About the Illumio - Splunk Integration
The Illumio - Splunk integration contains two parts:
The Illumio Technology Add-On, or TA, which performs metadata collection and event parsing.
The Illumio App for Splunk, which provides dashboards and reports to display important data from the Illumio PCE.
Install the TA to each tier of a distributed Splunk deployment, but install the app only on the search head or search head cluster:
Component | Forwarder | Indexer | Search Head |
|---|---|---|---|
Illumio Technology Add-On for Splunk | Yes (Heavy Forwarder only) - data collection and modular input | Yes - index-time filtering and transforms | Yes - search-time field extractions and transforms |
Illumio App for Splunk | No | No | Yes |
Specific recommendations for the configuration and topology of a distributed Splunk environment are outside the scope of this document. See the documentation on Splunk Validated Architectures for suggestions on topology for distributed deployments.
Supported Splunk Versions
V4.0.3: Splunk 9.3, 9.2, 9.1, 9.0, 8.2, 8.1 + PCE 21.5, 22.2, 22.5, 23.2, 23.5, 24.2.x, and SaaS
v4.0.2: Splunk 9.3, 9.2, 9.1, 9.0, 8.2, 8.1 + PCE 21.5, 22.2, 22.5, 23.2, 23.5, and SaaS
v4.0.1: Splunk 9.1, 9.0, 8.2, 8.1 + PCE 21.5, 22.2, 22.5, 23.2, and SaaS
Important
Version 4.0.2 consists of TA-Illumio version 4.0.2 and Illumio App for Splunk version 4.0.1.
Splunk Common Information Model (CIM) versions 4.x and 5.x are supported.
About Illumio Event Data Collection
The following diagram describes how Illumio event data is collected for On-Premises deployments:
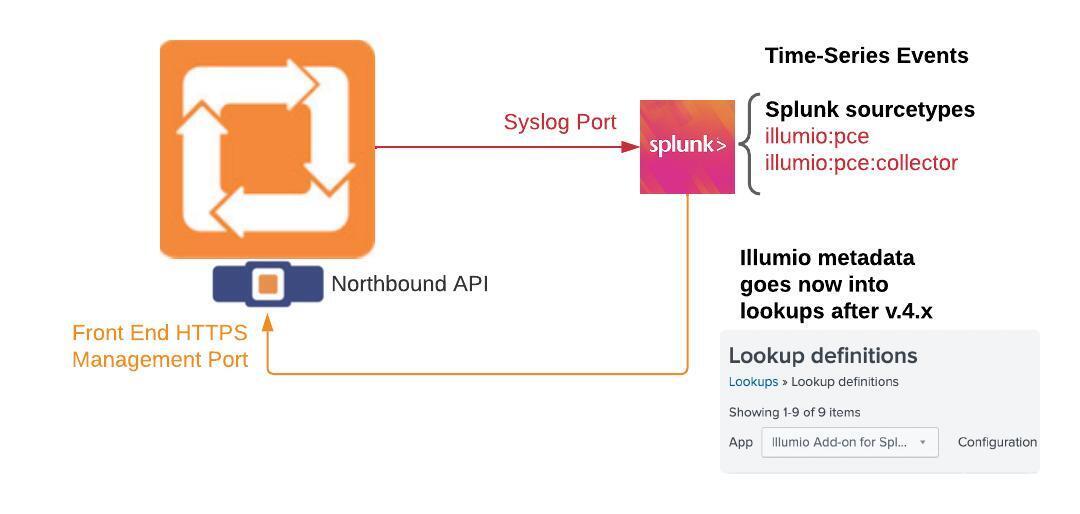
The following diagram describes how Illumio event data is collected for Cloud deployments:
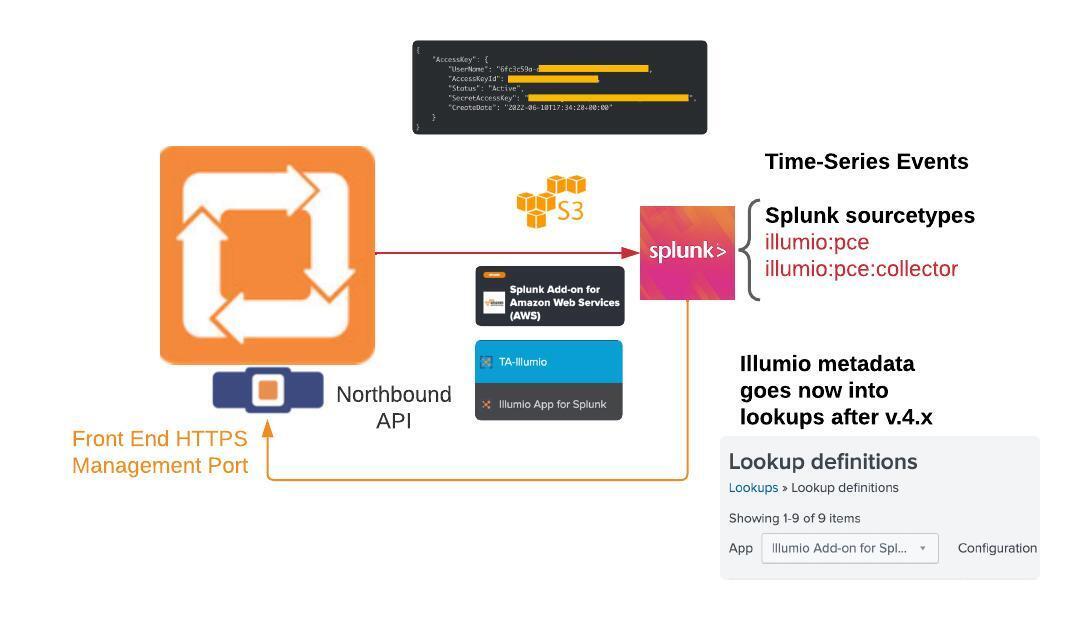
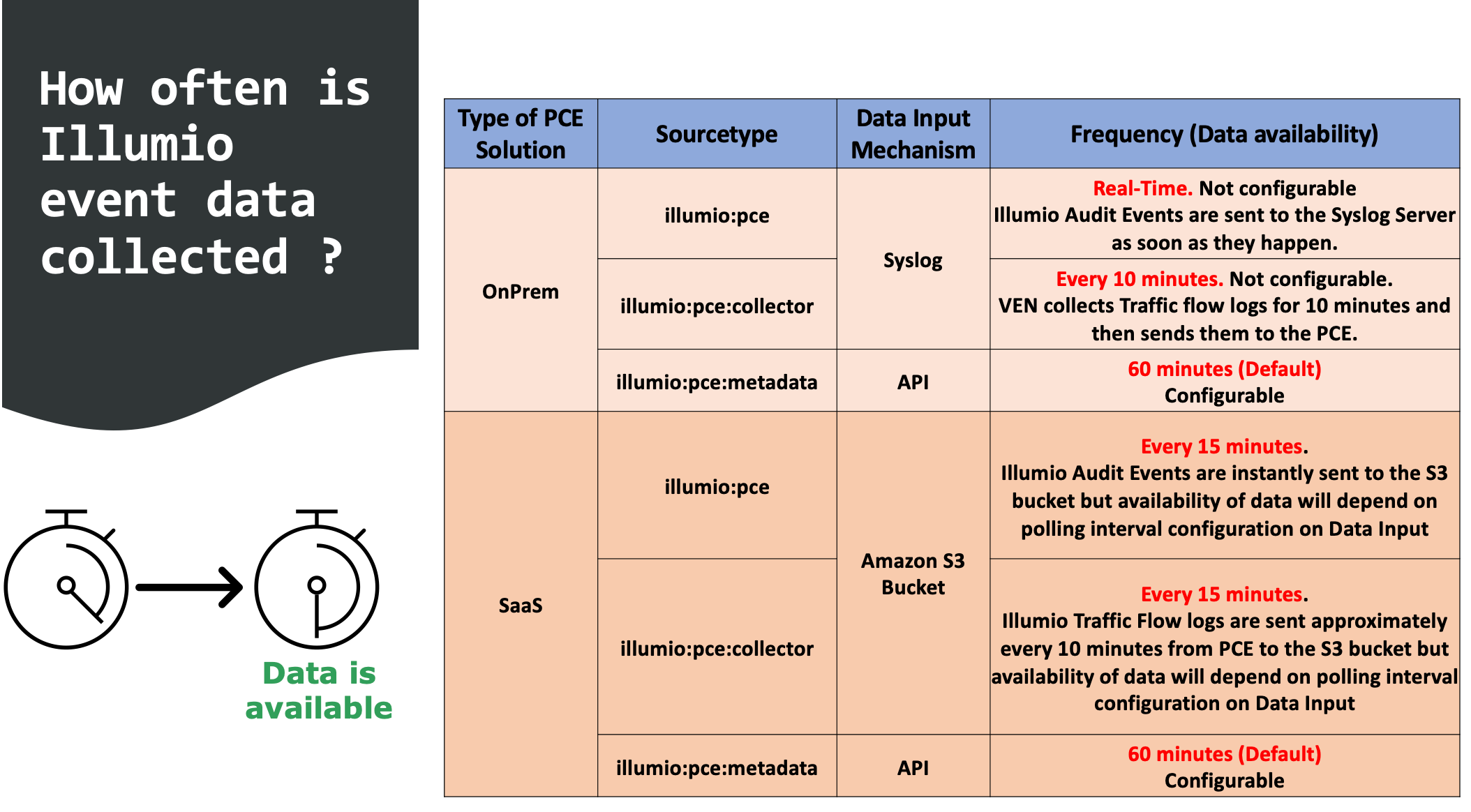
The following diagram describes how often Illumio event data is collected and is then available for search:
About the Illumio Technology Add-On for Splunk
The Illumio Technology Add-On for Splunk (TA) pulls data into Splunk and performs data normalization and enrichment. Illumio event fields are aliased and transformed to be compatible with the Common Information Model (CIM) and used with other Splunk products and add-ons.
The Illumio TA defines a custom Illumio modular input that can be configured on a standalone Splunk instance or Heavy Forwarder to retrieve data from the PCE. See Configure the Illumio Technology Add-On for Splunk.
The TA receives data from the Illumio Policy Compute Engine (PCE) in two forms:
Metadata pulled by the Illumio modular input from the PCE REST APIs
The Illumio modular input pulls Illumio object metadata and status information from the PCE over HTTPS. The input calls the following endpoints:
/api/v2/health
/api/v2/orgs/<org_id>/workload_settings (used to verify the org ID when validating the PCE connection configuration)
/api/v2/orgs/<org_id>/labels
/api/v2/orgs/<org_id>/workloads
/api/v2/orgs/<org_id>/sec_policy/active/ip_lists
/api/v2/orgs/<org_id>/sec_policy/active/services
/api/v2/orgs/<org_id>/sec_policy/active/rule_sets
Syslog events forwarded directly from the PCE (on-prem) or pulled using a third-party add-on as described in the document (SaaS)
Sourcetypes
The Illumio modular input writes to a user-configured Splunk index and predefined sourcetypes:
Sourcetype | Description |
|---|---|
illumio:pce | Contains PCE auditable events written to Syslog. |
