VEN Support for Standalone Containers
Illumio Core supports the use of containerized workloads, such as those provided by Docker or Podman.
To enable support for standalone (that is, unorchestrated) containers you must configure changes on the PCE. Follow the steps in this topic to support such containers running on a host.
Note
This topic describes VEN support for standalone containers only, and not support on orchestrated container engines, like Kubernetes. If you use orchestrated containers like Kubernetes or OpenShift, you can use the Illumio Core for Kubernetes and OpenShift product.
Supported Versions
Regular VENs are supported on standalone containers only of the versions listed below:
Operating System
First, confirm the Linux OS is supported on your VEN as described in the Illumio Support Portal at https://support.illumio.com/software/os-support-package-dependencies/ven.html#.
Container Engine
Second, confirm your Container Engine version is supported, as shown below:
Container Engine | Version |
|---|---|
Docker | 20.10 19.03 |
Podman | 4.0 and later 3.0 and later |
Capabilities
Using VEN, the protection on standalone containers is:
to and from container hosts
to and from containers through CIHP (Container Inherit Host Policy), given some limitations described below in the Limitations section
Limitations
Note the following limitations:
This support does not provide segmentation between containers on the same host.
This support does not represent the container as a workload (map or policy object), and each container is implicitly part of the Docker host (the workload).
The containers must share the same policies as the host.
CIHP is supported on RHEL 8 / Oracle Linux 8 / Ubuntu 22 or later with Illumio Core 22.5 or later.
In Illumio Core 21.5 and after, if you enforce on the containers hosts only, allow all the traffic to containers and bypass CIHP by enabling IP forwarding. For details, see "Enable IP Forwarding."
Segmentation between containers is NOT supported.
We do recommend you use an orchestration platform to manage your containers. Illumio provides a complete solution for Kubernetes-based platforms, as described in Illumio Core for Kubernetes and OpenShift
PCE Configuration Procedure
Follow these steps to configure the PCE to support containers running on a host.
Configure Containers to inherit host policy.
This is disabled by default. Enabling support copies the host policy (all Illumio iptables related rules) into the filter:FORWARD chain so that packets forwarded to containers are controlled by the Illumio security policy.
Set a scope of Illumio labels for host with containers:
Go to Settings > Security.
Click the Containers Policy tab and then click Edit.
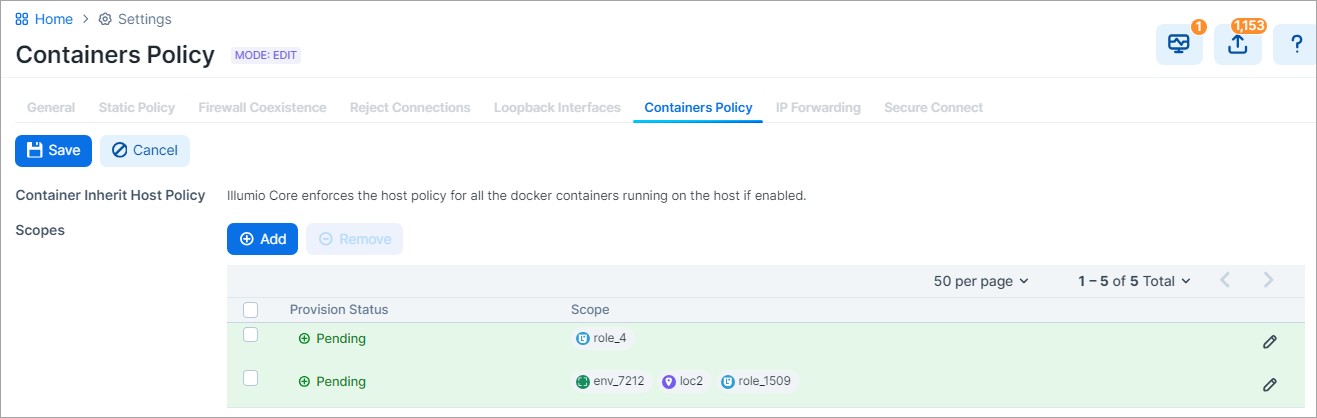
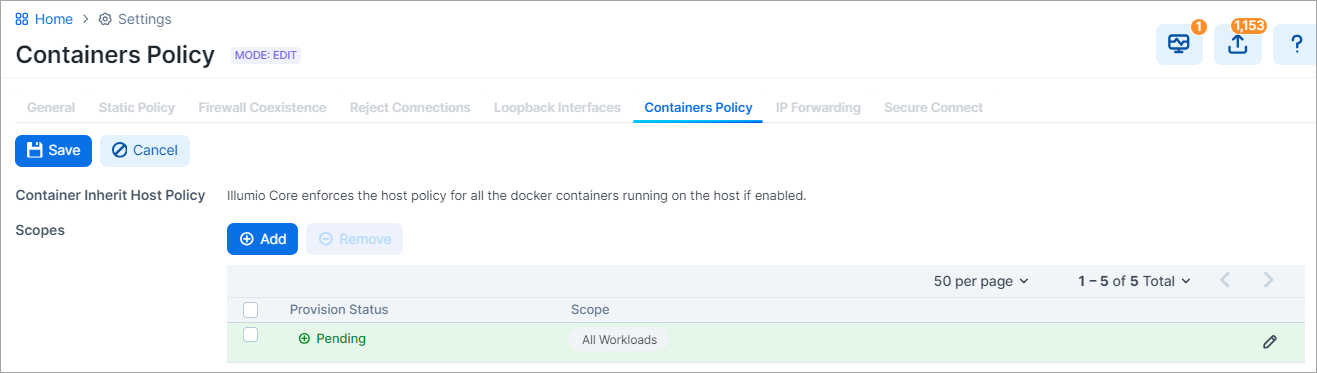
Add scope for host with containers.
