Policy Exclusions
In Illumio Segmentation for Data Centers 22.2.0 and later releases, the PCE supports including policy exclusions in ruleset scopes and rules. This topic explains what they are, how they are supported in Illumio Segmentation for Data Centers, and how to add them to your security policy.
Policy Exclusions Described
Using policy exclusions in your Illumio Segmentation for Data Centers policy can greatly simplify the rule writing process. Specifically, using a policy exclusion in a ruleset scope or in rules allows you to replace the inclusion of a large number of required labels with the exclusion of a small number of unwanted labels. Security policy written with policy exclusions can be easier to read and definitely easier to maintain.
Using a policy exclusion allows you to state in your security policy that you want a ruleset or rule to apply to “all except X,” where X can be both labels and label groups. To state this another way, “all except X” means ”All labeled workloads except X” or “All label group objects of a dimension except X.”
You can include policy exclusions in ruleset scopes and in rules actors, namely destinations and providers.
Use Cases
The following examples demonstrate a few common use cases for using policy exclusions:
All environments except Production should be able to pull updates directly from RedHat
The standard jump boxes should be able to connect to all environments except PCI
All applications except Quarantine should be able to connect to Core Services
Support for Policy Exclusions
Policy exclusions are supported by Illumio Segmentation for Data Centers features and in the PCE web console in the following ways:
Illumio Core Feature | Details |
|---|---|
Ruleset scopes and rules | In rulesets and rules, excluding a label creates an “all-but” rule or boundary that applies to all workloads that don't have that excluded label but do have another label of the same label type as the excluded label. For example, your data center supports three environments: Production, QA, and Development. Adding an exclusion for “All environments except Production” means that the rules apply to all workloads with Environment labels minus the Production label. It does not translate to “All workloads except those with the Production label,” which would include workloads that don't have an Environment label. When you create a rule that applies to “All environments but Production," this rule achieves the same affect as creating a rule that applies to the QA and Development environments only. |
Labels | Fully supports except for the restrictions below. See Requirements and Restrictions. |
Label Groups | Label groups are supported for policy exclusions in the same way as labels. For example, you want to create a boundary between Finance applications and all other applications. You create a label group named “Finance Apps” and use it as a policy exclusion. Using label group exclusions is not supported with individual workloads, virtual services, virtual servers, “All Workloads,” the “Uses virtual service only” option, the “Uses virtual service and workloads” option, and container hosts. Additionally, you cannot specify exclusions out of label groups. For example, you have created a label group for the environment “Non-production.” You want to use the label group except you don’t want it to apply to the “Development” environment. You want to create a policy exclusion for the “Development” environment label from the “Non-production” label group. This action is not supported. Selecting to exclude a label group excludes all labels within that group. |
Rule Search and filters | You cannot search by policy exclusions; however, any rules that contain policy exclusions appear in the results of your rule search. In label filters and rule search, entering a label name displays both included and excluded labels with that name. |
App Groups | App Groups > App Groups List > select a group > Rules tab Rules with policy exclusions appear in the Rules tab. |
Policy Check | Rules with policy exclusions appear in the Policy Check page. |
Policy Generator | The PCE does not propose policy exclusions when using Policy Generator to create policy. When using Policy Generator to calculate V-E scores for vulnerabilities (you have the Vulnerability maps feature enabled), Policy Generator won’t work for rules that contain policy exclusions because they aren’t supported in Policy Generator. |
Access Management | Access management (also know as Role-based Access Control or RBAC) detects policy exclusions when determining user access in the PCE. However, you cannot add a policy exclusion to an RBAC role. Policy exclusions are only supported in rulesets and rules. If a ruleset scope includes a policy exclusion based on labels outside the scopes you have permission for, you cannot view or manage those rulesets and rules. For example, a ruleset includes a policy exclusion of “All environments except Production” and you have permission for the Production environment but do not have permission for the Staging environment, you could not view or manage that ruleset. |
Explorer | When writing rules using Explorer, you can choose rulesets containing policy exclusions. You can edit the rules in the ruleset that have exclusions. You can add new proposed rules taking the exclusion scopes into account. However, you cannot add a new policy exclusion to an existing proposed rule or add an exclusion to a new proposed rule. |
PCE web console maps | Policy exclusions are applicable to rules; they are not properties of the traffic links (the lines between the workloads) in the Illumio maps (Illumination Map, App Group Map, and Vulnerability Map). When you click View Rule for any traffic link, you can view the policy exclusions in the View Rule panel. |
Enforcement Boundaries | Policy exclusions are not supported in Enforcement Boundaries. However, you can view policy exclusion rules in the Rules tab of an Enforcement Boundary details page. |
Requirements and Restrictions
Requirements
When specifying a policy exclusion, it must be the same label type as the group it's being excluded from; the following examples are allowed:
All Locations except the New Jersey location
All Applications except Billing
However, this example is not allowed because it specifies different label types – Location vs Environment:
All Locations except those with Development systems
Restrictions
For each label dimension, you can specify an included or excluded label, but not both. The following examples show valid combinations:
App: Swift
App: All but Swift
Env: Prod, App: All but Swift
Loc: EU, Env: All but Prod
You cannot specify both included and excluded labels within the same label type. The following examples are invalid combinations:
Env: Prod, Env: Dev, Env: All but UAT
Env: Prod, App: HRM, App: CRM, App: All but Swift
App: HRM + App: CRM - App:Swift
Loc: EU - Loc: Switzerland
You cannot use policy exclusions with the following objects in the PCE:
Individual (named) workloads
Virtual servers
Virtual services
Container hosts
Create a Policy Exclusion
You can add policy exclusions to the scope of a new ruleset and new rules, or edit existing ruleset scopes and rules. This procedure provides the steps to add policy exclusions to the scope of a new ruleset and in new rules. For detailed information about working with rulesets and rules, see Rulesets and Rules in this guide.
