Configuring the Microsoft Entra ID (Azure AD) Enterprise Application for AUS
Important
By participating in the BETA program for Entra ID for Adaptive User Segmentation (AUS), you agree that your company's use of the BETA version of Entra ID for AUS will be governed by Beta Terms and Conditions.
About this release
The Beta release of MS Entra ID includes these features:
Entra ID Group Sync: Support importing and syncing Entra ID security groups, preserving group names and unique identifiers (such as object IDs or SIDs).
Group Visibility in the UI: Synced Entra ID groups appear in the Illumio Console under the User Groups section with searchable metadata such as group name, unique ID, sync source (Entra ID), and last sync status.
Use Groups in Rulesets: Imported Entra ID groups are selectable in the Sources field when creating rulesets, allowing policies to be applied based on the identity of the logged-in users. Groups should not be used in the Destinations field.
Full Enforcement: If traffic originates from an endpoint where the logged-in user is an Entra ID user in a group referenced by an allow rule, and both source and destination labels match the rule, then the traffic must be explicitly allowed.
Note
To use this feature, you must be in an organization that is in a SaaS cluster with the PPM type.
Prerequisites
To use Entra ID for AUS, you must be running these versions of VEN and PCE:
VEN version 25.2.30 and later
PCE version 25.4 and later
Configuring Entra ID for Microsoft Azure
On the Home screen within the Azure portal, click Microsoft Entra ID.
Navigate to Manage > Enterprise Application, and add a new application called Illumio - AUS.
Navigate to Illumio - AUS Enterprise Application > Manage > Provisioning.
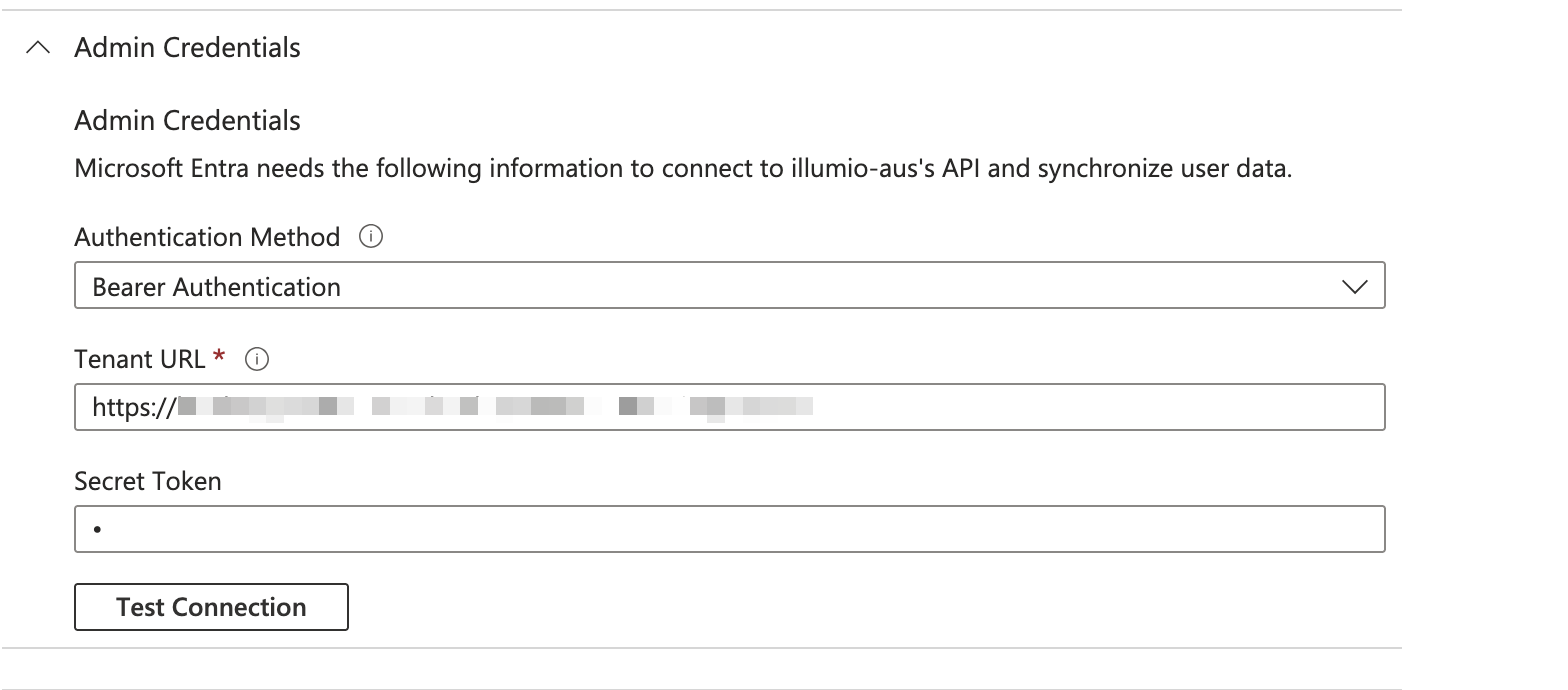
Click Admin Credentials and enter the following information:
Select Bearer Authentication from the Authentication Method drop-down list.