illumio:pce:health | Contains PCE system health events. |
illumio:pce:collector | Contains PCE network traffic flow events. |
Distributed Splunk Architecture
Install the Illumio Technology Add-On for Splunk on each tier of a distributed Splunk installation. For more information, see Where to install add-ons.
Heavy Forwarder: Configure Illumio modular input instances and TCP receivers to retrieve PCE data and forward it to the indexer/indexer cluster.
Indexer: Install on the indexer/indexer cluster to perform index-time filtering and transformations, including stripping the Syslog prefix for JSON-formatted events.
Search head: Install on the search head/search head cluster to perform search-time transformations, such as lookups, field extractions, and field aliasing.
Field Extractions
The custom Illumio sourcetypes define field extractions to enhance event data at search time. Extractions and aliases modify field names and values for CIM compatibility as shown in the following table:
Sourcetype | CIM Data Model | Tags | CIM Field | Illumio Field |
|---|---|---|---|---|
illumio:pce | Authentication | authentication | action | "success" or "failure" |
app | "illumio_pce" | |||
src | action.src_ip | |||
user | resource.user.username OR notifications.info.*user.username | |||
src_user | created_by.user.username | |||
All Change | change | change_type | same as object_category | |
dest | pce_fqdn | |||
dest_host | pce_fqdn | |||
object | object name or value | |||
object_category | object type (such as workload or rule_set) | |||
object_id | object HREF | |||
src | action.src_ip | |||
status | status | |||
user | created_by.user.username | |||
user_name | alias for user | |||
vendor_product | "illumio:pce" | |||
src_user | created_by.user.username | |||
Network Changes | change network | action | "modified" | |
Auditing Changes | change audit | action | "created", "updated", or "deleted" | |
Account Management | change account | action | "created", "updated", "deleted", or "modified" | |
user | resource.user.username OR notifications.info.*user.username | |||
illumio:pce:collector | Network Traffic | network communicate | action | "allowed", "potentially-blocked", "blocked", or "unknown" |
app | "illumio_pce" | |||
bytes | tbi + tbo | |||
bytes_in | tbi | |||
bytes_out | tbo | |||
dest | dst_ip | |||
dest_ip | dst_ip | |||
dest_host | dst_hostname | |||
dest_port | dst_port | |||
direction | "inbound", "outbound", or "unknown" | |||
dvc | pce_fqdn | |||
protocol_version | version | |||
src | src_ip | |||
src_ip | src_ip | |||
src_host | src_hostname | |||
transport | proto | |||
user | un | |||
vendor_product | "illumio:pce" |
Workload Quarantine Action
The Illumio Technology Add-On for Splunk provides a scripted alert action to move a workload into a configured quarantine zone. You must first define the policy and labels for the quarantine zone on the PCE.
This action takes the following parameters:
workload_href: The PCE workload HREF of the workload to move into quarantine.
pce_fqdn: The fully qualified domain name of the PCE
org_id: The PCE organization ID. (Defaults to 1)
When triggered, the alert action script looks up the modular input matching the given pce_fqdn and org_id and uses the configured PCE connection details when updating the specified workload.
Note
For the action to run successfully, the API key configured for the input must have write permissions for the workloads.