From the PCE web console main menu, choose Rulesets and Rules > Rulesets.
The Rulesets page appears.
Click Add.
The Add Ruleset dialog box appears.
Note
The Scope field appears in the Add Ruleset dialog box only when the PCE is configured to display scopes in rulesets.
If the PCE is configured not to display scopes in rulesets, you can still add a scope with an exclusion after saving the ruleset. From the Ruleset Actions menu at the top right corner of the page, select Add Scope.
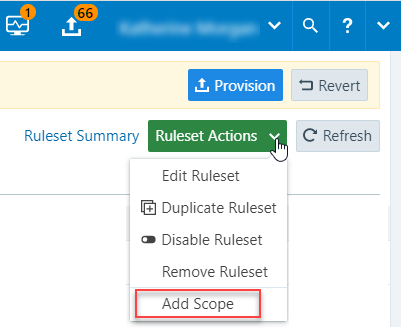
To add a policy exclusion to the scope of ruleset, open the Scope drop-down list and select Labels and Label Groups Except; then, select labels from the list. When done, click Save.
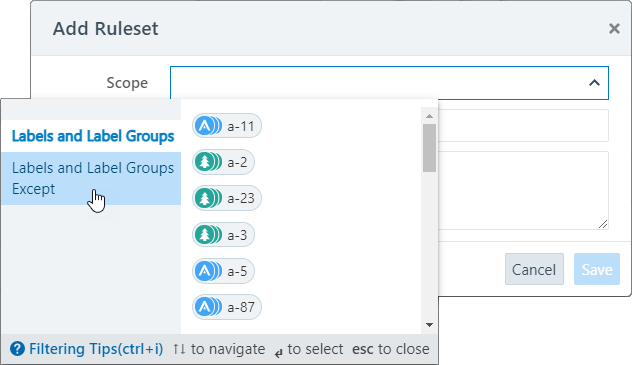
The page refreshes and displays the new ruleset and displays Intra-Scope Rules and Extra-Scope Rules tabs below the scope.
Select Add > Add Intra-Scope Rule or Add > Extra-Scope Rule depending on the type of rule needed. See Rules in this guide for information about these rule types.
An empty row for the new rule appears in the page.
Configure the values for the row. See Rule Writing in this guide for more information.
To add a policy exclusion for either the source or Provider, or both:
From the Select… drop-down list, select the Advanced Options checkbox.
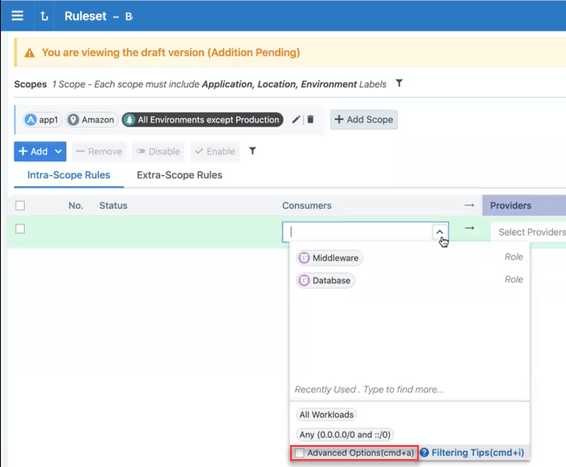
A second panel opens displaying your options for adding exclusions.
Select Labels and Label Groups Except and then select labels to exclude from the right-hand list.
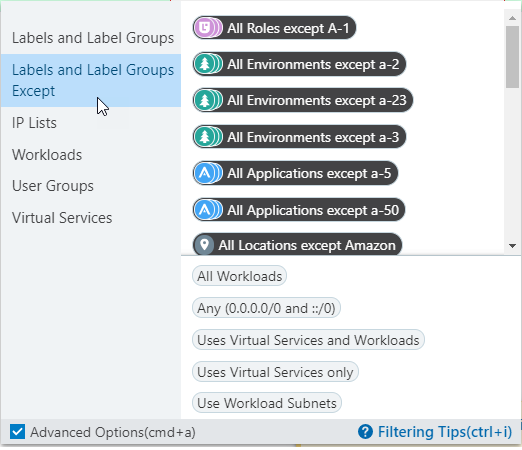
When done configuring the rule, click the Save icon at the end of the rule row. See Rule Writing in this guide for more information about the requirements and steps to fully configure a rule.
Important
If you unintentionally create a rule that has conflicting elements between added labels or label groups and excluded labels or label groups, the PCE web console will display a warning that the security policy as configured might not apply. Specifically, the rule won't have an actual effect on workloads because the rule conflicts with the ruleset scope or the union of the two is will not have an impactful effect on workloads.
For example, you create a ruleset that has the scope “all but the Production environment” and then you create a rule in the ruleset that specifies the Production environment. This rule ends up having no effect because the rule conflicts with the ruleset scope and the union of the two is nothing.