About Analytics Rules
Sentinel Analytics rules are KQL queries on logs that you can either run upon request or schedule. When an Analytic rule finds a match in the log data, a Sentinel alert and incident are created.
The following rules are included in this release of Illumio Sentinel Solution:
Illumio Firewall Tampering Analytic Rule
Illumio Enforcement Change Analytic Rule
Illumio VEN Offline Detection Rule
Illumio VEN Deactivated Detection Rule
Illumio VEN Suspend Detection Rule
Illumio VEN Clone Detection Rule
Each of these rules will be triggered when there is a corresponding VEN event. The hostname and IP address will be collected so that the admin can troubleshoot.
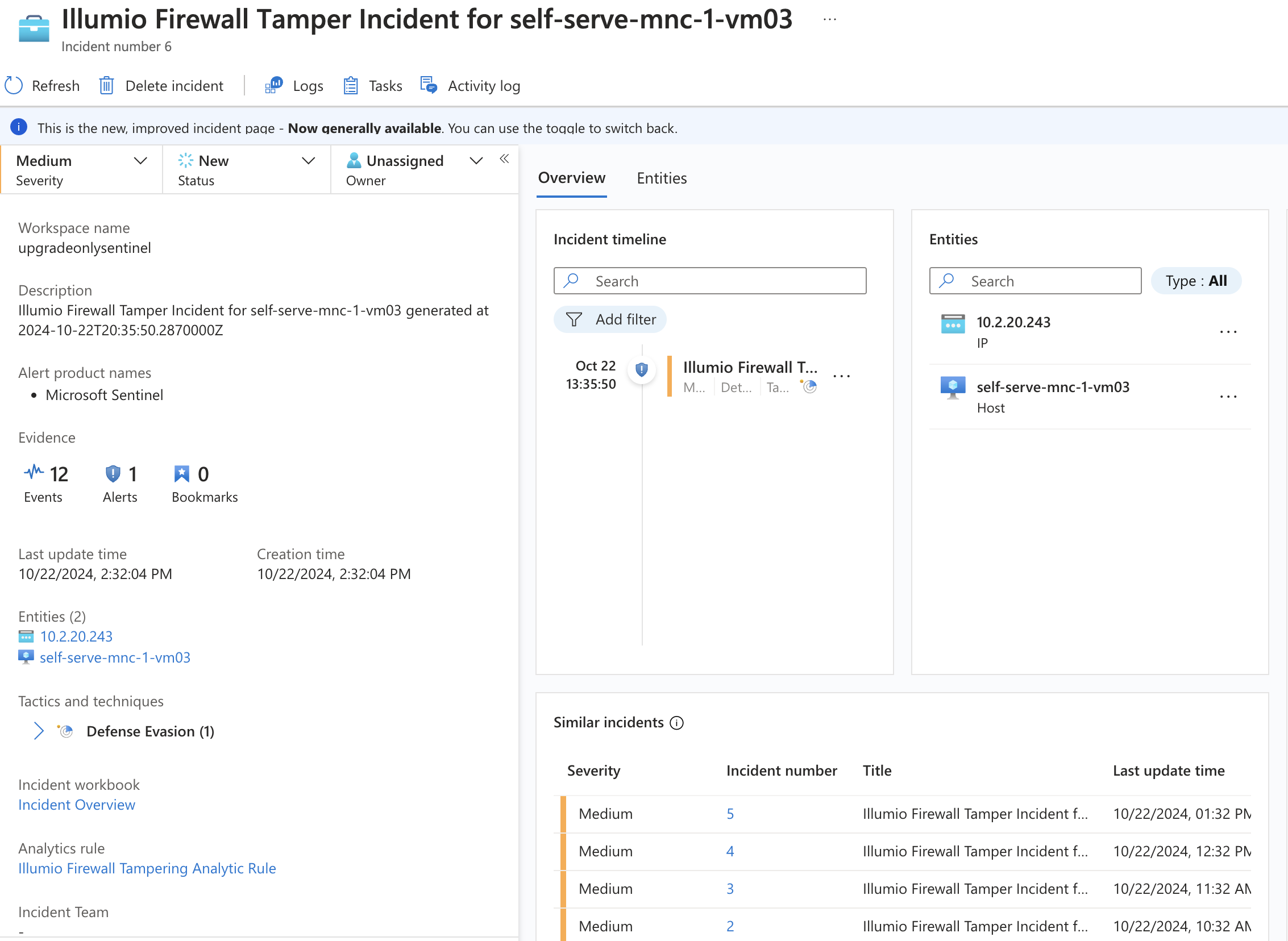
The following screenshot shows an example of an incident from one of the Analytics rules: