Firewall Coexistence
To provide additional security, you can supplement Illumio's firewall with your organization's firewalls using Firewall Coexistence. The Illumio firewall can be set to either Exclusive mode or Coexistence mode via the PCE web console or the Illumio REST API. In both modes, the Illumio firewall is always separate from other firewalls.
Note
Using Firewall Coexistence requires careful consideration
Illumio cannot prevent any non-Illumio processes from programming the firewall, so interference from non-Illumio processes is always possible. The server VEN is able to detect many cases of such interference and will report them as firewall tampering. Although Illumio expects to have exclusive control over the firewall by default (preferred), it is possible to coexist with non-Illumio processes depending on exactly how the non-Illumio processes are programming the firewall.
Because the VEN has no way to know about the actions of non-Illumio processes, coexistence necessarily results in the loss of some visibility and clarity in traffic reporting. For example, server VENs are usually able to coexist with:
Many versions of stand-alone Docker and other simple containers
Manually programmed rules, depending on the precise details
Windows GPO, depending on precise details
Many anti-virus solutions
Server VENs aren't able to coexist with complex containers such as Kubernetes. For such cases, consider using the C-VEN.
Firewall Coexistence and Endpoint VENs
Endpoint VENs are in Firewall Coexistence by default. This cannot be changed.
Important
The Firewall Coexistence feature deprecates these features:
Windows FAS VEN coexistence
Linux VEN NAT ignore
Linux VEN container mode
Firewall Tampering Protection
When coexistence is turned on in primary or secondary mode
The VEN only monitors its own firewall rules against tampering. When the VEN detects tampering of Illumio firewall rules, an alert is raised, and the VEN reconfigures its firewall rules to its pre-tampered state in order to protect the workload. You can program non-Illlumio rules in any table without generating any tampering alerts.
When coexistence is turned on in primary mode
The VEN also monitors that the Illumio rule in the main tables “stay on the top” when you choose Illumio to be the primary firewall. When the VEN detects that the Illumio rule is not on the top, an alert is raised, and the VEN moves the Illumio rule back to the top.
Firewall Coexistence Modes
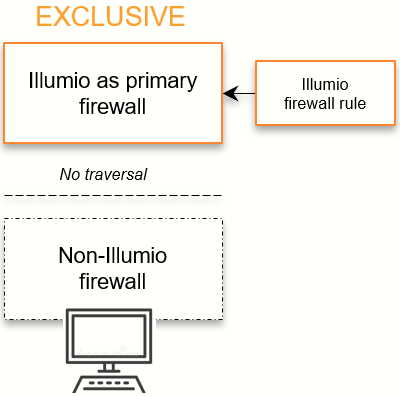
Exclusive Mode
The default mode is Exclusive, in which Illumio is the only firewall. In this mode, any non-Illumio firewall is not traversed. This behavior applies to all tables in iptables, such as filter, NAT, Raw, or Mangle.
Coexistence Mode
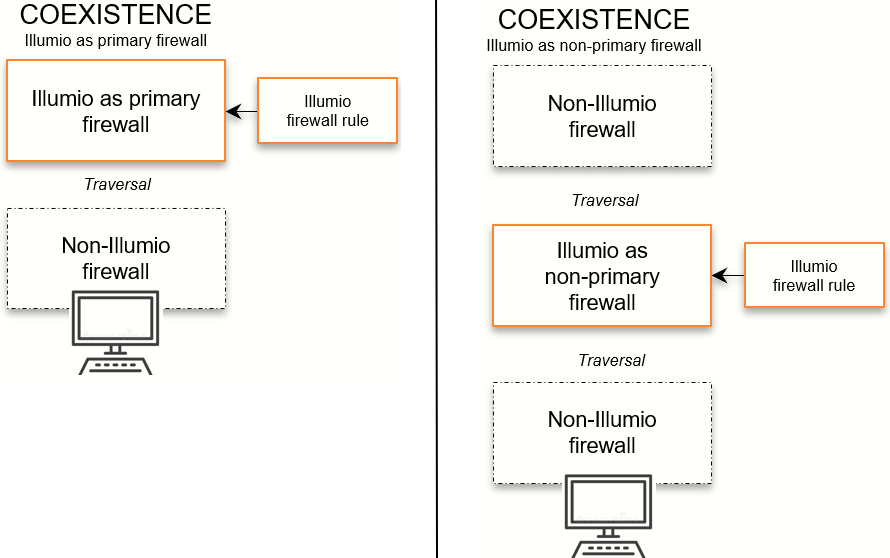
With a set of labels and policy states, you can enable Firewall Coexistence for a set of workloads. You can configure coexistence in two ways:
A configuration in which Illumio is the primary firewall.
