameter in the PCE
runtime_env.ymlfile:core_services_enabled: trueLog into the PCE web console and choose Settings > Core Services. The setting for the Core Services feature appears.
Select Enabled.
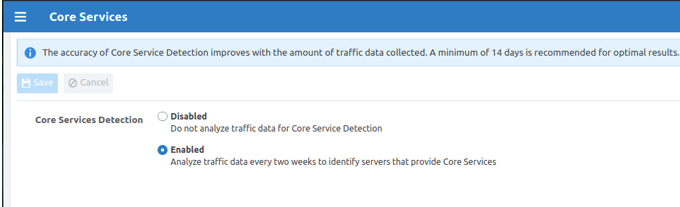
The Core Services menu option will now appear in the PCE web console main menu under Infrastructure and you can use the Illumio REST API to manage Core Services.
Workflow for Managing Core Services
Core Services Detector uses a three-step process to identify and manage core services:
Detect: The detection tool runs in the backend to recommend potential core services (workloads running core services).
Review: Review recommendations provided by the detection tool and accept or reject them.
Label: Label accepted recommendations for core services.
Detection Methods
The PCE uses three methods to detect core services:
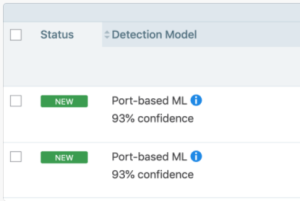
Port Matching: Rule-based model based on connections to specific ports.
Port-based ML: Machine learning model based on connections to specific ports.
Process-based ML: Machine learning model based on processes running on the server.
Note
The method that the PCE uses to detect a core service is not configurable.
All three algorithms run all the time.
The core services detection for Microsoft Active Directory uses the machine learning (ML) model.
Example showing how the PCE web console indicates the detection method:
Identify and Review a Core Service
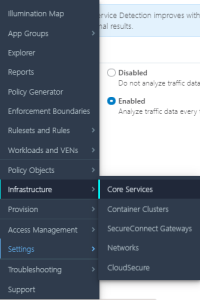
From the PCE web console main menu, choose Infrastructure > Core Services.
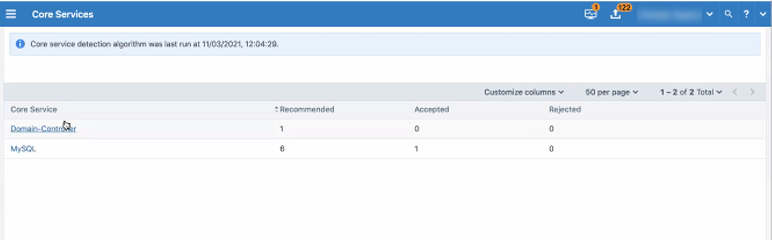
The landing page for core services shows all services detected by the detection tool during the last run.
It also tabulates the workloads that are recommended as running that particular core service along with the ones previously accepted or rejected for that service.
Click the link for any of the listed core services. The page refreshes and displays detailed status for that service.
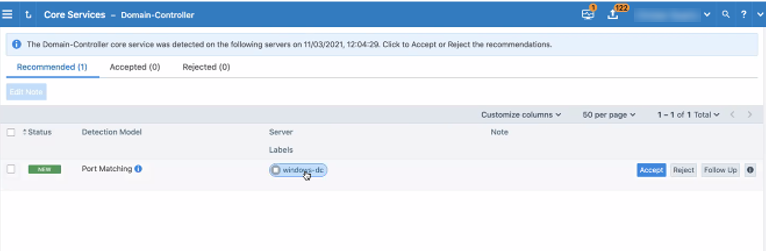
The details page for a core service provides the following information:
Status: Shows whether the recommendation is new.
Detection Model: Indicates with method the PCE used to detect the service.
Server: Displays the IP addresses and workloads recommended for that particular core service. The column includes either a defined workload or an unknown IP address.
Labels: For a defined workload, displays the existing labels.
To see the following details about the service in a pop-up dialog box, click either the detection method or the value in the Server column.
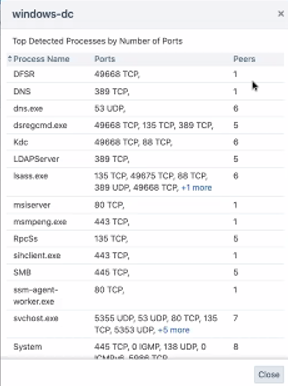
Accept or reject the core service by clicking the buttons on the right.