Enter the Illumio PCE URL in the Tenant URL field (for example, {Enter the Illumio PCE URL in the Tenant URL field (for example, {server1.mycompany.com}/scim/orgs/{orgid}/).
Create a PCE API key within the Illumio PCE.
Add the secret token to the Secret Token field using the following format: {api_key}:{secret}.
Navigate to the Mappings section.
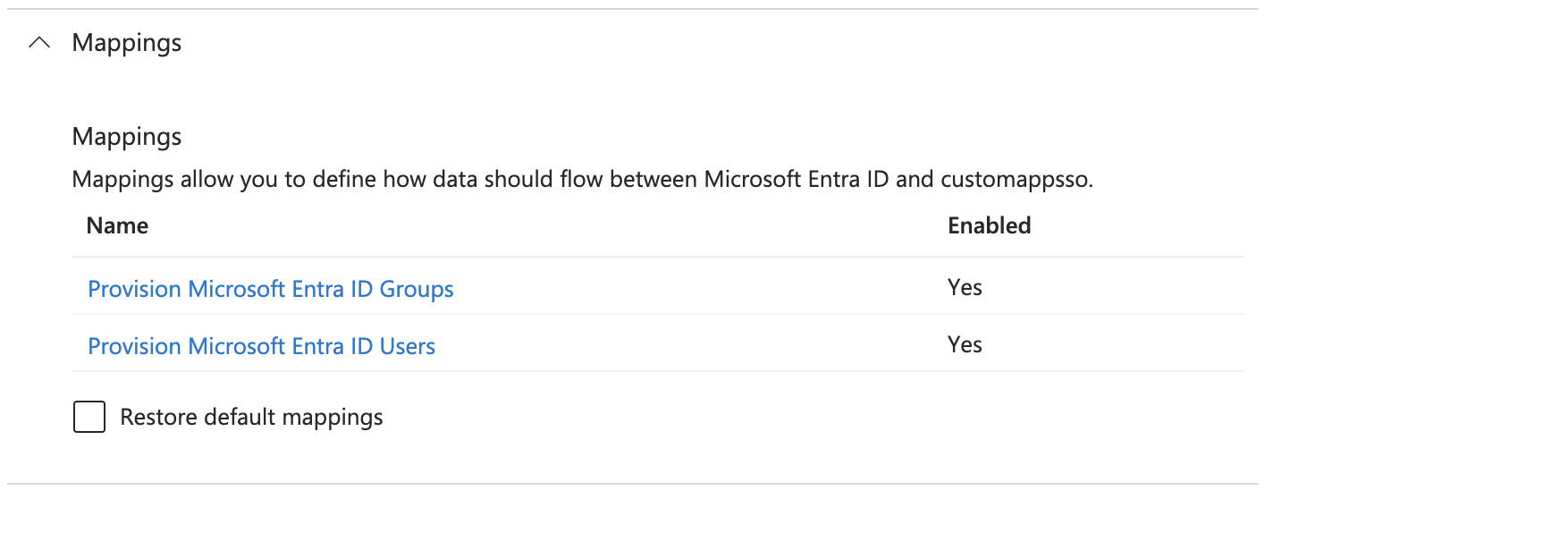
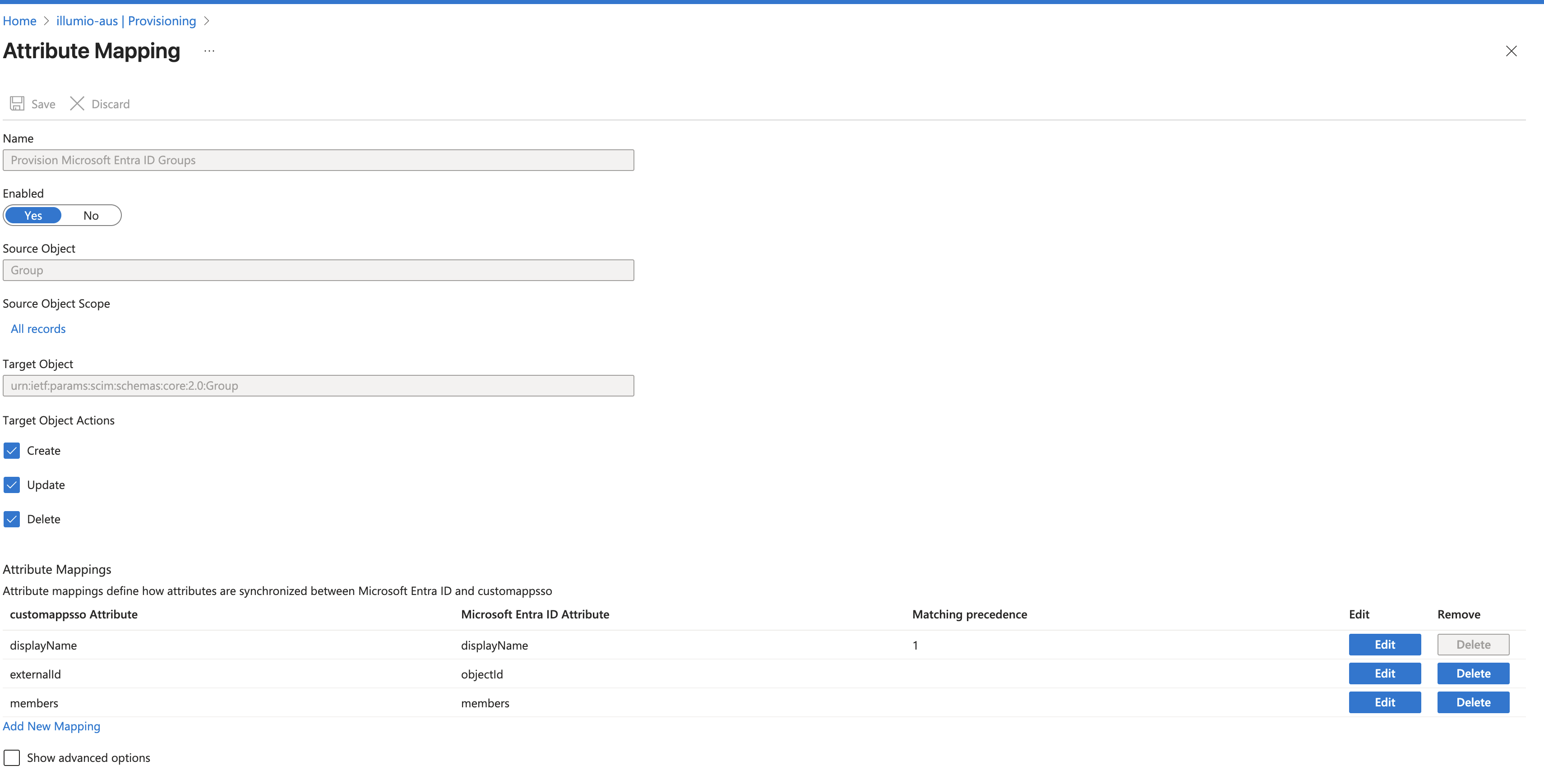
For Provision Microsoft Entra ID Groups, enable the attributes.
For Provision Microsoft Entra ID Users, enable these attributes:
Note
It can take some time for provisioning changes to propagate. This is an Entra ID limitation.

Navigate to Settings, and set the scope to Sync only assigned users and groups.
Navigate to Illumio - AUS Users and Groups and add groups and users.
Limitations for Entra ID and User Groups
Note the following limitations for Entra ID and user groups:
You cannot have a nested group as a member of a group.
You can only write Adaptive User Segmentation policies for users in an immediate group.
Setting Up the PCE for Entra ID for AUS
Enable Entra ID for AUS using the following script:
url="$PCE_URL/api/v2/orgs/$ORG/optional_features"
echo "Getting features for org from $url"
curl -s -u $CRED $url | jq .
echo "Enable feature"
curl -X PUT -u $CRED -s -H 'Accept: application/json' -H 'Content-type: application/json' -d "[{\"name\":\"ugm_support\",\"enabled\":true}]" $url | jq .
