Provide Access to the Quarantine Workload Action
By default, users do not have access to the Quarantine Workload action either in the Splunk App or in Adaptive Response Action.
To enable a Splunk user to take quarantine actions on Workloads, grant the user the Illumio_quarantine_workload role and the admin role. Only local users can be granted this role. SAML users cannot, because their roles are controlled by an external system.
Click Settings > Access Control.
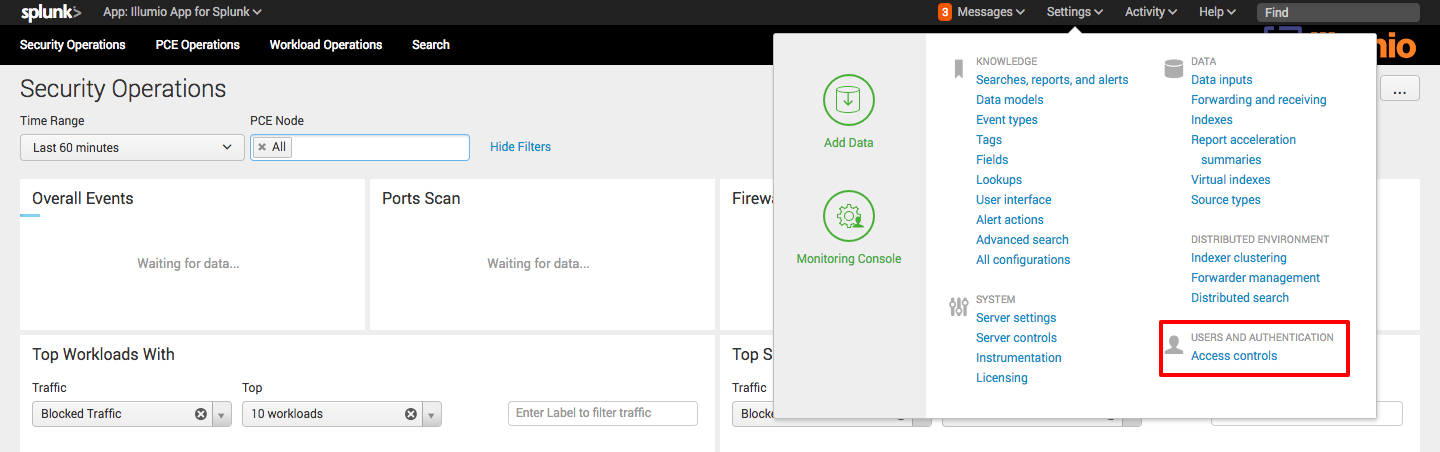
Click Users.
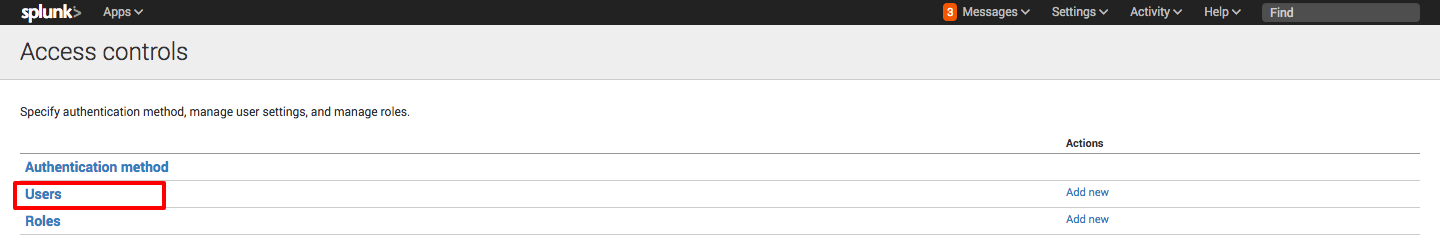
Click the username to which the role needs to be granted.
In the Role section of the edit screen, grant the required roles.