Accept: If the core service is from an unknown IP address, clicking Accept creates an unmanaged workload:
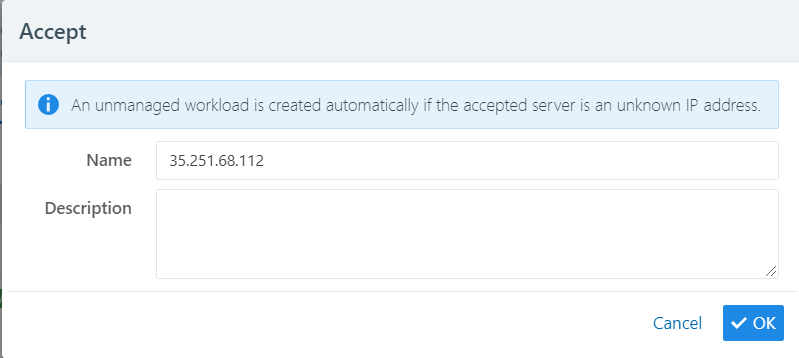
Note
Illumio encourages customers to create unmanaged workloads, install VENs on the unmanaged workloads so that they become managed, and then label them to allow enforcement.
Reject: When you reject the recommendation, that IP address is no longer recommended as a source of the detected core service.
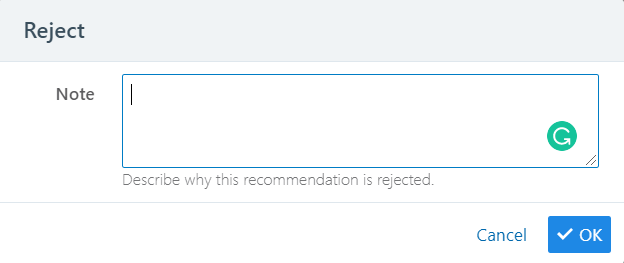
Follow Up: If you are unsure whether to accept the recommendation, leave a note about your reasons to help in later decision-making.
Label the Detected Core Services
Once you have accepted a recommendation to label a service, select the Accepted tab the Core Services page.
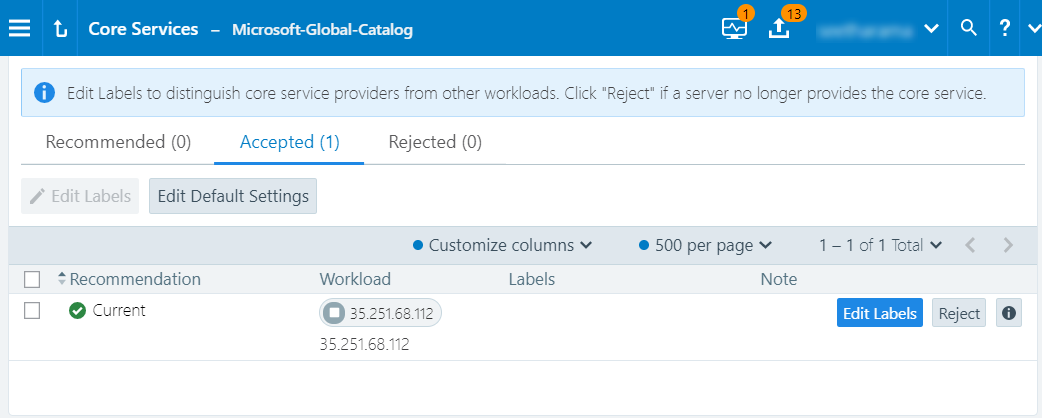
Each service type has its own recommended label.
Click Edit Labels to see what the current labels are. The Edit Labels screen shows the current labels on the left and the recommended label on the right. The types of labels shown include Role, Application, Environment, Location, and any custom label types you have defined using flexible labels.