You can define a narrow scope with specific label values, or a broad scope that encompasses all workloads, as shown in the two examples below:
Pair workloads with containers, or if they are already paired, go to the Security section of the workload's details page and verify that the workload's containers settings shows Container Inherit Host Policy: Yes.
Write rules to cover the port mapping between the host and the container. Below is an example scenario of container access:
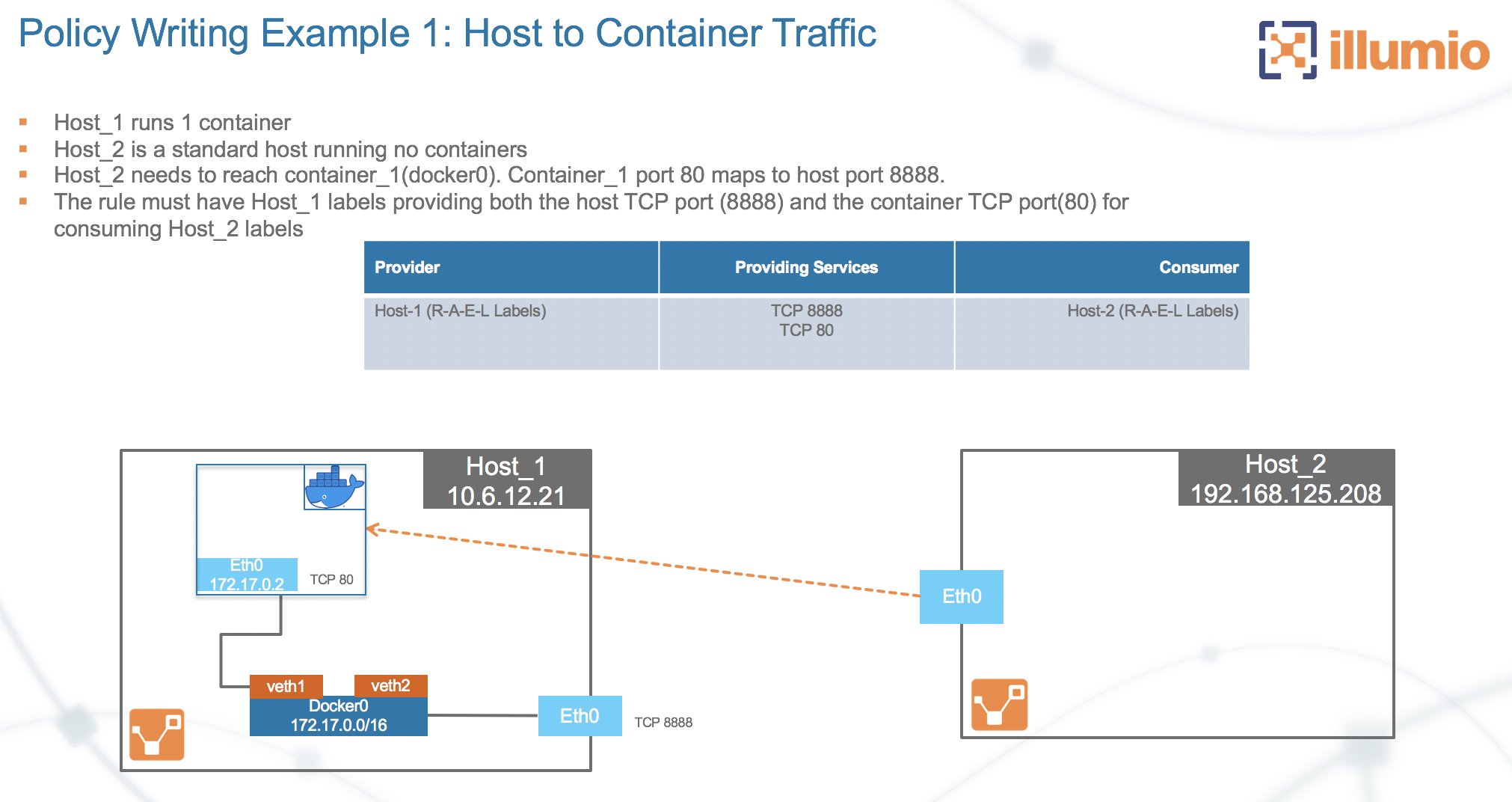
To allow access to container on Host_1 port 80, create an intra-scope rule for access within the application group and extra-scope rule for access from outside of the application group.