Manually Trigger Quarantine
Run the following search from the Splunk UI to quarantine a workload with a specified HREF:
| makeresults 1 | sendalert illumio_quarantine param.workload_href="/orgs/1/workloads /00f13a7b-0386-4943-a96c-cfd71d4096dd" param.pce_fqdn="my.pce.com" param.org_id=1
About the Illumio App for Splunk
The Illumio App for Splunk integrates with the Illumio Policy Compute Engine (PCE) to provide security and operational insights into your Illumio secured data center. A dashboard view displays an overview of the security posture of the data center.
With improved visibility of east-west traffic, Security Operations Center (SOC) staff can detect unauthorized activity and potential attacks from traffic blocked by Illumio segmentation policy on workloads in "Enforcement" mode. Additionally, the Illumio App for Splunk provides visibility into potentially blocked traffic for workloads in "Test" mode. SOC staff can quickly pinpoint potential attacks and identify workloads with a significant number of blocked flows.
Distributed Splunk Architecture
You only need to install the app on the search tier of a distributed Splunk installation.
Dashboards
The Illumio App for Splunk provides multiple dashboards to display important data from the Illumio PCE.
Security Operations Dashboard
The Security Operations dashboard provides an overview of the PCE security posture, allowing Splunk admins to monitor the state of the network at a glance.
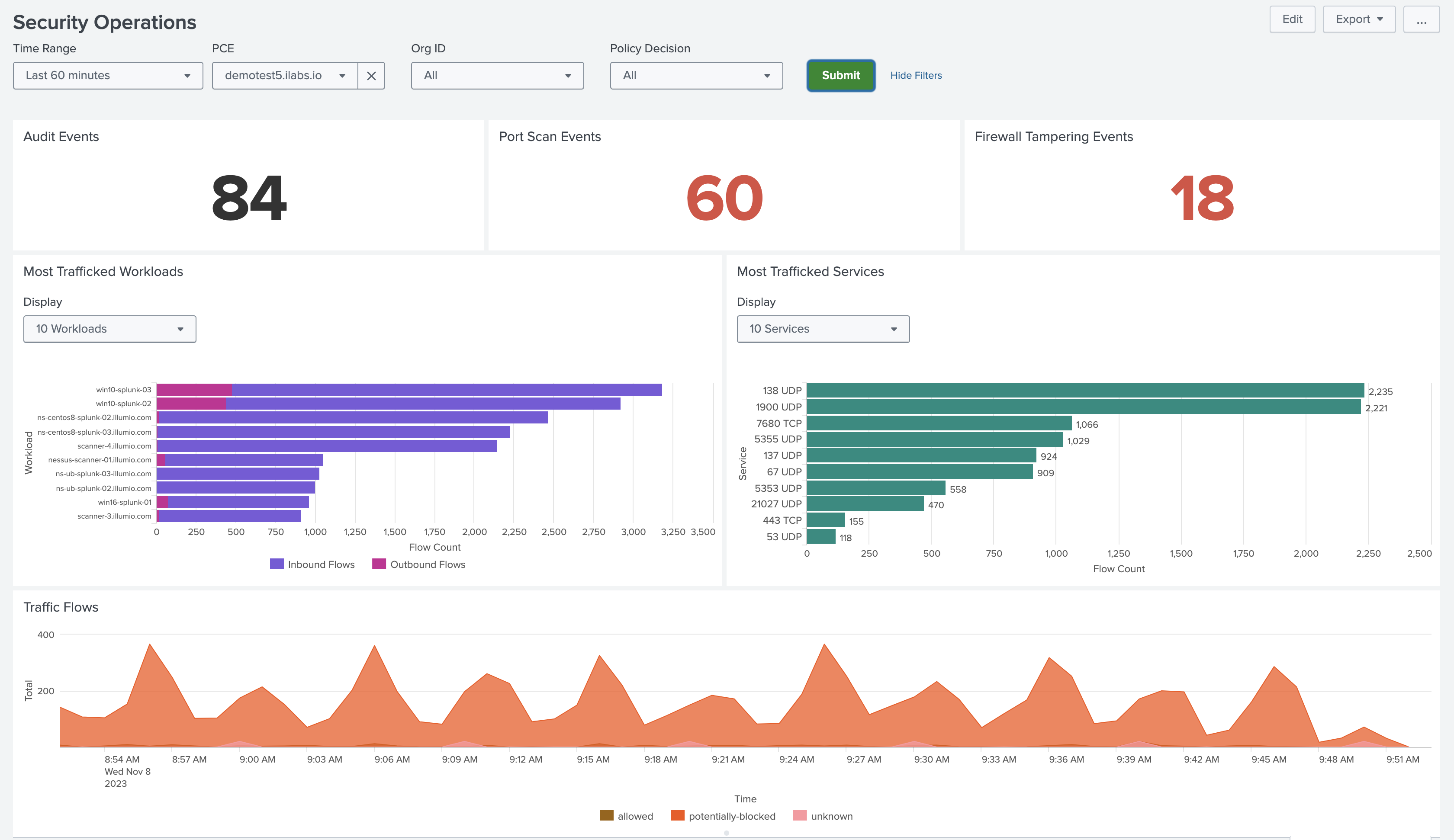
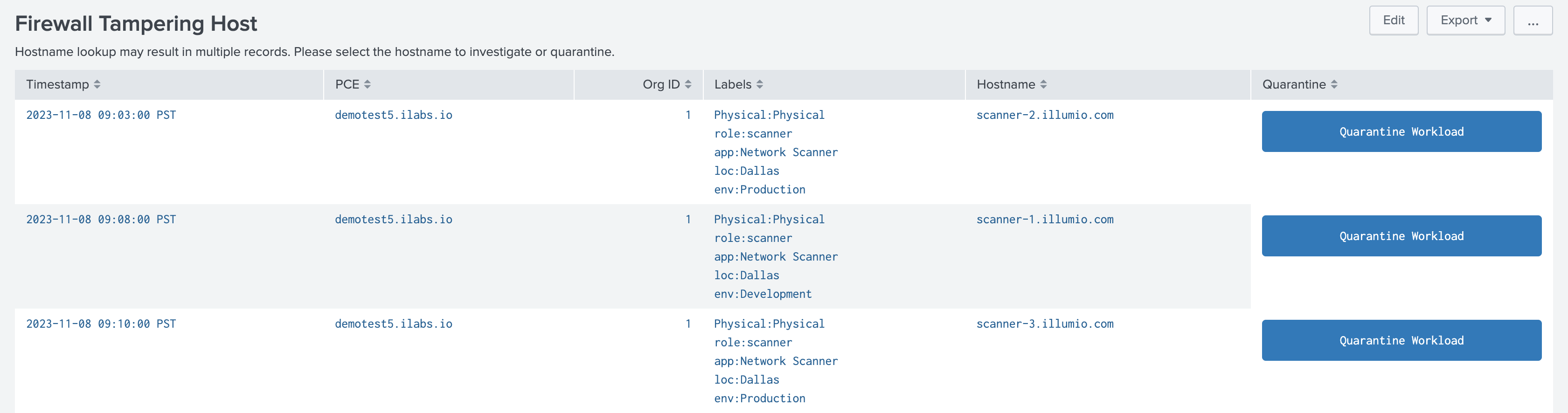
The Port Scan Events and Firewall Tampering Events panels drill down into detailed views of potentially compromised workloads. From these views, you can investigate the triggering events and quarantine the devices using the Illumio Quarantine alert action.
