What's New and Changed in Release 24.2
The following new features were added in Illumio Core 24.2.
Rule Hit Count for Illumio Core SaaS
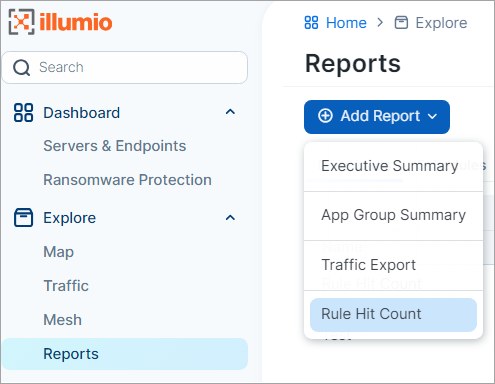
Beginning with this release, the Rule Hit Count feature is now available for Illumio Core SaaS customers. (Requires VEN 23.2.30 or later).
You can add a Rule Hit Count Report through the PCE UI or the Illumio REST API.
The Rule Hit Count Report provides the following:
Policy Compliance: Generate a Rule Hit Count Report to provide evidence that security controls are in place and working effectively, demonstrating compliance to auditors.
Redundancy Removal: Identify unused or less-used rules so you can remove or modify them to reduce redundancy and clutter in your implementation.
Troubleshooting: When network issues arise, identify the rules that were in effect during the relevant traffic flow, allowing you to resolve problems faster and more efficiently.
The PCE and VENs require enablement through the Illumio REST API.
Policy is a new section in the left navigation
The Policy section replaces Rules & Rulesets in the left navigation.
Note
For now, the stand-alone Deny Rules page still appears in the left navigation, but it's slated to be deprecated for future releases. If your Core instance was upgraded to release 24.2.x, Illumio recommends that you migrate your Deny rules from the Deny Rules page to the Policies page and add Deny Rules from the Policies page from now on.
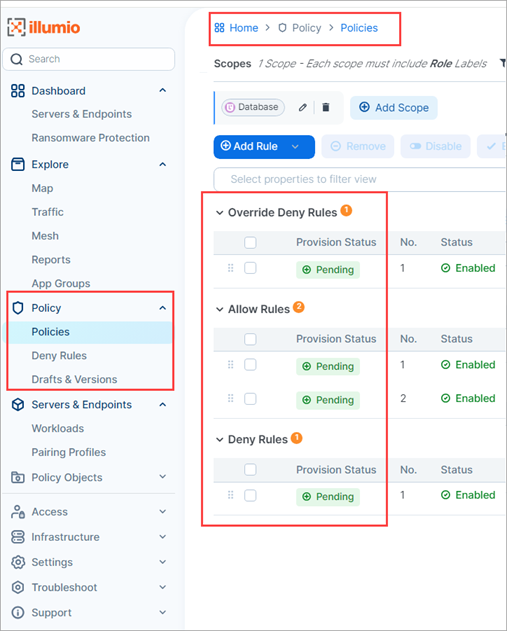
The Policies page differs from Rulesets & Rules in the following ways:
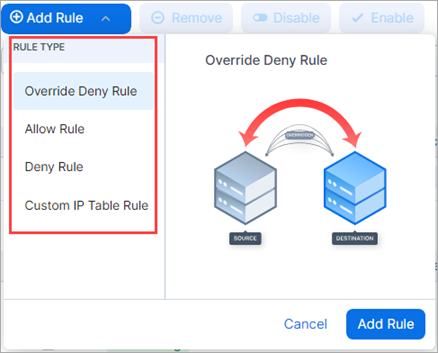
Rule types appear in a list when you click Add Rule.
All rule types can now be added from a single page.
You can add and view Override Deny rules
Rule types are listed in the order of their precedence.
