What's New in 25.21
Before you upgrade to Illumio Console 25.21, familiarize yourself with new features in this release.
Hybrid Policy Support
After hybrid policies are enabled, your on-premises and applicable cloud networks assume to use non-overlapping private IP subnets. Any policies between on-premises and cloud workloads are distributed to the appropriate on-premises workloads and cloud resources. Within each cloud, Illumio Console determines the network segregation with VPC peering detected. Currently, supported clouds are AWS and Azure.
Hybrid policy support is available only to applicable customers. For details, contact your Illumio representative.
Rule-Based Labeling Enhancements
For details about Rule-Based Labeling, see Rule-Based Labeling.
This release introduces the following enhancements to the Rule-Based Labeling feature:
Support for Regular Expressions and NOT operators
Regular Expressions
Regular Expressions (regex) allow you to define complex patterns to precisely match workloads in your environment. This precision is particularly useful when you're trying to find and label workloads that have multiple attributes. www
NOT Operators
NOT operators allow you to refine search queries by excluding certain values. You can combine NOT operators with other search operators (like AND, OR) to create complex queries that precisely target the desired information while excluding irrelevant data.
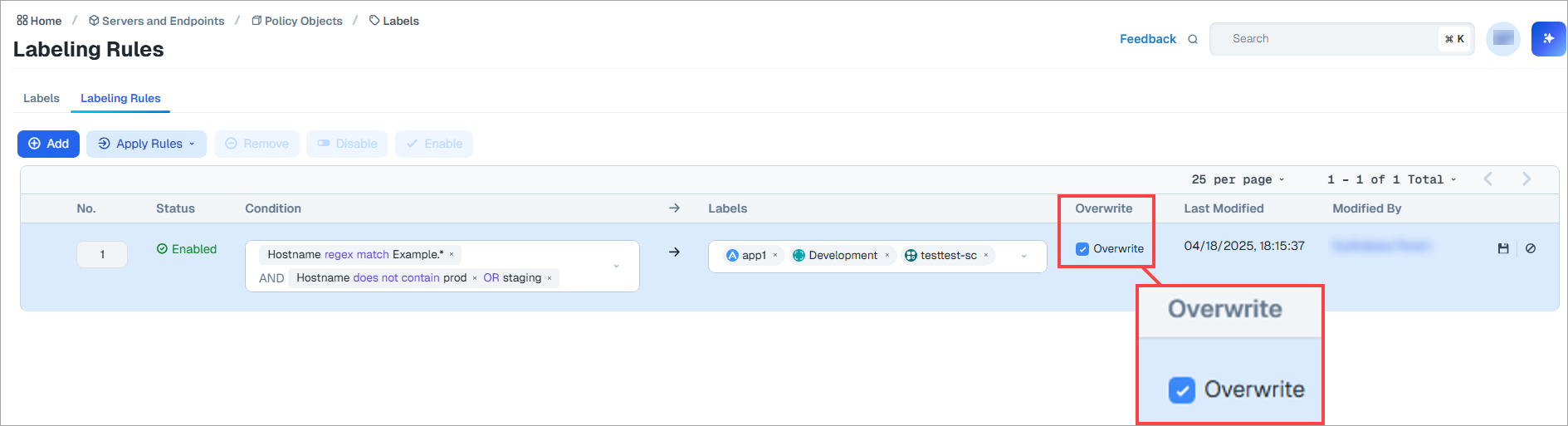
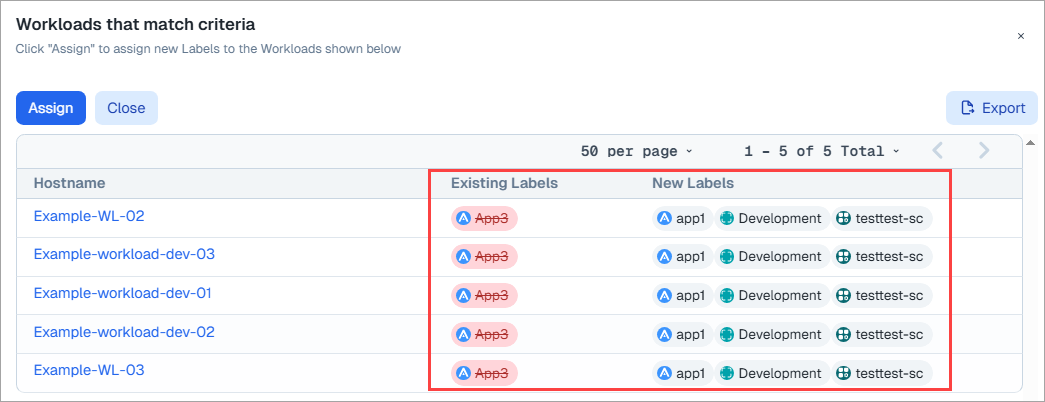
Support for Overwriting Existing Labels
The Overwrite option allows you to replace labels already assigned to workloads with new labels of the same type. For example, if your labeling rule is set to assign an Application label to matching workloads, selecting this option ensures that any Application label already assigned to these workloads is overwritten by the new Application label when you click Assign.