Note
Only users with the Illumio_quarantine_workload role can trigger the quarantine action. Also, note that when the Illumio Quarantine action is performed, the workload will lose all labels and the action will apply the labels that were originally configured on the Illumio Data Input. Th past labels are overwritten to avoid triggering policy rules and to maintain the Quarantine action.
PCE Operations Dashboard
Note
The PCE Operations dashboard is only available for On-Premises deployments.
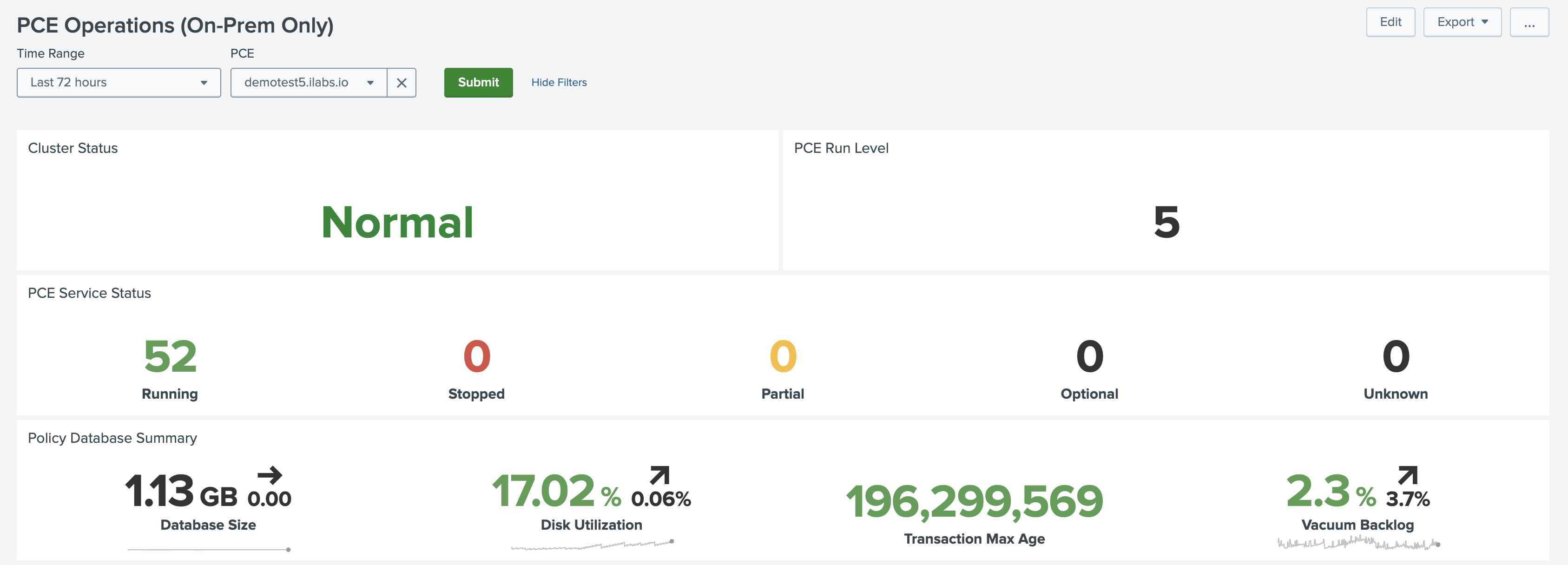
The PCE Operations dashboard shows the status of the PCE cluster. The top panels provide an overview of the whole cluster state, including the Unix run level, service statuses, and policy database metrics.
See the PCE Administration Guide for your version of the Illumio PCE for detailed explanations of these metrics.
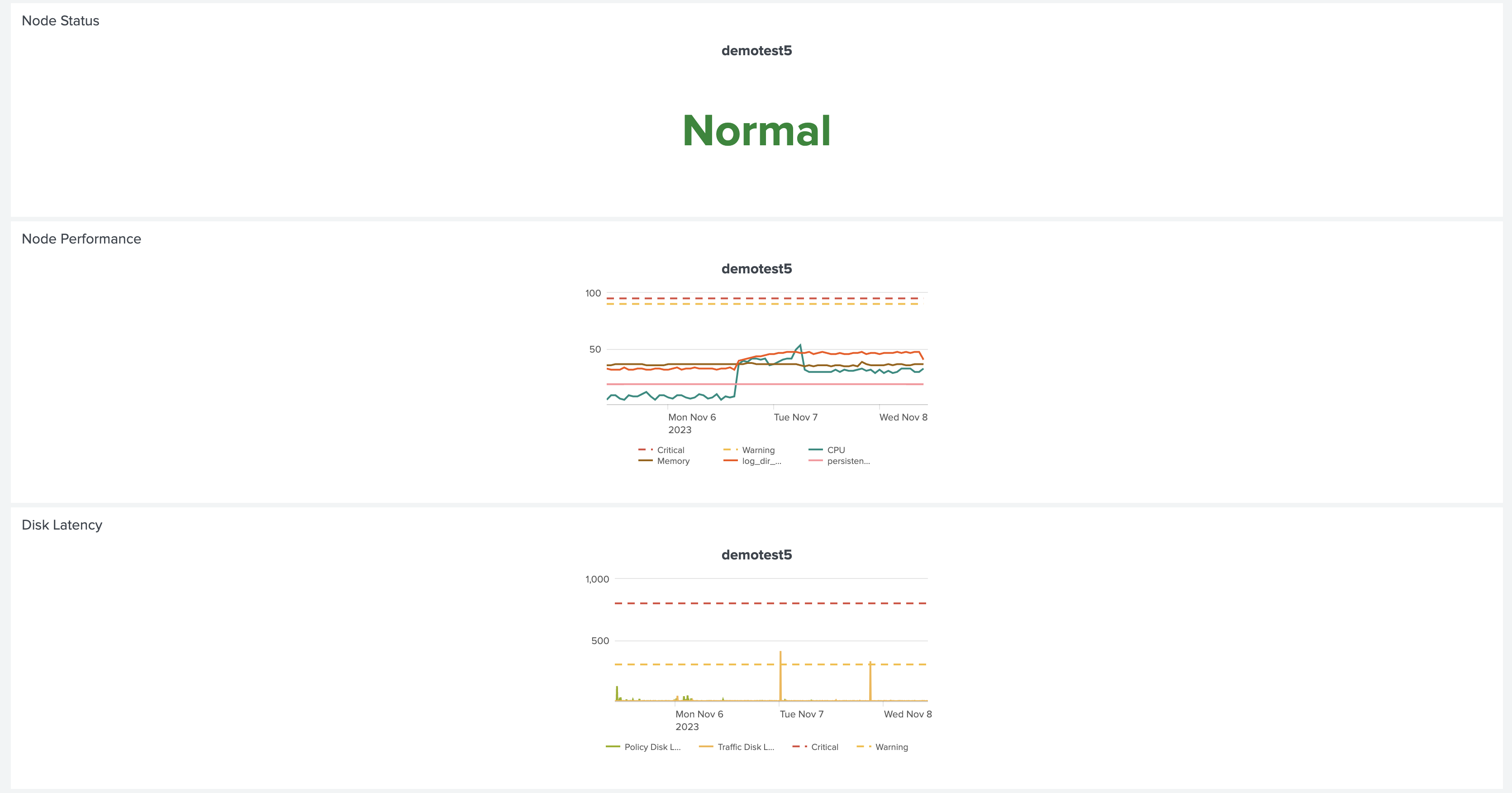
The Node Status, Node Performance, and Disk Latency panels show trellis charts for each host in the PCE cluster. The dashed yellow and red lines indicate warning and critical thresholds for the tracked metrics, respectively.
