Workload Ransomware Protection for Server Details
The Ransomware Protection tab provides detailed protection information for the workloads regarding each of the ransomware-risky services. Information about the ransomware risk is then aggregated into the Ransomware Protection Dashboard for the system-side ransomware risk analysis.
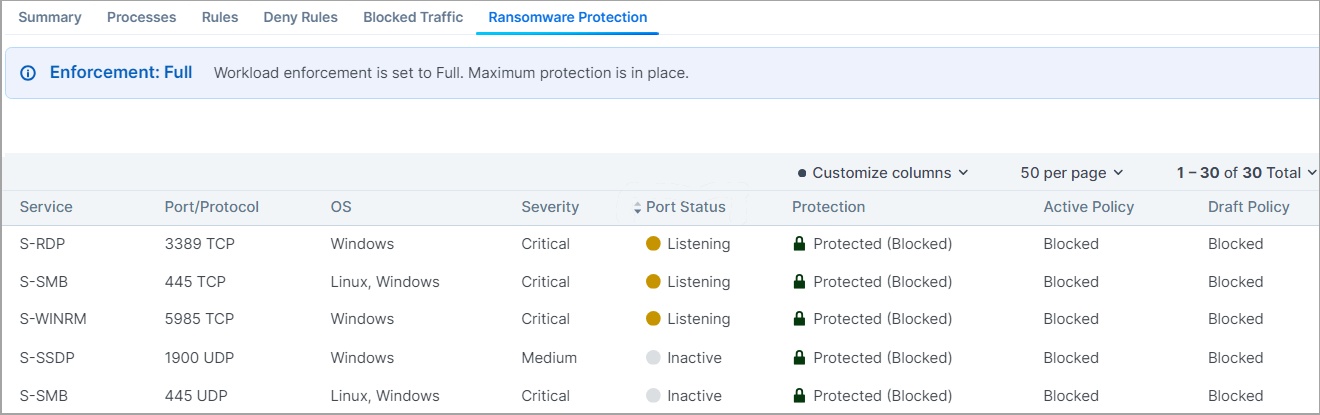
The Severity and Port Type are designated per each ransomware-risky service. Here is the explanation for the data provided in the Ransomware Protection table:
Severity: Severity of the ransomware risk, which can be Critical, High, Medium or Low.
Port Status: Port status can be Active or Inactive.
Listening: Listening means there is a running process on that port.
Inactive: Inactive means there is no process running on the port. The same information is also provided on the Processes tab.
Port Type: The port type can be Admin or Legacy.
Admin: Admin refers to the service and ports are used for common administrative tasks.
Legacy: Legacy means that ports are used for legacy protocols.
Protection: Protection types are:
Protected (Blocked). When port is blocked by deny rules in Selective Enforcement or blocked with no allow rules in Full Enforcement. No ransomware can propagate through that port.
Unprotected The port is exposed to ransomware exploits.
Protected (Allowed by Policy). When there are allow rules intentionally policing the traffic. Only the trusted sources are allowed to access the port and hence the risk of lateral movement for ransomware is reduced. The workload has to be either in Selective Enforcement or Full Enforcement for the policy to be enforced.
The Port status does not affect the protection state.
Active Policy and Draft Policy: Indicates whether there is an Active or Draft policy to protect that particular port and the corresponding action.
API Support for the Ransomware Protection for Servers Dashboard
The Dashboard uses several APIs to aggregate various data from the system and helps you focus on the data you are interested in.
The two main APIs are: time_series and risk_summary. To learn about APIs used to power the Ransomware Protection Dashboard, see "Ransomware Protection Dashboard APIs" in the REST API Developer Guide.