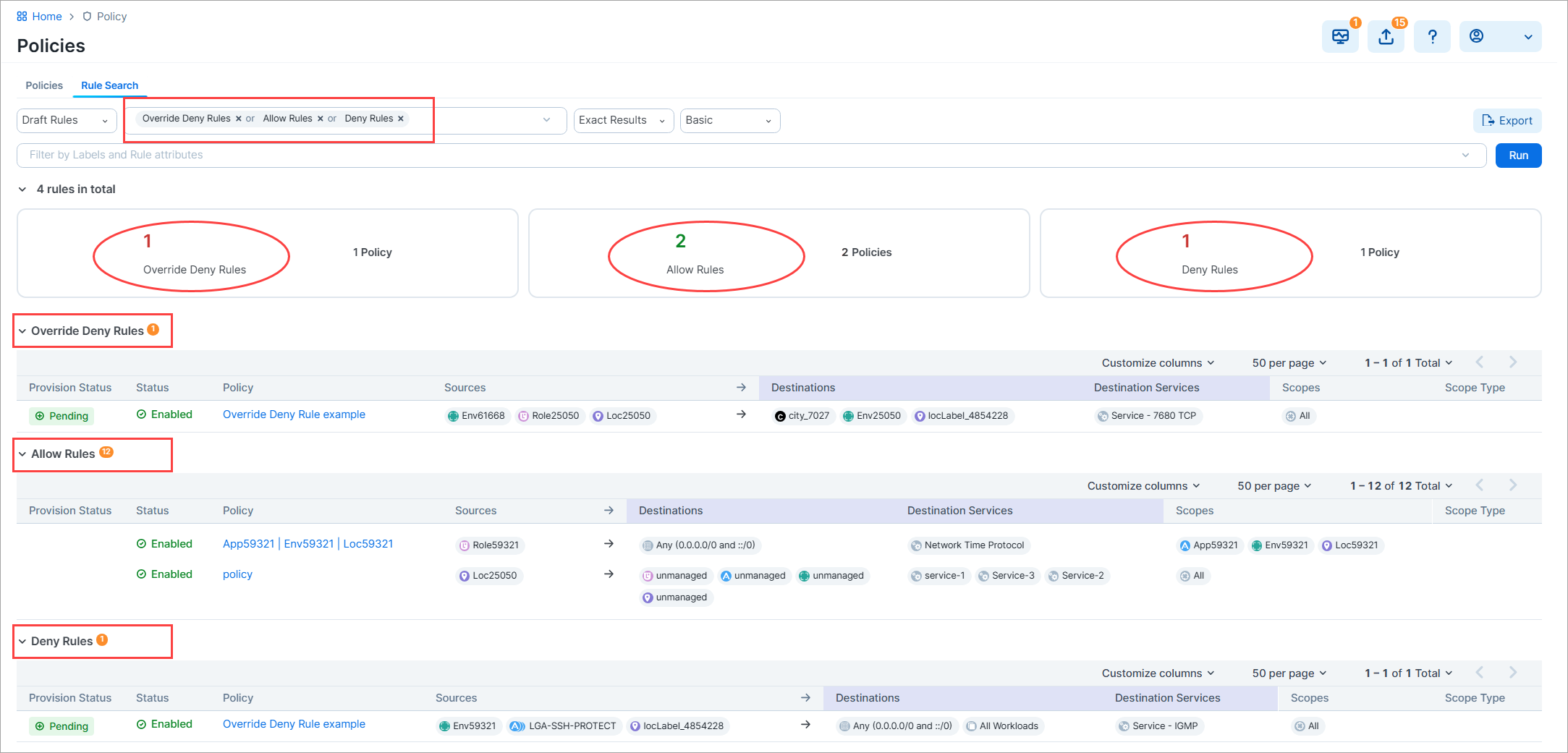
Rule Search now supports Deny and Override Deny rules
You can now search for any combination of Allow, Deny, and Override Deny rules from the Policies > Rule Search tab. Previously, Rule Search was limited to Allow rules. Also, the total number of each rule type is prominently displayed just below the search filter.
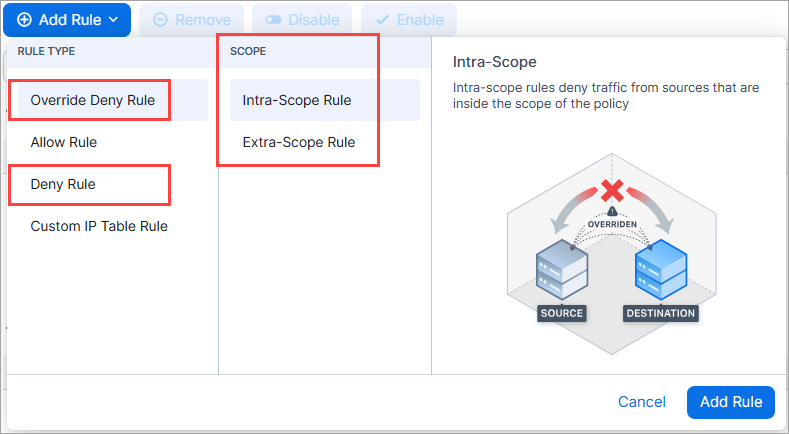
Deny and Override Deny rules now support Intra- and Extra-Scopes
You can now specify an Intra-Scope or Extra-Scope scope when you add Deny and Override Deny rules. Previously, this was only possible for Allow rules.