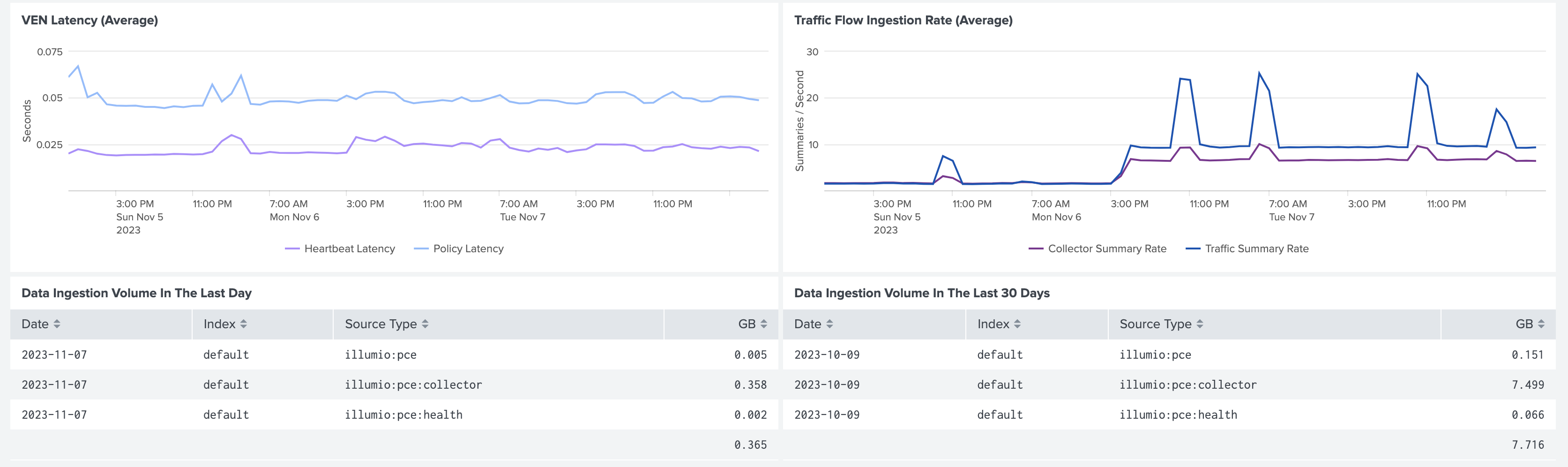
The VEN Latency panel provides an aggregate view of heartbeat and policy latency times for all VENs. The Traffic Flow Ingestion Rate panel shows average traffic flow collection rates to the PCE.
Finally, the Data Ingestion panels at the bottom of the dashboard show the index volume, in gigabytes, broken down by sourcetype.
Note
Only users with the admin or sc_admin roles can view the data ingestion panels.
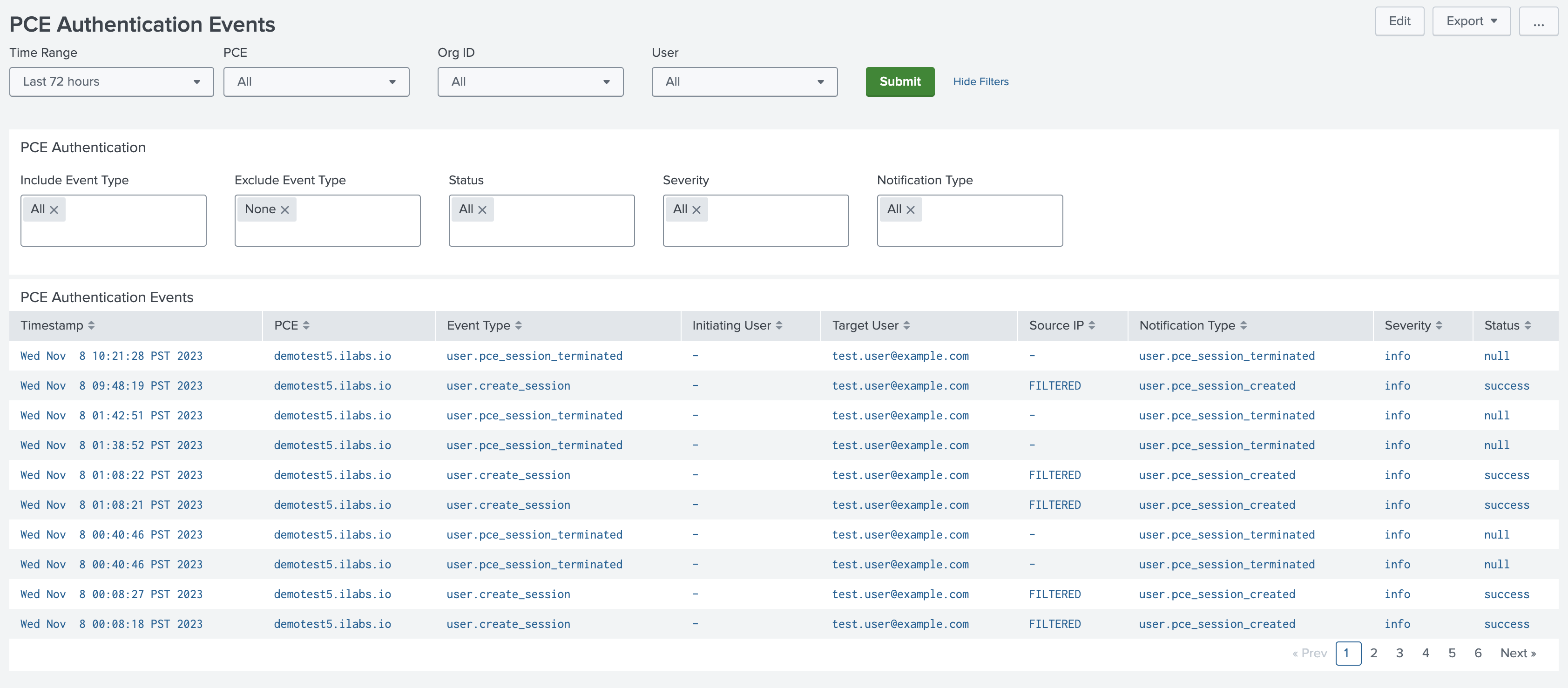
PCE Authentication Events Dashboard
The PCE Authentication Events dashboard shows all authentication and authentication-related events that were made to the PCE. You can filter events by user, type, and severity.