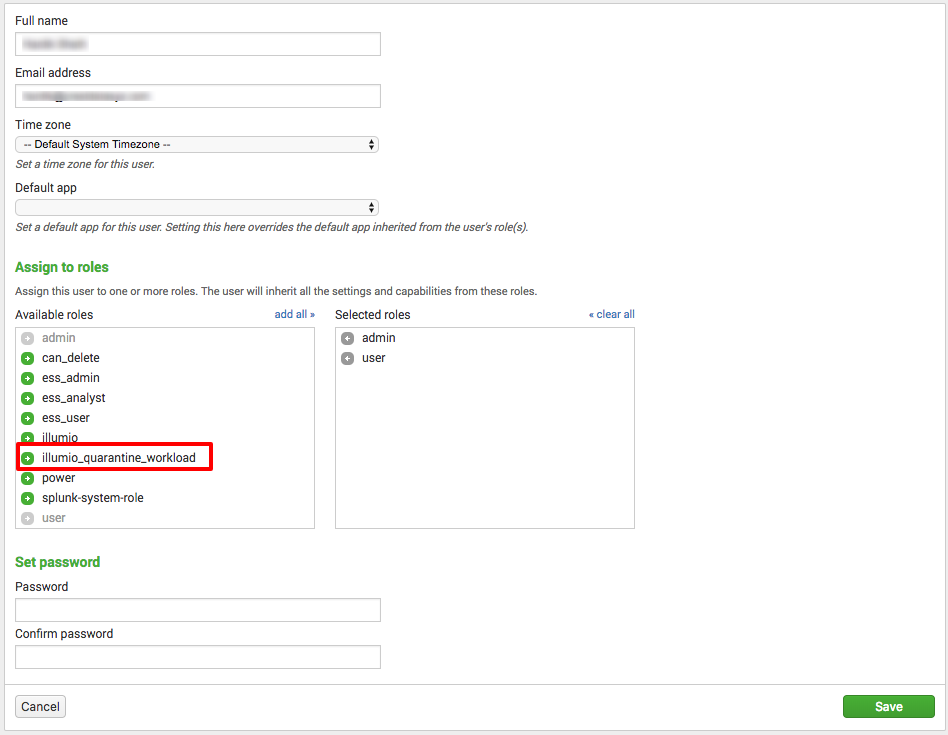
Click Save.
Quarantine Workloads Using Splunk Core Alert Actions
If Splunk Enterprise Security Suite (ESS) is not installed in your Splunk infrastructure, the Illumio App for Splunk offers a way to monitor and take action on the events reported by analytics on Illumio PCE logs.
To achieve this, the Illumio Add-On for Splunk leverages the custom alert action to quarantine the workload. These actions are available on the drilldowns from the main dashboards.
Quarantine Workload Using Enterprise Security Suite
Splunk provides the Splunk Enterprise Security Suite (ESS), which leverages Splunk’s Adaptive Response Framework and allows administrators to monitor and manage threats and incidents directly from Splunk apps. It has rich dashboards that help monitor incidents and take actions on these incidents.
Splunk Enterprise Security Suite is extendable by adding a compatible Module App (Adaptive Response Add-ons) for a particular domain or technology. The Suite detects configurations in these Adaptive Response Add-ons and helps monitor and take actions on the incidents reported by these Add-ons.
The Illumio Add-On for Splunk (TA-Illumio) is one such module for Splunk Enterprise Security Suite. It leverages the Splunk Adaptive Response Framework and empowers system administrators to monitor and take actions on incidents reported by analytics on Illumio PCE events or logs from the Splunk Enterprise Security Suite dashboards.
When using the Splunk Enterprise Security (ES) suite, the Illumio Splunk TA can be installed on a single ES Search Head (SH), or on both an ES SH and an associated ES Search Head Cluster (SHC). This allows the Adaptive Response to be invoked from any installed TA location. The Illumio data is stored on the indexers only, and not on the search head nodes, so the data is not duplicated. If the TA is installed only on a single ES SH, the data is normalized for the associated SHC.
The Incident Review dashboard:
 |
As a part of the Adaptive Response Framework, Splunk has enhanced this Incident Review dashboard in the Enterprise Security Suite app, which provides the option to take actions on these notable events.
To view the notable event details, expand the left arrow for that notable event. To execute alert actions manually for each of the notable events, click Run Adaptive Response Actions for the notable event and select the specific Alert Action.
 |
When you click Run Adaptive Response Actions for a notable event, a menu appears that lists all of the standard and custom actions. This list is created by reading the alert_actions.conf files of all the installed apps on the Splunk instance. Users can select multiple actions on this popup menu and run them for that notable event.
 |
 |
 |
When these actions are run, each selected corresponding action is invoked from alert_actions.conf.
Quarantine Workloads from the Illumio Splunk App
If you have both the admin role and the Illumio_quarantine_workload role, you can quarantine workloads from the Illumio Splunk App by clicking the Quarantine button, which appears on the following dashboards:
Port Scan (on the Security Operations dashboard)
Firewall Tampering (on the Security Operations dashboard)
If the Quarantine button is greyed out, then you do not have adequate permissions to quarantine workloads. See Access to Quarantine Workload Action.
 |