The Illumio Policy Model
Illumio provides the option to manage your security policies using either adaptive or static policies. Choosing how to implement a security policy is possible because of the Illumio policy model.
Security Policy Guidelines
These guidelines are recommendations on how you can create your security policy in Illumio Segmentation for Data Centers. Creating a security policy is an iterative process. Follow these recommendations to create a broad initial policy that you can improve incrementally till you establish a sufficiently robust policy.
When creating your security policy, follow these guidelines:
Refine your initial policy to strengthen it by narrowing overly broad access.
Use the Visibility Only enforcement to verify and enact your policy.
Enforcement States
After creating a ruleset, preview the effects in Illumination using the Draft View. This view displays the changes that will be implemented by your policy when it is enforced.
Visibility Only: After refining your initial policy, most of the traffic lines in Illumination should be green. No traffic will be blocked, and you can check your policy's accuracy. Any new traffic will be displayed as a red line.
Selective Enforcement: Enables you to protect applications or processes on workloads while other services and ports function as if the workloads are in the Visibility Only enforcement state. By using selective enforcement, you can gradually expand policy enforcement on your workloads. Using the selective enforcement state is useful for temporarily enforcing security for specific ports in case a vulnerability is detected and action must be taken quickly. Using the selective enforcement state enables security enforcement before you can create complete allowlists of what traffic is allowed to reach your workloads.
Full Enforcement: It is helpful to move workloads to the Full Enforcement state in stages. This action can be performed by workload, application, environment, or data center. Start with less critical applications or workloads, stabilize them, then move on to more sensitive systems. This approach minimizes issues to a smaller number of affected workloads.
Understanding Rulesets and Rules
Note
In previous releases, this feature was referred to as “Segmentation Rulesets.” In Illumio Segmentation for Data Centers 21.5.0 and later releases, this feature is now referred to as “Rulesets.”
Rules are a vital component of Illumio's security policy. A set of rules is known as a “ruleset” and it specifies the allowed traffic in your network. Create the rules using labels that identify your workloads.
Illumio's Illumio Segmentation for Data Centers allowlist model for security policy uses rules to define the allowed communication for two or more workloads. For example, if you have two workloads that comprise a simple application — a web server and a database server — to allow these two workloads to communicate, you must write a rule that describes this relationship.
Note
The order in which the rules are written or any possible overlap between rules does not affect the allowlist model, since each rule permits some traffic between workloads.
For example, in the following diagram:
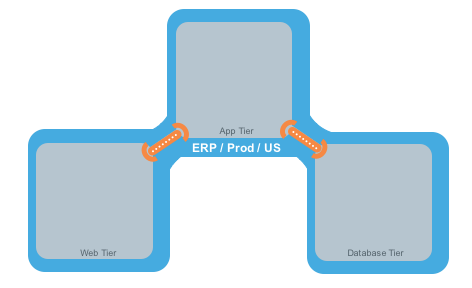
The relationships between the tiers (or workloads, as they are known in Illumio Segmentation for Data Centers) in this example are:
The Web workload can initiate communications with the App workload (Web → App).
The App workload can initiate communications with the Database workload (App → Database).
In Illumio Segmentation for Data Centers, the relationship in the diagram above is expressed as two separate rules:
The Web workload can initiate communications with the App workload.
The App workload can initiate communications with the Database workload.
To build your network security policy, create a ruleset for each of your workloads. Use labels to identify your workloads and use scopes to apply rulesets to multiple workloads simultaneously.
Note
Illumio recommends creating no more than 500 rules per policy; otherwise, the PCE web console will not be able to display all the rules.
If you want to create a policy with more than 500 rules, Illumio recommends splitting the rules across multiple policies or using the Illumio Segmentation for Data Centers REST API, where there is no limit on the number of rules you can create per policy.
Overview of Policy Objects
The PCE contains the following policy objects that help you write your security policy:
Segmentation Templates: Prepackaged, tested security policies that provide all the rules needed for common enterprise applications.
Labels and Label Groups: Group similar labels together and use the label groups in rule writing.
Services Allow you to define or discover existing services on your workloads. When a workload is paired with the PCE (has a VEN installed), it is scanned for any running processes, which are then displayed in the Services list.
Virtual Services: Allow you to label processes or services on workloads. Virtual services can either be used directly in rules, or the labels applied to virtual services can be used to write rules.
IP Lists: Create IP lists (allowlists) to define IP addresses, IP ranges, and CIDR blocks that should be allowed access to your applications.
Load Balancers and Virtual Servers: Add F5 Load Balancer configurations to the PCE so you can write a policy for workloads whose traffic is managed by load balancers.
Pairing Profiles: Configurations that allow you to apply certain properties to workloads as they pair with the PCE, such as applying labels and setting workload enforcement.
User Groups: You can import Active Directory User Groups to write user-based rules for Adaptive User Segmentation.