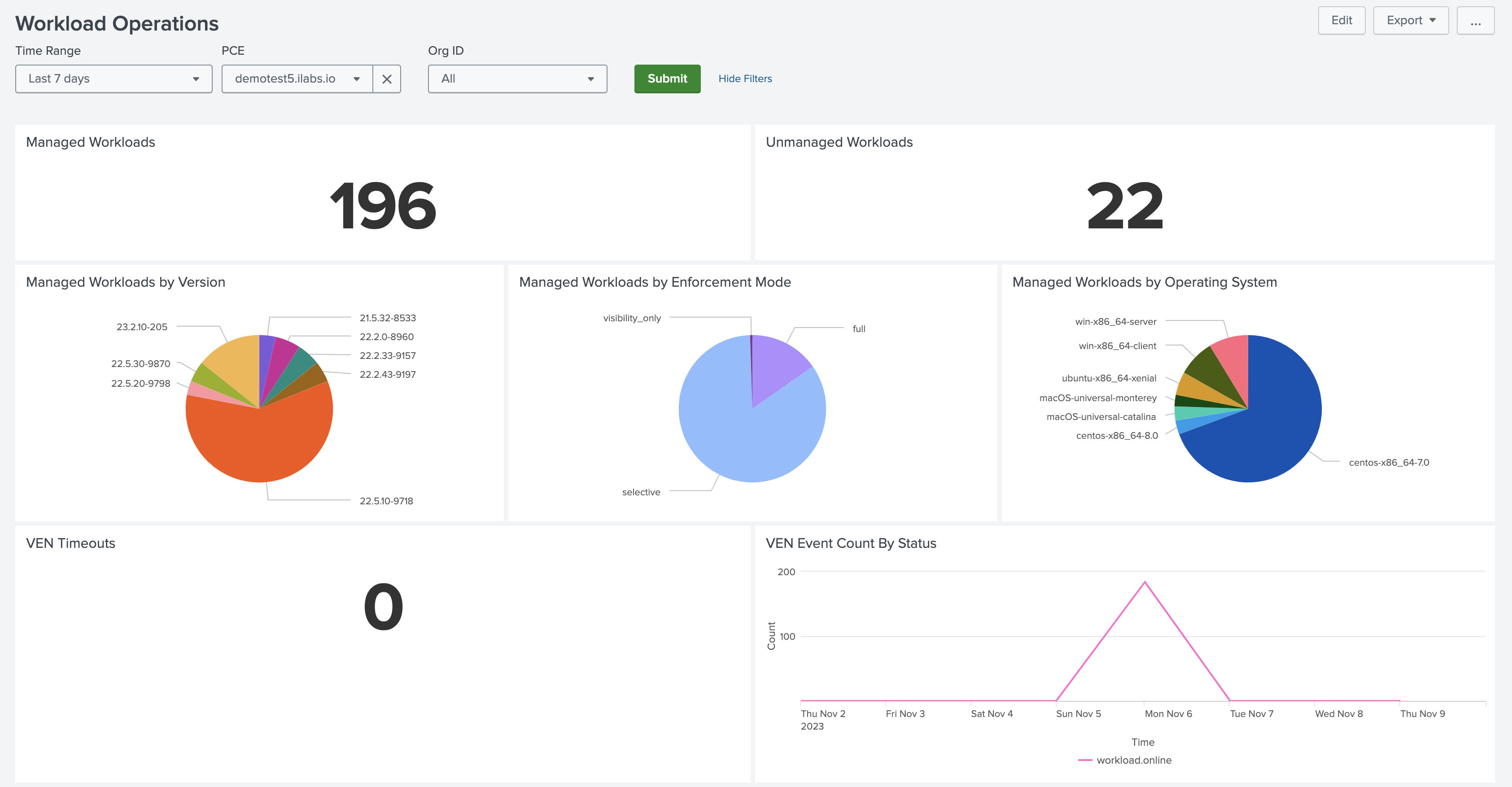
Workload Operations Dashboard
The Workload Operations dashboard shows breakdown of managed and unmanaged workloads by VEN version, enforcement mode, and operating system. It also shows VEN timeouts and VEN/workload events over time.
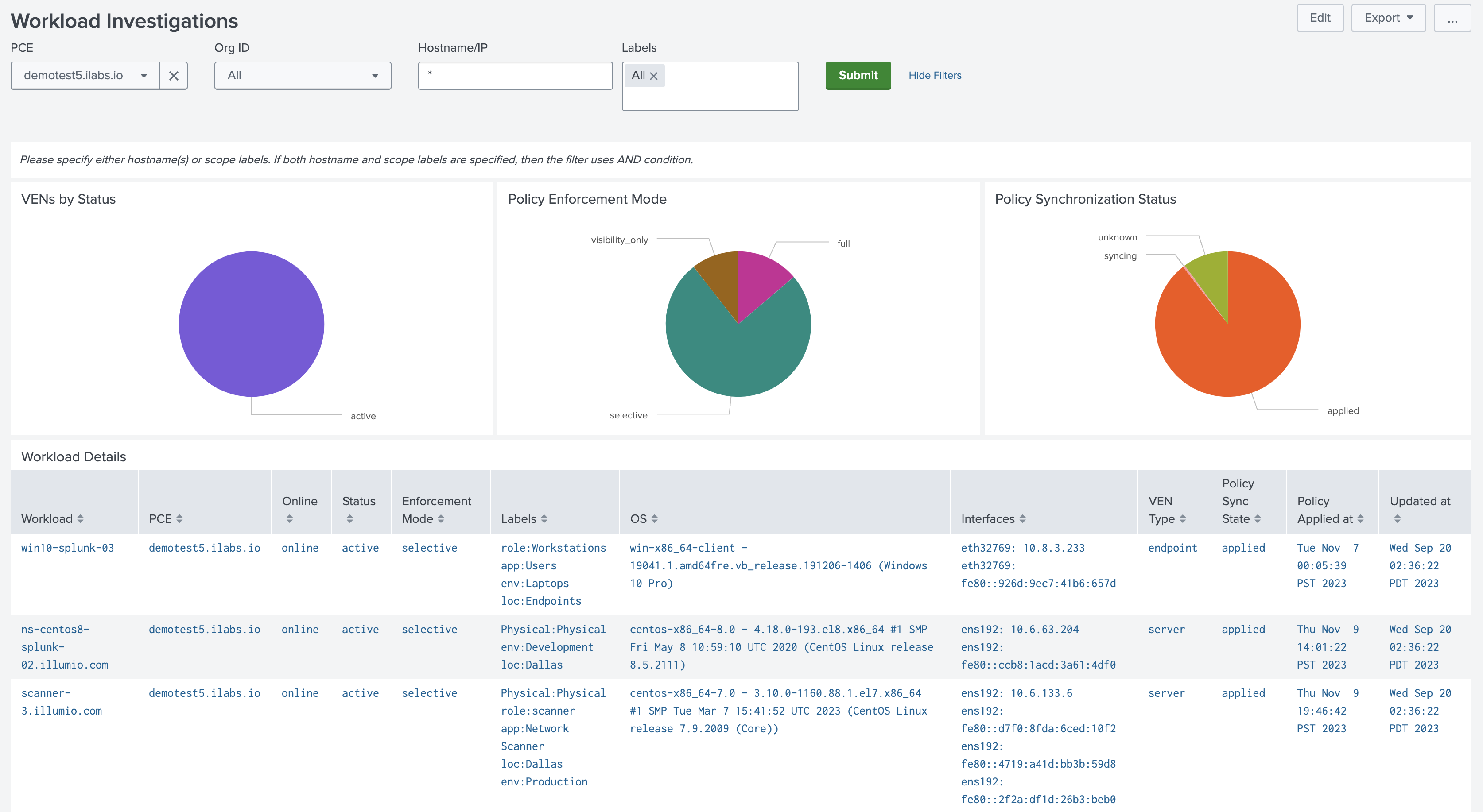
Workload Investigations Dashboard
The Workload Investigations dashboard shows a more detailed breakdown of workload metadata and events, as well as VEN status and policy synchronization status.