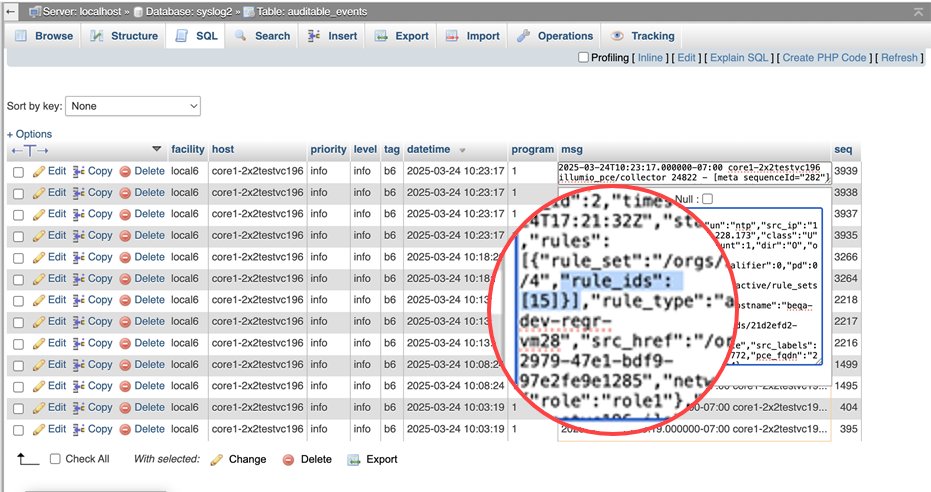
Rule IDs now included in Syslog
To help you trace and investigate traffic flows, each traffic flow entry in Syslog now includes the rule ID associated with the policy decision of the flow. This provides an explicit reference to the rule that affected the flow's policy state.
Caution
For large customers with 10K+ messages per second, adding rule IDs to the syslog events will make the recorded data significantly larger.
To use this feature, perform these steps:
Enable Rule Hit Count on the PCE and the VEN.
Enable the Rule ID feature as described in Showing Rule ID in Syslog in the Illumio REST API Guide.
Find the rule IDs in your syslog.
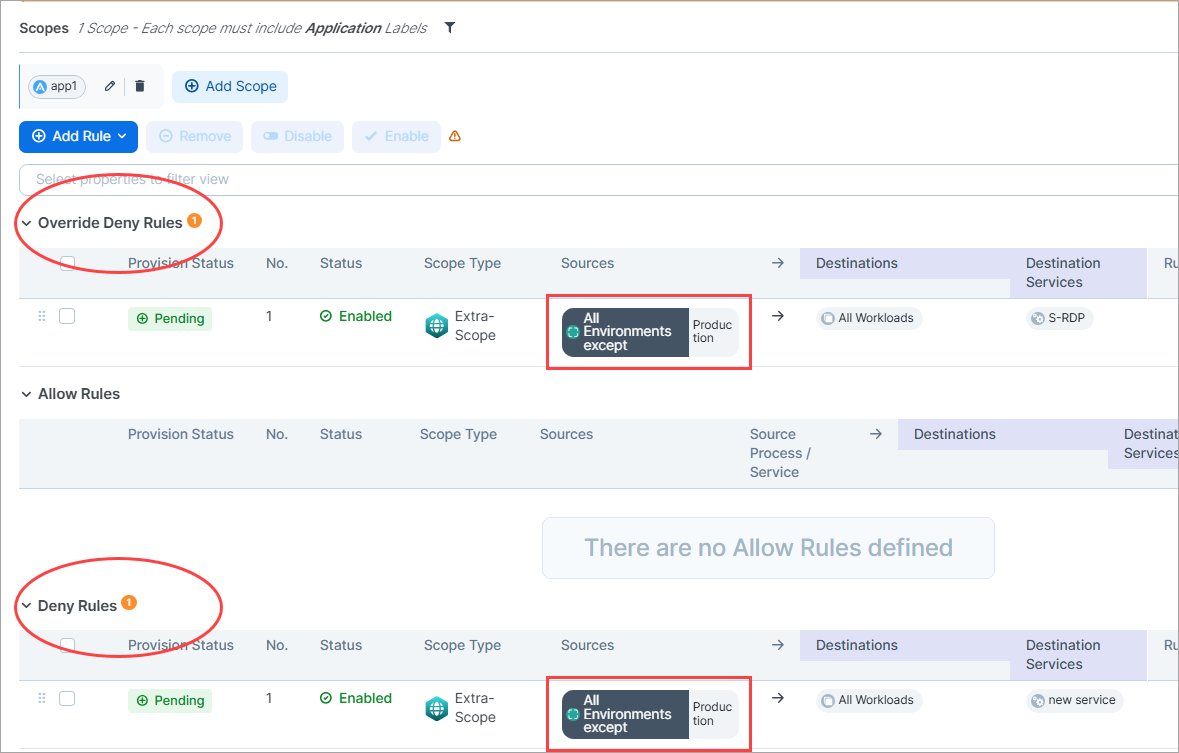
Label Exclusion now available for Deny and Override Deny rules
The ability to use an "all labels except. . ." approach when selecting labels for your rules is now available for Override Deny and Deny Rules. Previously, this feature was only available for Allow rules.