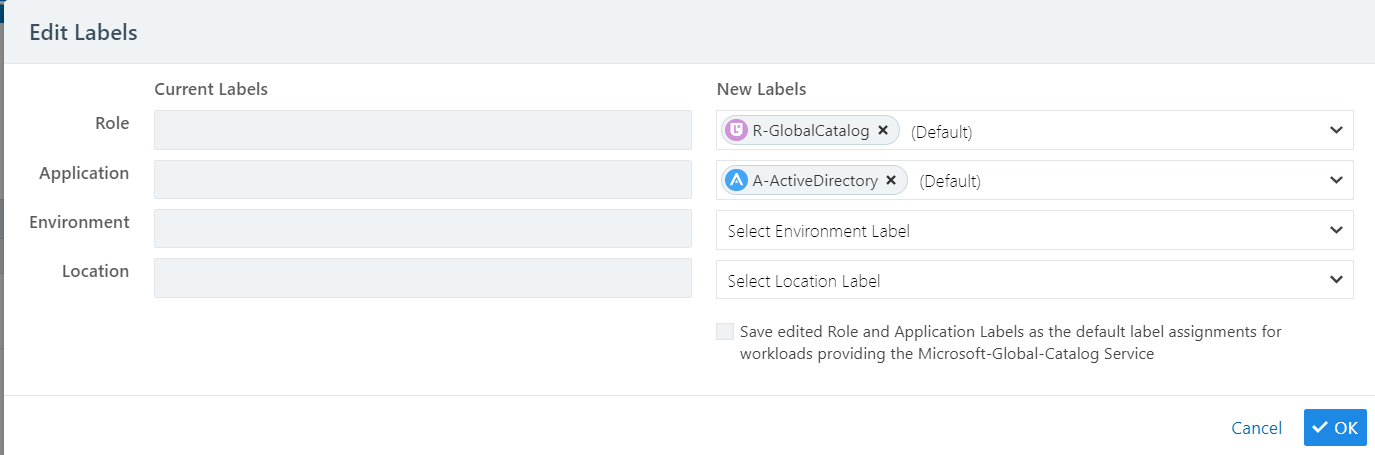
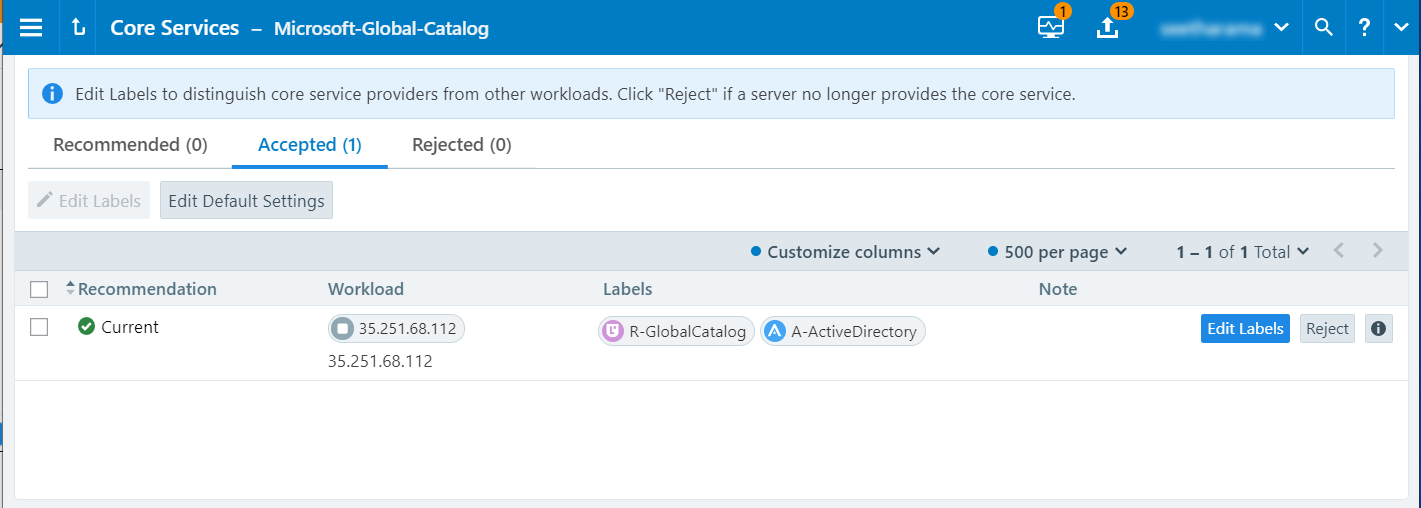
Click OK to accept the recommended labeling.
The page refreshes and displays the labels added for the core service.
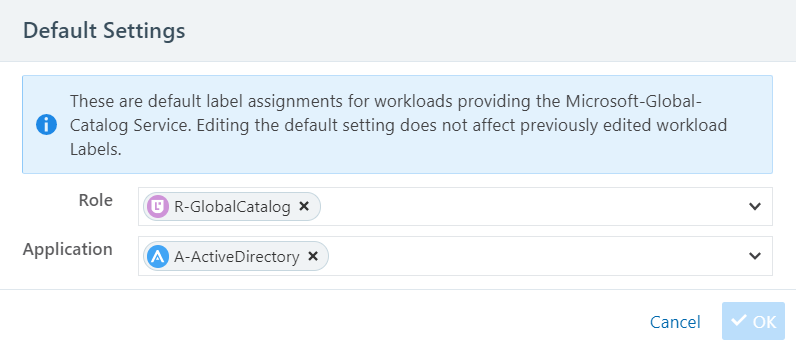
When required for your network environment, change the default labels by selecting the Edit Default Settings button and modifying the labels as necessary.
Important
To change the default label assignments, you must be an Illumio Org Administrator.
Note
Changing the default label assignment does not change any of the previously edited workload labels.
Scanner Detection
Starting in Illumio Segmentation for Data Centers 22.4, scanners running in a network can be automatically detected, much as services are detected.
Important
Scanner detection by default is not enabled. You must manually enable scanner detection at the Core Services page. After being enabled, scanner detection runs every 24 hours to detect scanner traffic.
After a scanner is detected, the src_port can be used to create a collector-side traffic filter, so that traffic originating from that src_port will be dropped and not stored in the PCE.