A configuration in which Illumio is not the primary firewall.
Note
The Coexistence mode applies to all tables of the Linux firewall.
Prerequisites and Recommendations
This release of the Firewall Coexistence feature requires that you upgrade the VEN to 18.3.1 or later. The older versions of Illumio Firewall Coexistence are deprecated.
Windows VEN version 18.3.x ignores the older limited_wfas_coexistence and full_wfas_coexistence VEN settings for coexistence located in the VEN runtime_env.yml file. Linux VEN version 18.3.x ignores settings in /etc/default/illumio-agent for NAT table coexistence (container mode).
The following upgrade sequence is required. You must upgrade the VEN last and only after configuring firewall coexistence in the PCE:
Recommended Firewall Setting
For better security, Illumio strongly recommends setting the Illumio firewall as the primary firewall.
When you select Illumio to be the primary firewall, the VEN ensures that the Illumio rule in the main tables “stay on the top” only when you choose Illumio to be the primary firewall. The VEN does not enforce the Illumio rules to be on the top when Illumio is not the primary firewall. This behavior applies to all tables in iptables, such as filter, NAT, Raw, or Mangle.
When the Illumio firewall is set as primary, non-Illumio firewalls are traversed only when the Illumio firewall rules allow the traversal, in which case, packets are passed to non-Illumio firewalls.
Important
When the Illumio firewall is not set as primary, packets passed by non-Illumio firewalls are seen by the Illumio firewall; however, packets accepted by the non-Illumio firewall are not seen by the Illumio firewall.
Example
When the Illumio firewall is not set as primary, and the non-Illumio firewall logs and accepts all traffic on port 22, the Illumio firewall does not see the traffic on port 22.
When packets are allowed by the Illumio firewall, they are passed to other firewalls. Illumio's firewall does not monitor packets dropped by other firewalls. Packets dropped by the Illumio firewall are not passed to non-Illumio firewalls.
Set Firewall Coexistence
Warning
Endpoint VENs are in Firewall Coexistence by default. This cannot be changed.
Firewall Coexistence is not supported on Solaris and AIX platforms.
You can set firewall coexistence using either interface:
PCE web console
Illumio REST API
To view firewall coexistence settings in the PCE web console:
From the PCE web console menu, choose Settings > Security > Firewall Coexistence. The PCE web console displays the following settings:
Default: Ilumio Core is the exclusive firewall by default. You can configure firewall coexistence as needed for all workloads, for specific labels, or for both.
Firewall Coexistence:
To add the scope for firewall coexistence:
Click Add.
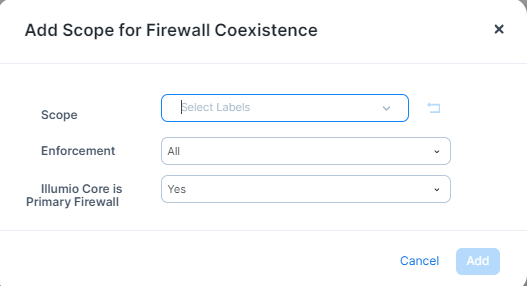
From the Scope drop-down list, select the labels.
From the Enforcement drop-down list, select All, Enforced, or Illuminated.
In the Illumio Core is Primary Firewall, select either Yes or No.
When finished, click Add.