echo "Check features for org from $url"
curl -s -u $CRED $url | jq .After Entra ID provisioning starts, Entra ID will periodically push group and user information to the PCE, and the information will eventually be populated within Policy Objects > User Groups:
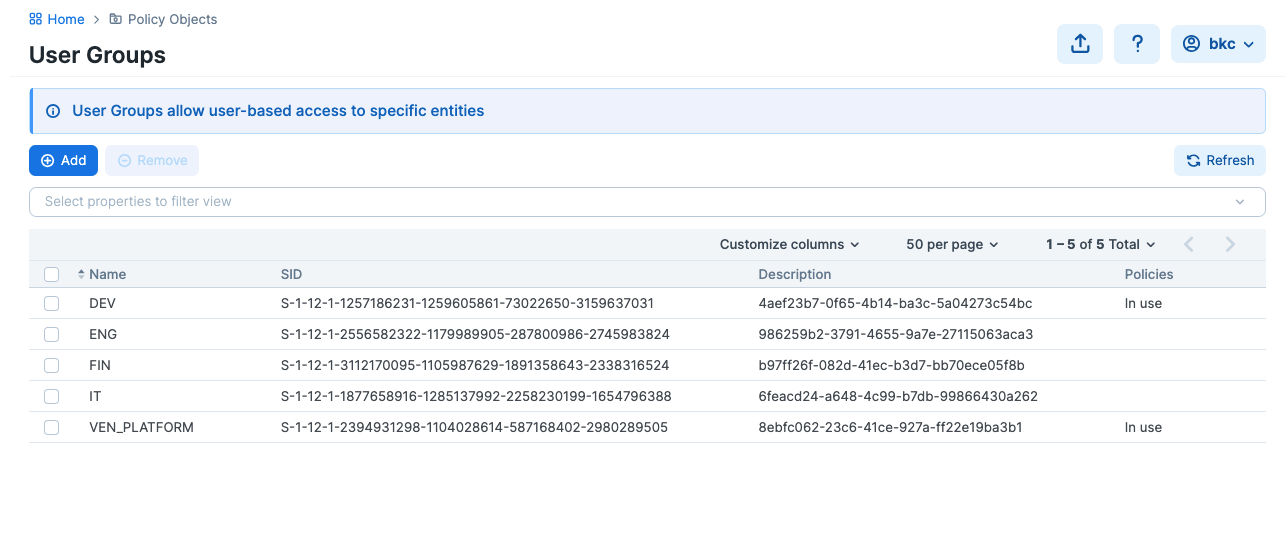
After the User Groups list is populated, you can use the user groups to write policies.
Here is an example of a policy that allows egress traffic from all workloads with users in the DEV user group to all destinations on port 80/TCP:
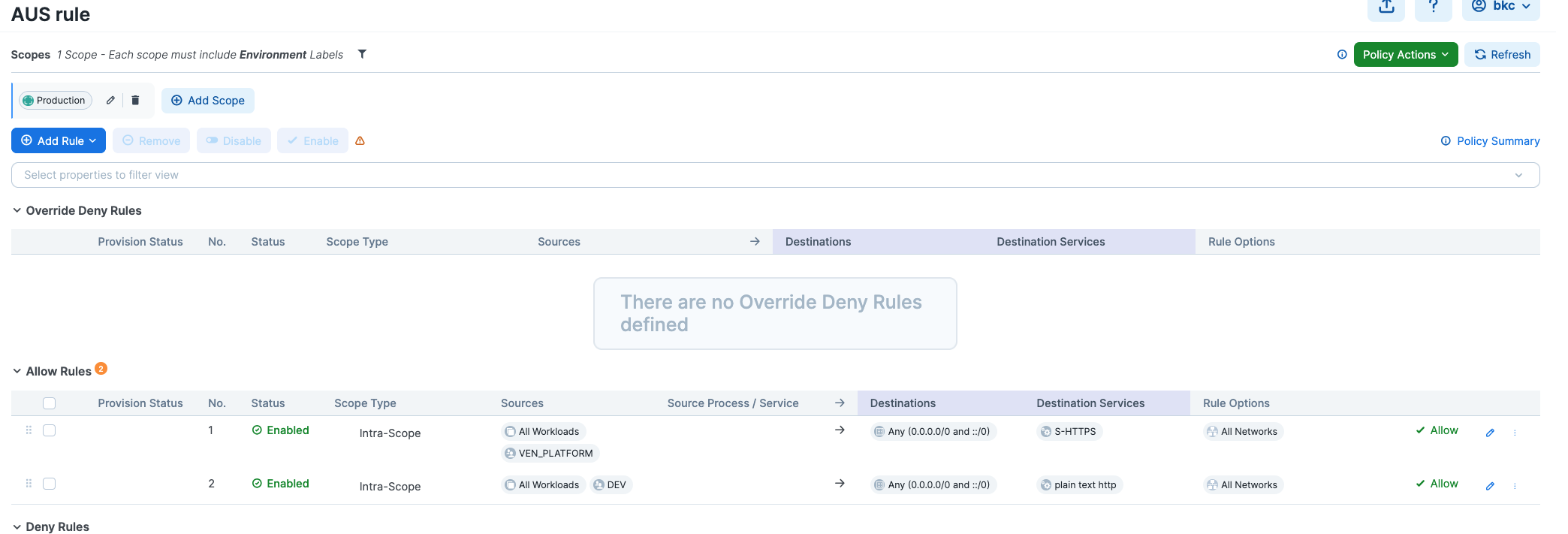
Setting Up the VEN for Entra ID for AUS
Important
For Entra ID for Adaptive User Segmentation, the source workloads must be where the user in a specific user group is logged in and the workload must have a Windows VEN version 25.2.30 or higher on it.
Log in to the workload where the VEN is installed using Entra ID credentials and the flow will be enforced. Entra ID provisioning does not take effect immediately in the VEN so you may have to log out and log back in.