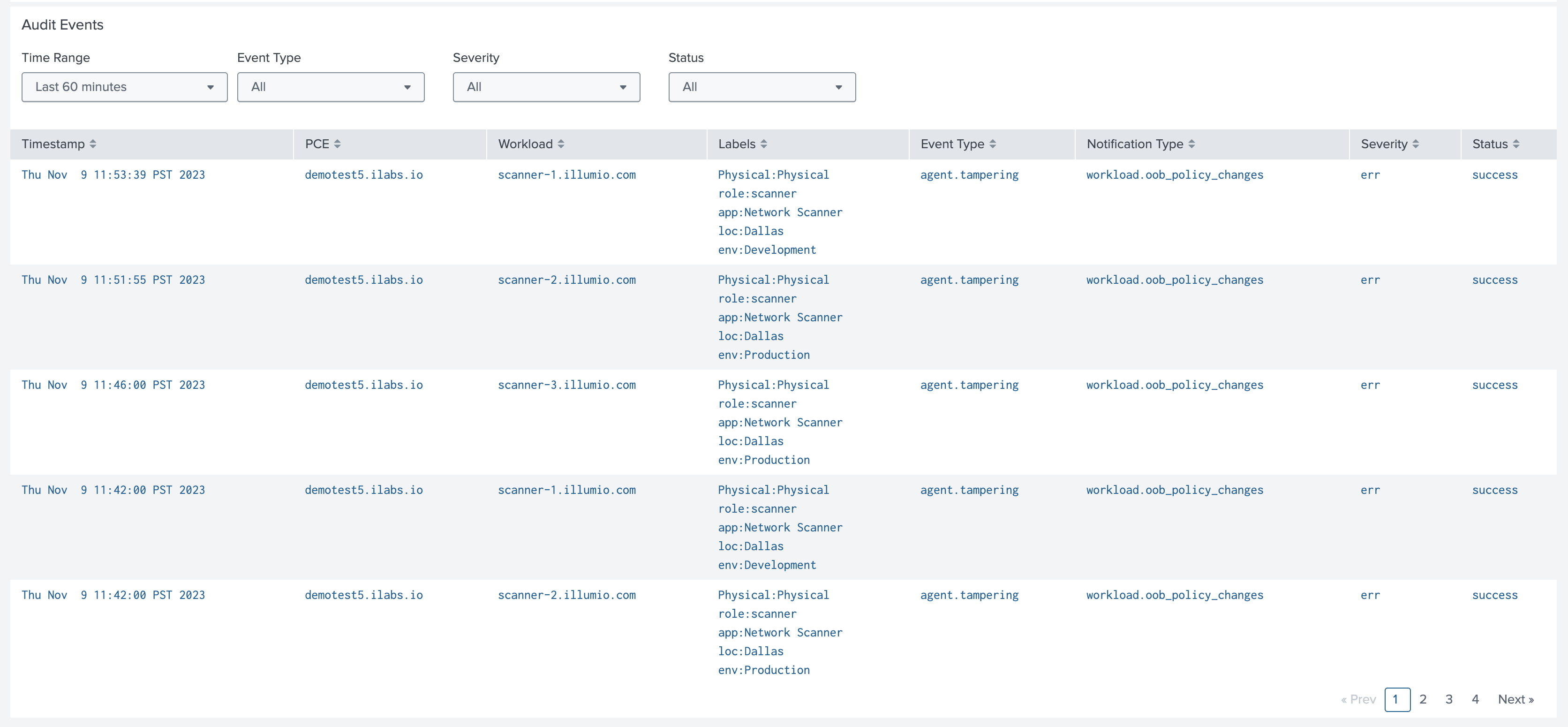
The Audit Events table at the bottom of the dashboard highlights the most recent VEN and workload events on the PCE.
Traffic Explorer Dashboard
The Traffic Explorer dashboard displays traffic flows reported from managed workloads or otherwise uploaded to the PCE. The visualizations show traffic grouped by policy decision, port, and source/destination.
You can filter traffic by source/destination hostname or IP address, assigned labels, policy decision, port, and transport protocol.
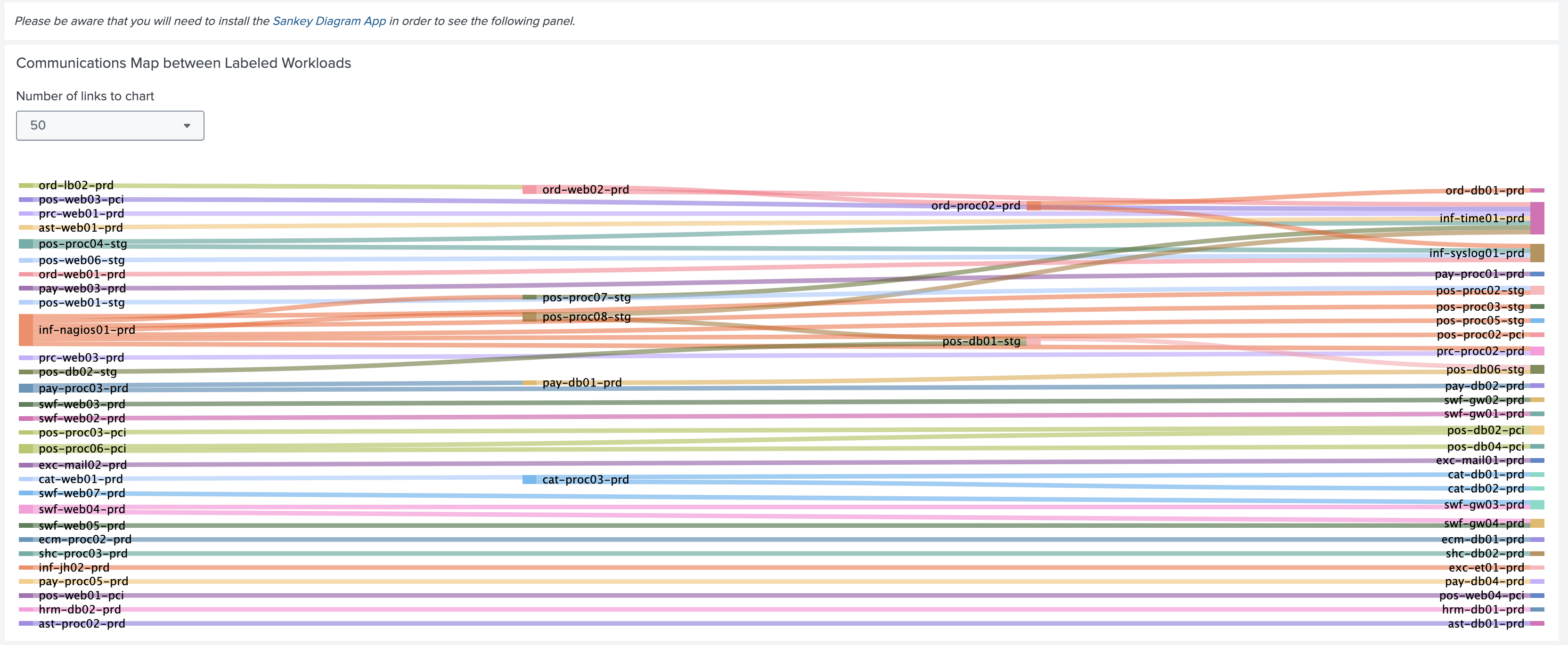
Note
The Communications Map between Labeled Workloads chart shown below uses the Splunk Sankey Diagram Custom Visualization app. You must install the app to render the chart.