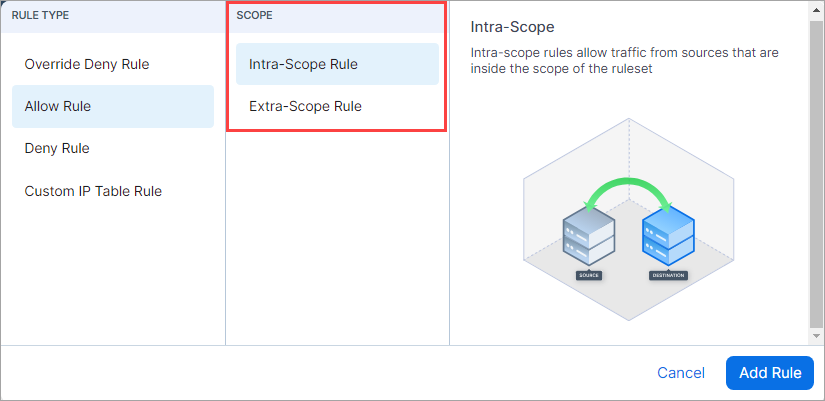
Scope types are listed in a Scope category when you choose Allow Rule.
Override Deny Rules
Note
Override Deny rules require VEN release 22.3.0 or later.
Deny and Override Deny rules are implicitly Intra-Scope rules. Extra-Scope deny rules are not supported currently.
This release introduces Override Deny rules. These are "without exception" deny rules that have precedence over all other types of rules and can't be overridden. Use Override Deny rules to block communication that should always be blocked. For example, if an administrator in your organization creates an Allow rule that would permit communication that should always be denied, having an Override Deny rule in place denying that communication serves as a safeguard. Override Deny rules:
Provide an additional type of granular control for blocking network traffic, helping to ensure that only explicitly authorized communications are permitted.
Block traffic with a type of Deny rule that can't be overridden.
Can be used in scoped and un-scoped rulesets.
Impact the calculation of ransomware protection coverage and V-E scores.
Support the Rule Hit Count feature.
Support compliance with stringent regulatory requirements by enforcing the principle of least privileged access.
Example
Suppose you want to block all traffic between your Production and Development environments except over
splunk-data (9997 TCP)(existing capability).Additionally, you want to block all traffic between all workloads over
SSHwith no exceptions possible (highest precedence; new capability with this release).
Add a Deny rule specifying Production as the source and Development as the destination, blocking all services.
Add an Allow rule specifying the same source and destination, permitting traffic over
splunk-data (9997 TCP).Add an Override Deny rule blocking all traffic between all workloads over
SSH. Because this role has the highest precedence, it can't be overridden by an Allow rule.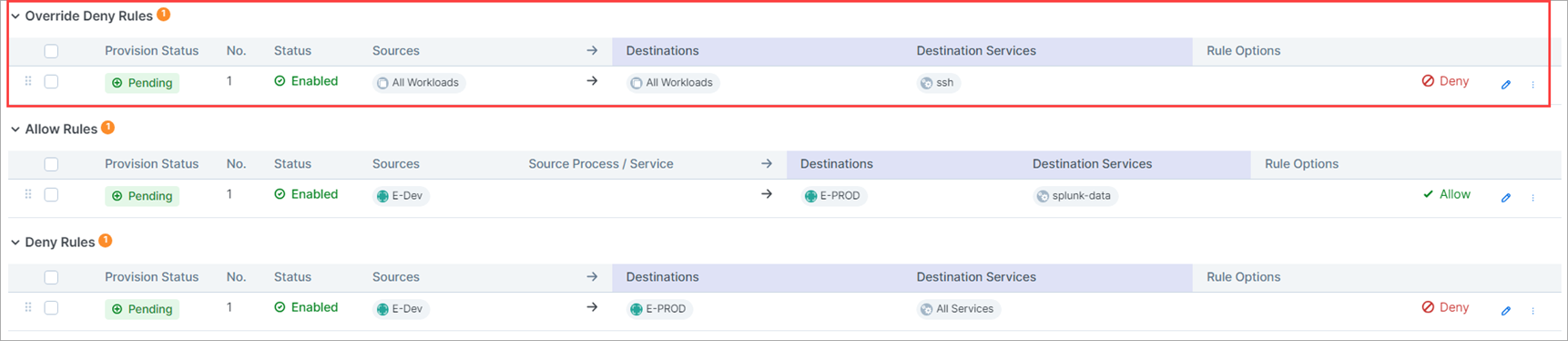