The example rule below allows any workload to access container port 80 on Host_1. Notice the service includes both port 80 of container port and port 8888 of host port.
Rule allowing access to container on Host_1:
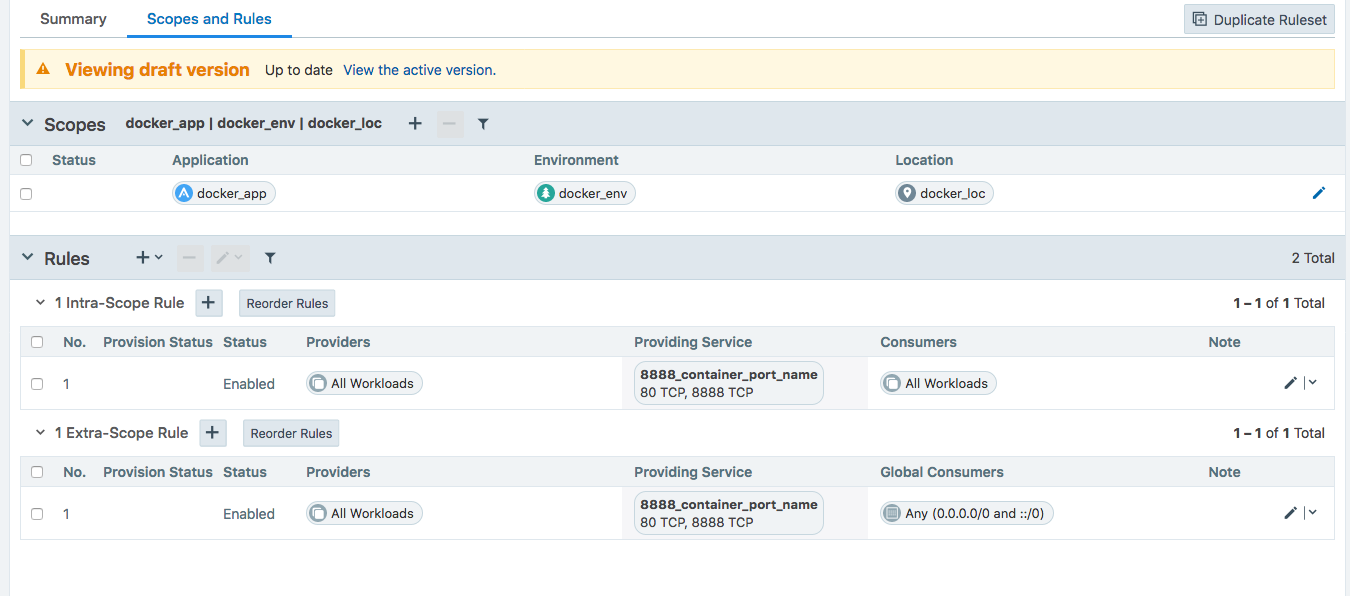
Docker will have rules to NAT port 8888 to port 80.
Verify traffic flows to the containers on the VEN.
Verify in the log at
/opt/illumio_ven_data/log/vtapdrop.logthat there is no dropped traffic to the containers. In the/opt/illumio_ven_data/log/vtapflow.logfile, verify that there are flows to the containers on the VEN when workload is enforced.The highlighted log entry below below shows the flow between host_2 192.168.125.208:54253 to container on Host_1 172.17.0.2:80:
==> /opt/illumio_ven_data/log/vtapflow.log <== 2020-02-03T16:47:15.104-08:00 docker0 O 0 4 192.168.125.208 172.17.0.2 6 64886 80 12286 C 0 U SWID=3c1b9f96-969a-472e-bbbc-9d1c93751ef9 TBI=0 TBO=116 2020-02-03T16:48:15.157-08:00 docker0 O 0 4 192.168.125.208 172.17.0.2 6 64885 80 72339 C 0 U SWID=3c1b9f96-969a-472e-bbbc-9d1c93751ef9 TBI=0 TBO=116
Inbound traffic from Host_2 to Host_1 will not be shown in
vtapflow.log, only traffic to container IP address from Host_2.