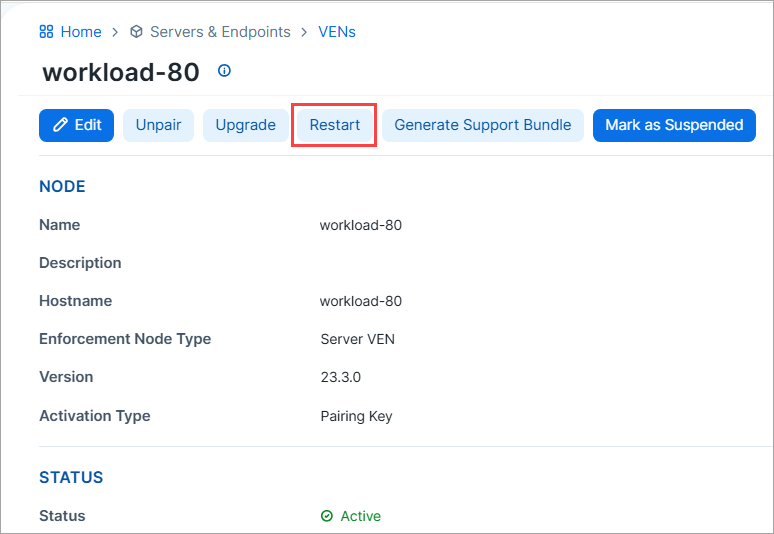
VEN Remote Restart
You can now restart a VEN directly from the PCE without physical access to the workload. Remote Restart is similar to other VEN operations that you can initiate from the PCE, such as unpairing and upgrading. For details, see Remote VEN Restart.
Note
The Restart button is grayed out if the VEN is Suspended or Offline.
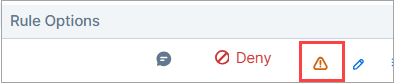
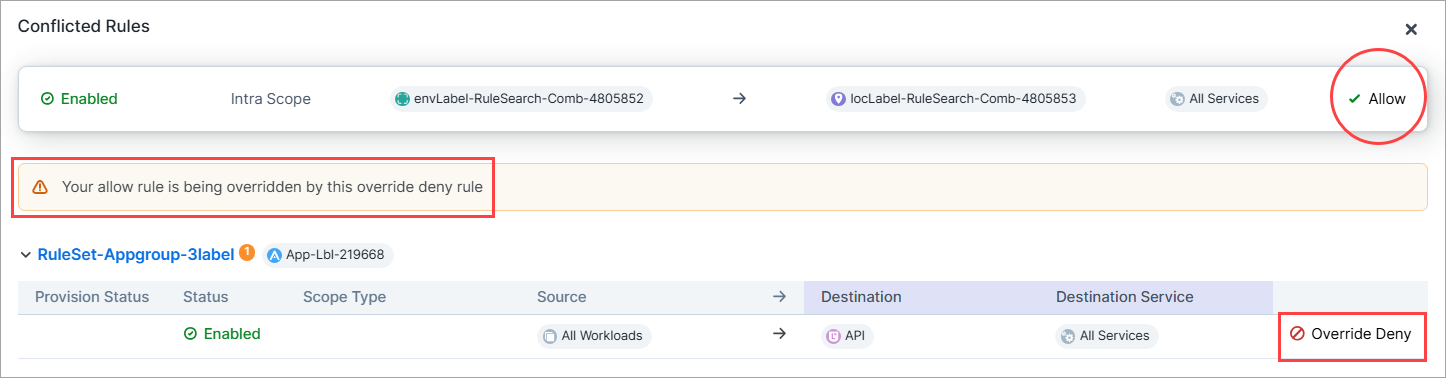
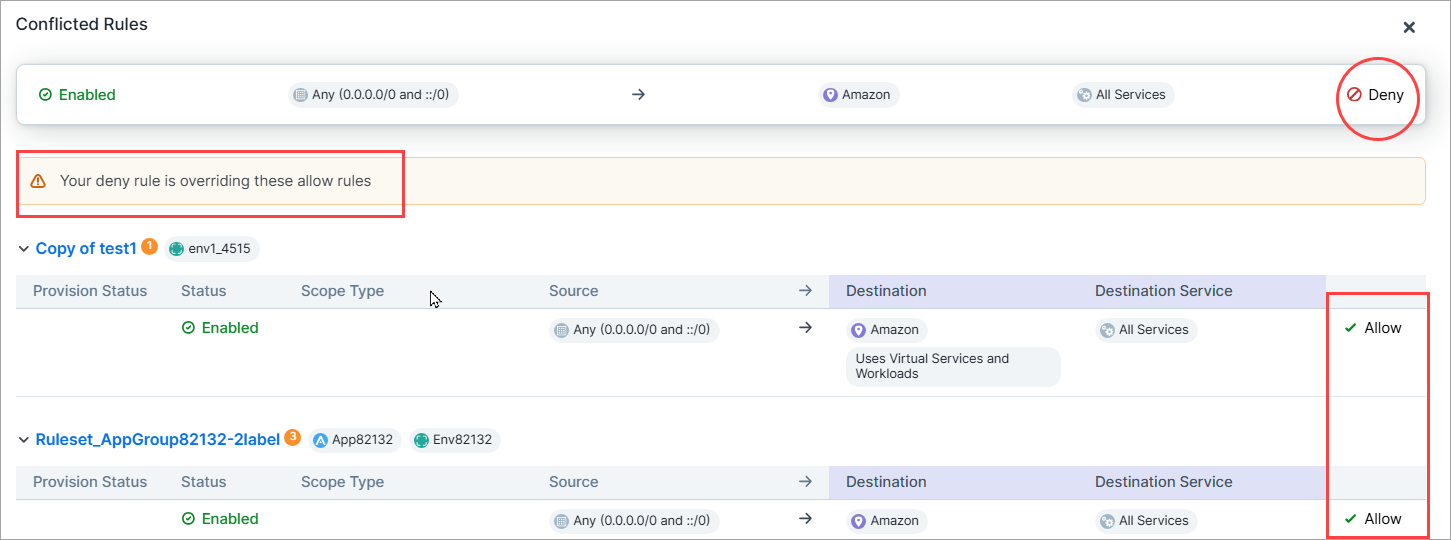
Conflicted Rules panel
You are now alerted when rules are in conflict with one or more other rules in the same or another policy in your organization. Click the yellow icon to display a panel with the conflict details and use the information to perform housekeeping on your policy or troubleshoot unexpected policy behavior.
Rules are in conflict when:
Traffic allowed by an Allow rule in your policy is overridden by an Override Deny rule in the same or another policy in your organization. Result: traffic is denied, which you may or may not have intended.
Traffic denied by a Deny rule in your policy is overridden by an Allow rule in the same or another policy in your organization. Result: traffic is allowed, which you may or may not have intended.
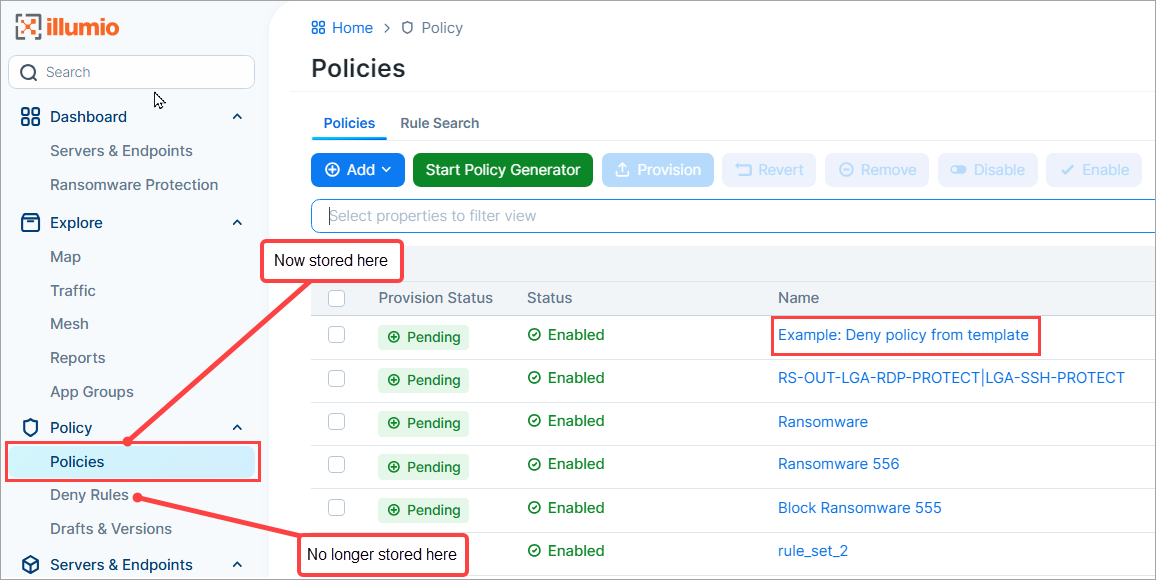
Deny Rules created from a Template now appear in the Policies page
When you add a deny rule from a template, it's now placed in the Policies list page, not the Deny Rules page as before.
Note
Although the stand-alone Deny Rules page still appears in the left navigation, Illumio plans to deprecate it in a future release. If your Core instance was upgraded to release 25.2.10 or later, Illumio recommends that you migrate your Deny rules from the Deny Rules page to the Policies page and add and manage Deny Rules from the Policies page from now on.