Appearance in Visualization tools
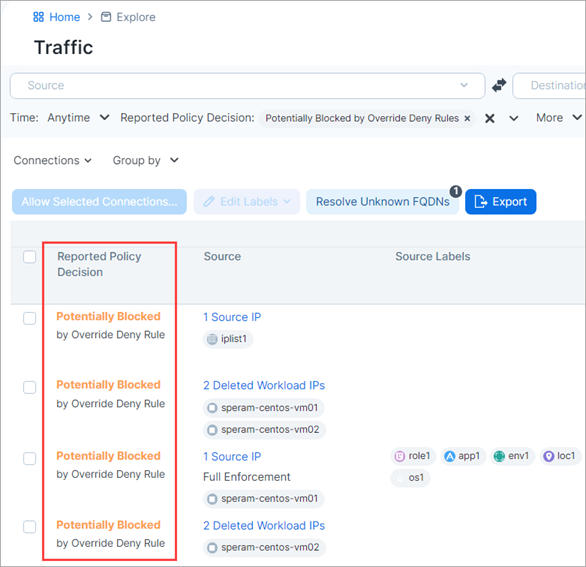
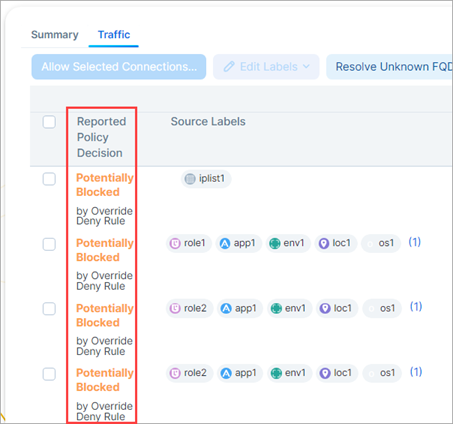
When Override Deny rules block or potentially block traffic in your environment, the policy decision is indicated in the Map and Traffic views in the PCE UI.
As seen in Traffic view
As seen in the details panel in Map view
Impact on key security measurements
Adding Override Deny rules to your security policy affects the calculation of the following security measurements:
Ransomware protection coverage
V-E score
UI Updates for Extra-Scope and Intra-Scope rules
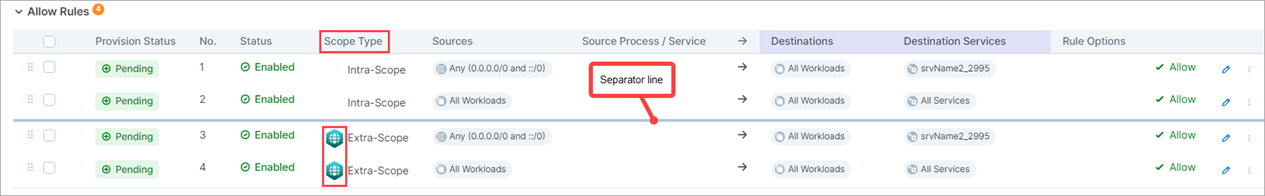
The separate tabs that contained Intra-Scope and Extra-Scope options in previous releases are removed and a new column called Scope Type appears in the Allow rules section of the Policies page.
Extra-Scope and Intra-Scope rules occupy different sections within Allow Rules, separated by a gray line.
You can move rules up or down but only within their respective section.
Extra-Scope rules are now distinguished by an icon.
Only Allow Rules are listed on some pages
The badge  appears in the following areas of the PCE UI where only Allow Rules are listed. Illumio plans to list other rule types in those pages in a future release.
appears in the following areas of the PCE UI where only Allow Rules are listed. Illumio plans to list other rule types in those pages in a future release.
Troubleshoot > Policy Check
App Groups details page > Rules tab
Policy > Policies > Rule Search tab
Get faster query results by turning off Aggregate Explorer Results
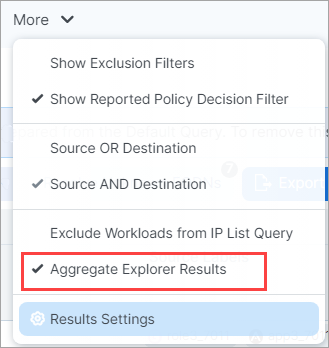
If it's taking too long for query results to appear in the Map or the Traffic table, you can now try to speed things up by turning off Aggregate Explorer Results (on by default) through the More menu. Be aware that turning off aggregation means you may see more duplicate flows, which can result in a slight loss of fidelity in data reporting.
Click More.
Click Aggregate Explorer Results on the menu to turn it off/on.
Click Run.