About the Illumio Technology Add-On for Splunk (TA-Illumio)
The Illumio Technology Add-On for Splunk (TA-Illumio) is a Splunk module that receives PCE data for Splunk and performs data normalization. TA-Illumio collects data from the PCE and enriches the data according to the Common Informational Model (CIM). CIM is the native data representation used by Splunk. Illumio data in CIM format can be used easily with Splunk applications such as Splunk Enterprise Security and Splunk App for PCI Compliance.
Data collection from the PCE is accomplished in two ways: through the Illumio ASP REST API and the Illumio PCE syslog.
The Adaptive Response Framework components that are used by Splunk Enterprise Security Suite are packaged with TA-Illumio.
Illumio ASP REST API
TA-Illumio pulls data using the Illumio ASP REST API. For data collection to work, you must set up the API configuration in TA-Illumio to use Data Input, also known as modular input. Data collected from API calls is used to create metadata for workloads, labels, and services. The API data is used to enrich syslog data, such as traffic flow summaries and auditable events.
The following Illumio ASP REST API endpoints are called:
GET /api/v2/orgs/1/workloads/
GET /api/v2/orgs/1/labels/
GET /api/v2/orgs/1/health/
GET /api/v2/product_version
GET /api/v2/orgs/1/sec_policy/draft/ip_lists
GET /api/v2/orgs/1/sec_policy/draft/services
Illumio PCE Syslog
TA-Illumio receives and processes messages directly from the PCE using the TCP configured in Data Input (modular input). The types of messages are:
Events, which are structured JSON messages that represent auditing information.
Traffic flow summaries, which are structured JSON messages that represent enriched traffic flows. Traffic flow summaries contain flows, Illumio labels, and other data about the flow.
PCE System Health messages in syslog format (key-value pairs).
Other syslog messages.
Splunk Index, Source, and Source Types
Index and source type are default Splunk fields used to categorize and filter the indexed data to narrow down search results.
Indexes
In Splunk, raw syslog data is stored in indexes, classified by source type. With TA-Illumio, you can select an index while creating Data Input (modular input). Data collected from that modular input will be collected into the selected index.
If you choose the default index in Data Input, you do not need to perform any further configuration.
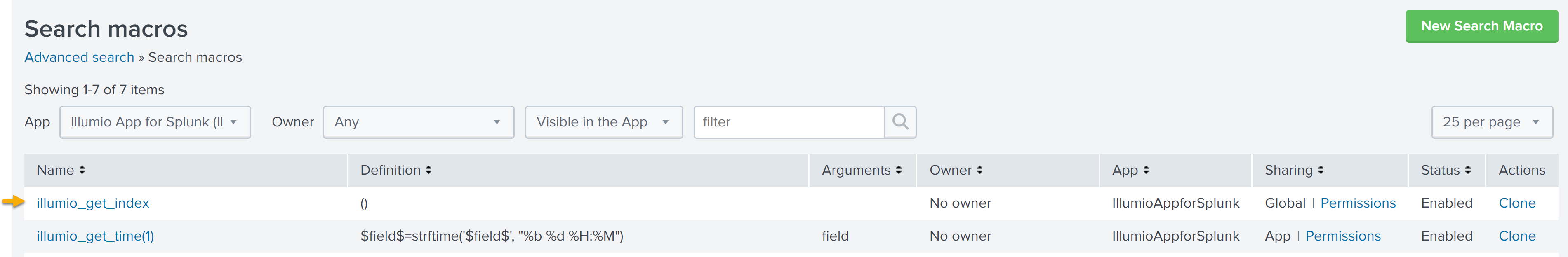
If you choose a non-default index, you must also update the search macros as follows to use the custom index. Otherwise, the dashboards will not display charts.
Use the following procedure to modify the search macro:
In Settings > Advanced Search > Search Macros > App: Illumio App for Splunk, select Illumio_get_index.
In Definition, do one of the following:
If you use the default index, enter open and close parentheses: ()
If you have created a custom index, enter the name of your index in parentheses:
(index=custom_index_name)
Source Type
The following table shows how Illumio data is classified by source types.
Source Type | Description |
|---|---|
illumio:pce | Events collected from the Illumio PCE through syslog. |
illumio:pce:metadata | Workloads, labels, iplists, and services collected from the PCE using REST API calls. |
illumio:pce:collector | Traffic flow summaries collected from the Illumio PCE through syslog. Note that the time stamp for traffic flow summaries is the stamp in the message itself and is not the time when the message is received by the PCE or relayed to Splunk. Effectively, the timestamp of traffic flow summaries is the time when the traffic actually occurred. |
Field Extractions
TA-Illumio extracts fields from various source types using regular expressions.
Data Model and Data Model Acceleration
The app consists of one data model named "Illumio". The data model used in this application is not accelerated by default. If you want to improve the responsiveness of the dashboards, you should enable data model acceleration with a 1-week period. Accelerated data models help improve the performance of the dashboard, but also increase the disk usage on the indexer node.
To enable acceleration:
On the Splunk menu bar, click Settings > Data models.
From the list of data models, click Edit in the Action column of the row for the Illumio data model.
From the list of actions, select Edit Acceleration.
Check the Accelerate checkbox to enable data model acceleration.
Select the summary range and specify an acceleration period of 1 week.
Click Save.
If you don’t need to use the already indexed accelerated data model, the data model can be configured to rebuild from scratch for the specified acceleration period.
To rebuild the data model:
On the Splunk menu bar, click Settings > Data models.
From the list for Data models, expand the Illumio row by clicking the > arrow in the first column.
From the Acceleration section, click Rebuild.
Monitor the status of the rebuild in the Status field of the Acceleration section. Reload the page to get the latest rebuild status.
CIM Mapping
PCE events are mapped to multiple Common Information Model (CIM) data models as shown in the following table.
Event Type | CIM Data Model | CIM Field | Illumio Field |
|---|---|---|---|
sourcetype="illumio:pce" category = "auditable" event_type="user.sign_in" OR event_type="user.login" | Authentication | src | src_ip |
user | created_by.user.username | ||
app | "Illumio" | ||
action | "failure" OR "success" | ||
sourcetype="illumio:pce" category = "auditable" event_type="agent.tampering" OR event_type="agent.firewall_config" | Network Changes | action | "modified" |
status | status | ||
vendor_product | "illumio:pce" | ||
change_type | change_type | ||
src | src_ip | ||
user | created_by.user.username | ||
sourcetype="illumio:pce" category = "auditable" (event_type="*.create" OR event_type="*.delete" OR event_type="*.update") (event_type!="user.*") | Auditing Changes | action | "created" OR "deleted" OR "modified" |
src | src_ip | ||
status | status | ||
vendor_product | "illumio:pce" | ||
user | created_by.user.username | ||
change_type | change_type | ||
sourcetype="illumio:pce" category = "auditable" event_type="user.create" OR event_type="user.update" OR event_type="user.delete" | Account Management Changes | action | "created" OR "deleted" OR "modified" |
src | src_ip | ||
status | status | ||
vendor_product | "illumio:pce" | ||
src_user | created_by.user.username | ||
change_type | change_type | ||
user | resources_changes.resource.username | ||
sourcetype="illumio:pce:collector" | Network Traffic | action | pd |
bytes | tbi + tbo | ||
bytes_in | tbi | ||
bytes_out | tbo | ||
dest | dst_ip | ||
dest_ip | dst_ip | ||
dest_port | dst_port | ||
src | src_ip | ||
protocol | proto |