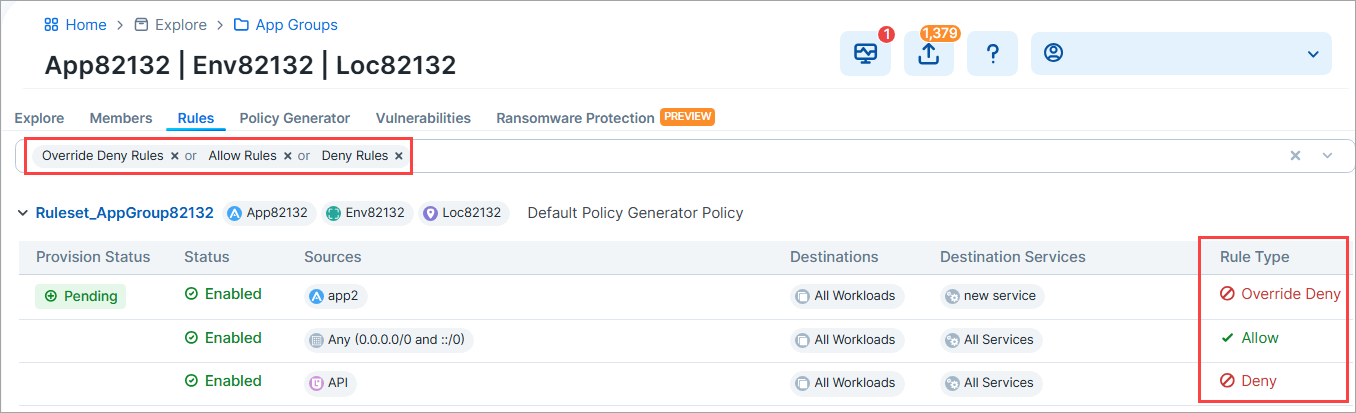
Support for searching App Groups by Deny and Override Deny rules
You can now search for Deny and Override Deny rules from an App Group's details page. Previously, you could only search for App Groups containing Allow rules from this page.
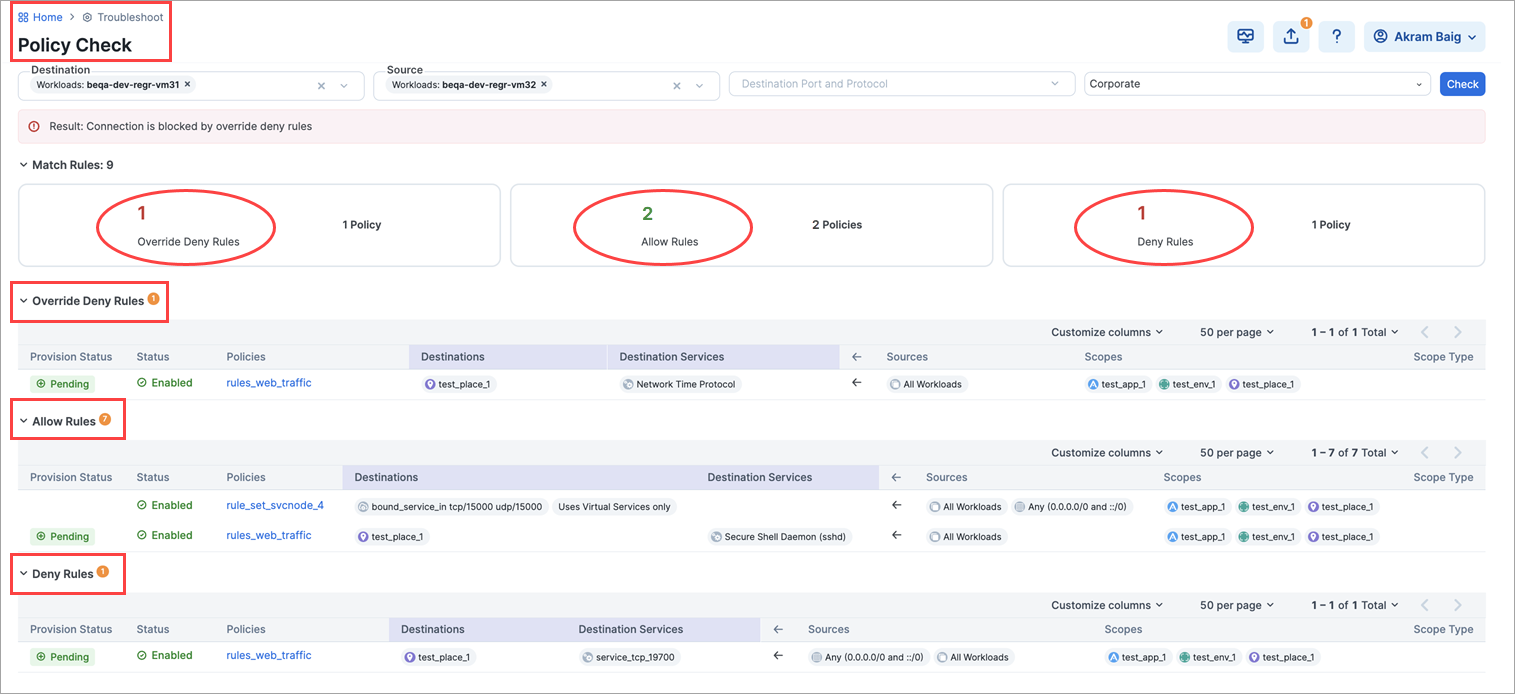
Support for checking policy by Deny and Override Deny rules
Beginning with this release, the policy check feature (Troubleshooting > Policy Check) checks for policies that include Deny and Override Deny rules. Previously, this featured only checked policies containing Allow rules.
