Overview of Events Administration
This section describes how to do typical administration tasks related to PCE events.
Before You Begin
Illumio recommends that you be familiar with the following technology:
Solid understanding of Illumio Core
Familiarity with syslog
Familiarity with your organizations' Security Information and Event Management (SIEM) systems
About This Guide
This guide provides the following information to administer your PCE deployment:
An overview of events and SIEM integration
Events setup considerations
Event record formats, types, and common fields
Event types by resource
SIEM integration considerations and recommendations
See also the following related documentation:
U.S. National Institute for Standards and Technology's NIST 800-92 Guide to Computer Security Log Management
U.S. Department of Homeland Security National Cybersecurity Center
Notational Conventions in This Guide
Events Framework
The Illumio events framework provides an information-rich, deep foundation for actionable insights into the operations of Illumio Core.
Overview of the Framework
Auditable events are records of transactions collected from the following management interfaces:
PCE web console
REST API
PCE command-line tools
VEN command-line tools
All actions that change the configuration of the PCE, security policy, and the VENs are recorded, including workload firewall tampering.
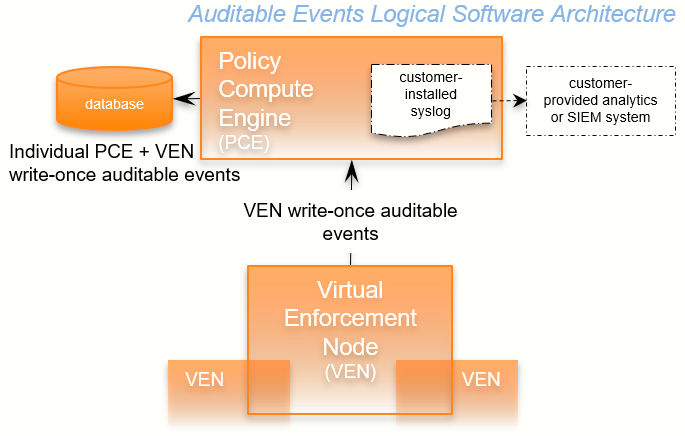
As required by auditing standards, every recorded change includes a reference to the program that made the change, the change's timestamp, and other fields. After recording, the auditable events are read-only.
Auditable events comply with the Common Criteria Class FAU Security Audit requirements standard for auditing.
Auditing Needs Satisfied by Framework
Need | Description | See topic... |
|---|---|---|
Audit and Compliance | Evidence to show that resources are managed according to rules and regulatory standards. | |
Resource Lifecycle Tracking | All information necessary to track a resource through creation, modification, and deletion. | |
Operations | Trace of recent changes to resources. | |
Security | Evidence to show which changes failed, such as incorrect user permissions or failed authentication. |
Benefits of Events Framework
The events framework in the Illumio Core provides the following benefits:
Exceeds industry standards
Delivers complete content
Comprehensive set of event types
Includes more than 200 events
Additional notable system events are generated
Easily accessible interfaces to capture events:
Event Viewer in the PCE web console
REST API with filtering
SIEM intregration
Events are the same across all interfaces
Designed for customer ease of use
Flattened, common structure for all events
Eliminates former duplicate or multiple events for single actions
Streamed via syslog in JSON, CEF, or LEEF format
Create/Update/Delete REST APIs recorded as events
Read APIs/GET requests are not recorded, because they do not change the Illumio Core.
Events Lifecycle for Resources
Illumio resources progress through the lifecycle stages (creation, updating, deletion) and Illumio Core records them with the appropriate event types.
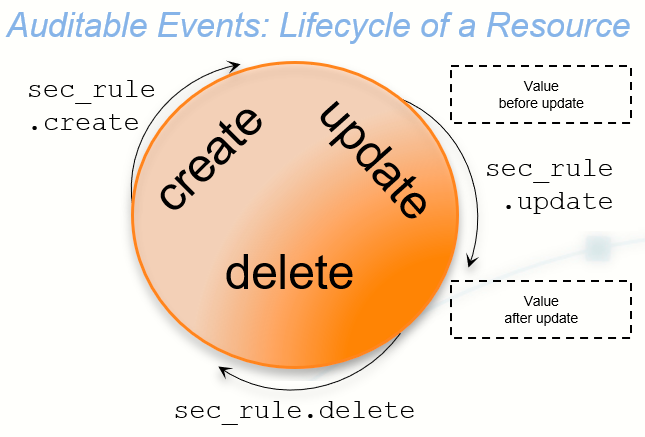
About the Lifecycle
Many resources have a lifecycle from creation through update to deletion. For example, the events related to a security policy rule (identified by the resource name sec_rule) are recorded with the following event types.
sec_rule.createsec_rule.update: Update events record with the values of the resource object both before and after the event for a lifecycle audit trail.sec_rule.delete
Other Resource Lifecycles
Some resources have unique characteristics and do not follow the create-update-delete pattern. For example, workloads have the following event types:
workload.updateworkload.upgradeworkload.redetect_networkworkload.recalc_rulesworkload.soft_deleteworkload.deleteworkload.undelete