Each link in the chart is grouped by source, destination, and destination port. The thickness of the link represents the relative flow count.
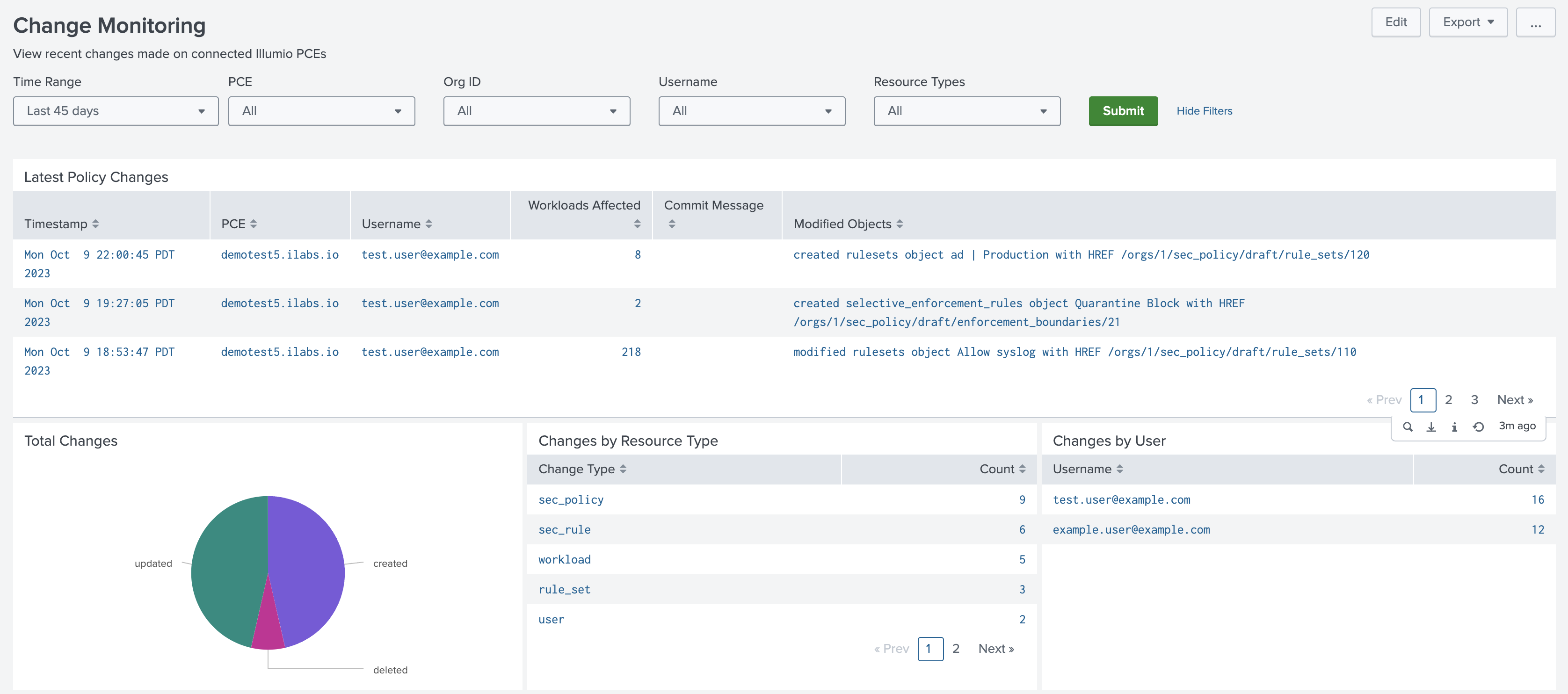
Change Monitoring Dashboard
The Change Monitoring dashboard shows recent security policy changes, and groups auditable change events (creates, updates, and deletes) by count, resource type, and initiating user.
Data Model
The Illumio App for Splunk provides an Illumio data model that can help to improve search performance at the cost of disk space by building a limited index of PCE syslog event fields.
Note
According to Splunk app guidelines, model acceleration is disabled by default.
The model provides the following objects:
Name | Type | Parent | Base Search | Description |
|---|---|---|---|---|
Audit | Root event node | - | illumio_get_index sourcetype="illumio:pce" | Auditable syslog events |
Traffic | Root event node | - | illumio_get_index sourcetype="illumio:pce:collector" | Traffic flow events |
Status | Root event node | - | illumio_get_index sourcetype="illumio:pce:health" | PCE system health and status events |
Status.Policy | Child event node | Status | event_source="policy" | Policy service events |
Status.Collector | Child event node | Status | event_source="collector" | Collector service events |
Status.FlowAnalytics | Child event node | Status | event_source="flow_analytics" | Flow analytics service events |
Illumio data model nodes can be referenced using the tstats command
| tstats sum(Traffic.count) AS flows FROM datamodel=Illumio.Traffic WHERE Traffic.pce_fqdn="my.pce.com" BY Traffic.timestamp, Traffic.src_ip, Traffic.dest_ip
Data Model Acceleration
Note
Enabling or disabling accleration for the Illumio data model requires the accelerate_datamodel capability. The admin or sc_admin roles have this capability by default.
To enable acceleration for the Illumio data model:
Note
If you are using a distributed search head cluster, see Sharing data model acceleration summaries among search heads to avoid rebuilding the summary on each search head in the cluster.
Navigate to Settings > Data models.
Select Illumio App for Splunk from the App dropdown menu.
Click the Edit dropdown under Actions for the Illumio data model.
Click Edit Acceleration.
Check the Acceleration toggle in the dialog and adjust the Summary Range and advanced settings as needed. See the Splunk documentation on data model acceleration for a more detailed explanation of the individual parameters for configuring acceleration.
Click Save. It may take a while to build the summary for the accelerated model.
Click the arrow to the left of the model name to view the progress in the ACCELERATION section.
To rebuild the Illumio data model summary:
Navigate to Settings > Data models.
Select Illumio App for Splunk from the App dropdown menu.
Click the arrow to the left of the Illumio data model name.
Click Rebuild under the ACCELERATION section.