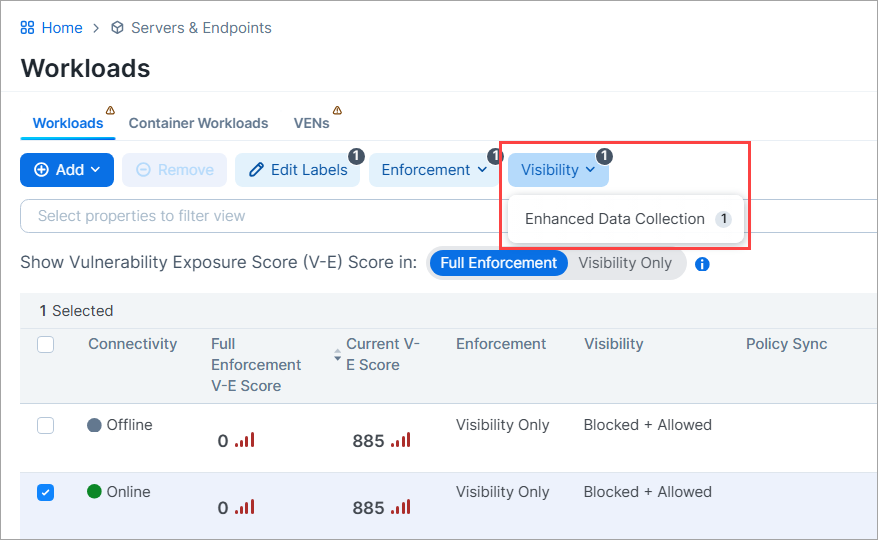
Support for Enhanced Data Collection in all enforcement modes
You can now enable the Enhanced Data Collection option in any enforcement mode, not just Full Enforcement as before. Enhanced Data Collection allows the VEN to log byte counts and connection details for Allowed, Blocked, and Potentially Blocked traffic.
New APIs in 25.21
New Common Schemas
common deny_rule_actor: The Enforcement Boundary Actor schema describes the actors as workloads and defines the exclusions.
{ "$schema": "http://json-schema.org/draft-04/schema#", "description": "Enforcement boundary actor", "type": "array", "minItems": 1, "items": { "type": "object", "additionalProperties": false, "properties": { "actors": { "description": "Rule actors are all workloads ('ams')", "type": "string", "enum": ["ams"] }, "exclusion": { "description": "Boolean to specify whether or not the actor is an exclusion - only for labels and label groups", "type": "boolean", "expose_to": ["end_user_experimental"], "default": false }, "label": { "$ref": "href_object.schema.json" }, "label_group": { "$ref": "href_object.schema.json" }, "ip_list": { "$ref": "href_object.schema.json" }, "workload": { "expose_to": ["end_user_private_perm"], "$ref": "href_object.schema.json" } } } }common deny_rules_get: For deny_rules, this gets the timestamps when the Enforcement Boundary was created, updated, and deleted. It also defines the users who originally created, updated, and deleted the boundary.
{ "$schema": "http://json-schema.org/draft-04/schema#", "description": "Enforcement boundary", "type": "object", "required": ["href", "providers", "destinations", "ingress_services"], "expose_to": ["end_user_private_perm"], "_comment": "Don't set additionalProperties:false here as it collides with usage in allOf, set that in the schema that references this one instead.", "properties": { "created_at": { "description": "Timestamp when this Enforcement Boundary was first created", "type": "string", "format": "date-time" }, "updated_at": { "description": "Timestamp when this Enforcement Boundary was last updated", "type": "string", "format": "date-time" }, "deleted_at": { "description": "Timestamp when this Enforcement Boundary was deleted", "type": ["string", "null"], "format": "date-time" }, "created_by": { "type": ["object", "null"], "required": ["href"], "properties": { "href": { "description": "User who originally created this Enforcement Boundary", "type": "string" } } }, "updated_by": { "type": ["object", "null"], "required": ["href"], "properties": { "href": { "description": "User who last updated this Enforcement Boundary", "type": "string" } } }, "deleted_by": { "type": ["object", "null"], "required": ["href"], "properties": { "href": { "description": "User who deleted this Enforcement Boundary", "type": "string" } } }, "update_type": { "$ref": "../common/sec_policy_update_type.schema.json" }, "href": { "description": "The job URI.", "type": "string" }, "providers": { "$ref": "deny_rule_actor.schema.json" }, "destinations": { "$ref": "deny_rule_actor.schema.json" }, "ingress_services": { "$ref": "sec_rule_ingress_services.schema.json" }, "egress_services": { "$ref": "sec_rule_egress_services.schema.json" }, "caps": { "$ref": "../common/entity_caps.schema.json" }, "enabled": { "description": "Enabled flag", "type": "boolean" }, "description": { "description": "Description", "type": ["string", "null"] }, "network_type": { "$ref": "../common/rule_network_type.schema.json" }, "override": { "description": "When true, the deny rule will override and take precedence over other user defined allow rules.", "default": false, "type": "boolean" }, "unscoped_destinations": { "description": "Set the scope for rule destinations to All", "type": "boolean" } } }common rule_set: Parent Rule Set of a Rule.
{ "$schema": "http://json-schema.org/draft-04/schema#", "description": "Enforcement boundary", "type": "object", "required": ["href", "providers", "destinations", "ingress_services"], "expose_to": ["end_user_private_perm"], "_comment": "Don't set additionalProperties:false here as it collides with usage in allOf, set that in the schema that references this one instead.", "properties": { "created_at": { "description": "Timestamp when this Enforcement Boundary was first created", "type": "string", "format": "date-time" }, "updated_at": { "description": "Timestamp when this Enforcement Boundary was last updated", "type": "string", "format": "date-time" }, "deleted_at": { "description": "Timestamp when this Enforcement Boundary was deleted", "type": ["string", "null"], "format": "date-time" }, "created_by": { "type": ["object", "null"], "required": ["href"], "properties": { "href": { "description": "User who originally created this Enforcement Boundary", "type": "string" } } }, "updated_by": { "type": ["object", "null"], "required": ["href"], "properties": { "href": { "description": "User who last updated this Enforcement Boundary", "type": "string" } } }, "deleted_by": { "type": ["object", "null"], "required": ["href"], "properties": { "href": { "description": "User who deleted this Enforcement Boundary", "type": "string" } } }, "update_type": { "$ref": "../common/sec_policy_update_type.schema.json" }, "href": { "description": "The job URI.", "type": "string" }, "providers": { "$ref": "deny_rule_actor.schema.json" }, "destinations": { "$ref": "deny_rule_actor.schema.json" }, "ingress_services": { "$ref": "sec_rule_ingress_services.schema.json" }, "egress_services": { "$ref": "sec_rule_egress_services.schema.json" }, "caps": { "$ref": "../common/entity_caps.schema.json" }, "enabled": { "description": "Enabled flag", "type": "boolean" }, "description": { "description": "Description", "type": ["string", "null"] }, "network_type": { "$ref": "../common/rule_network_type.schema.json" }, "override": { "description": "When true, the deny rule will override and take precedence over other user defined allow rules.", "default": false, "type": "boolean" }, "unscoped_destinations": { "description": "Set the scope for rule destinations to All", "type": "boolean" } } }common sec_rule_egress_services: Array of objects.
{ "$schema": "http://json-schema.org/draft-04/schema#", "description": "Array of objects", "type": "array", "items": { "type": "object", "$ref": "../common/href_object.schema.json" } }common sec_rules_get: For sec_rules, this gets the timestamps when the Enforcement Boundary was created, updated, and deleted. It also defines the users who originally created, updated, and deleted the boundary.
{ "$schema": "http://json-schema.org/draft-04/schema#", "description": "Enforcement boundary", "type": "object", "required": ["href", "providers", "destinations", "ingress_services"], "expose_to": ["end_user_private_perm"], "_comment": "Don't set additionalProperties:false here as it collides with usage in allOf, set that in the schema that references this one instead.", "properties": { "created_at": { "description": "Timestamp when record was first created", "type": "string", "format": "date-time" }, "updated_at": { "description": "Timestamp when record was last updated", "type": "string", "format": "date-time" }, "deleted_at": { "description": "Timestamp when record was deleted", "type": ["string", "null"], "format": "date-time" }, "created_by": { "type": "object", "properties": { "username": { "description": "The username which created this record", "type": "string" } } }, "updated_by": { "type": "object", "properties": { "username": { "description": "The username which last updated this record", "type": "string" } } }, "deleted_by": { "type": ["object", "null" ], "properties": { "username": { "description": "The username which deleted this record", "type": "string" } } }, "update_type": { "description": "Type of update", "oneOf": [ { "type": "null" }, { "type": "string", "enum": ["create", "update", "delete"] } ] }, "update_label": { "description": "Type of update", "oneOf": [ { "type": "null" }, { "type": "string", "enum": ["create", "update", "delete"] } ] }, "href": { "description": "URI of object", "type": "string" }, "enabled": { "description": "Enabled flag", "type": "boolean" }, "description": { "description": "Description", "type": ["string", "null"] }, "ingress_services": { "$ref": "sec_rule_ingress_services.schema.json" }, "egress_services": { "$ref": "sec_rule_egress_services.schema.json" }, "resolve_labels_as": { "$ref": "sec_rule_resolve_labels_as.schema.json" }, "sec_connect": { "description": "Whether a secure connection is established", "type": "boolean" }, "stateless": { "expose_to": ["end_user_experimental"], "description": "Whether packet filtering is stateless for the rule", "type": "boolean" }, "machine_auth": { "expose_to": ["end_user_experimental"], "description": "Whether machine authentication is enabled", "type": "boolean" }, "providers": { "$ref": "sec_policy_rule_sets_sec_rules_providers_get.schema.json" }, "destinations": { "$ref": "sec_policy_rule_sets_sec_rules_destinations_get.schema.json" }, "consuming_security_principals": { "$ref": "consuming_security_principals_get.schema.json" }, "unscoped_destinations": { "description": "Set the scope for rule destinations to All", "type": "boolean" }, "use_workload_subnets": { "$ref": "sec_rule_use_workload_subnets.schema.json" }, "rule_set": { "$ref": "../common/rule_set.schema.json" }, "log_flow": { "description": "If false, the VEN will not log any traffic that matches this flow.", "type": "boolean", "expose_to": ["end_user_private_transitional"] }, "network_type": { "$ref": "../common/rule_network_type.schema.json" } } }